A different topic for today in relation to Cyber Security and system security because it is very important to know security as well, rather than just knowing how to make attacks.
Today in this guide we will see how we can protect our Database and confidential files from a malicious hacker with an attack SQL INJECTION into a POST method. For those who want to know how such an attack is carried out, there are some guides. But let's get to our topic.
I will show you the example in my own manual website which runs locally with the help of xampp. So let me say that I opened an apache server and a phpmyadmin from behind for database. (db = egasiasxol, host = localhost, table = users, columns = username-password). You can see the html and php codes below.
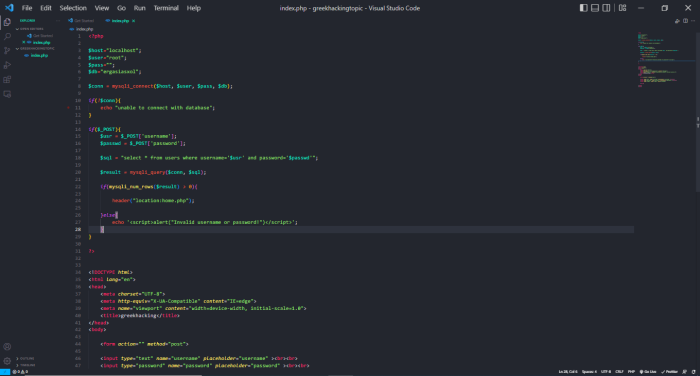
What do we have in code;
In the code we have simple inputs in the html which are textboxes for the user to enter the username and password and another input which is type=submit i.e. a button so that the connection is made in case the data is correct ( All this is in a form in which we use method=post.
In the php code we allow the database to communicate with it. What does this mean; to read through the database the username and password in order to check whether the information is correct for the user to gain access to the so-called Dashboard, or not.
$sql = "select * from users where username='$user' and password='$passwd'";So let's see what's wrong with this code. The answer is that there is no error, just that there are no filters and thus the hacker can gain access to the system because our code has not filtered the Symbols that can be used (' etc.).
So let's go see Live the attack and also the security. First we'll start with the attack.
We open Burpsuite on our Linux, we also open a browser in which we have correctly set the proxies to communicate with burp. proxy -> intercept
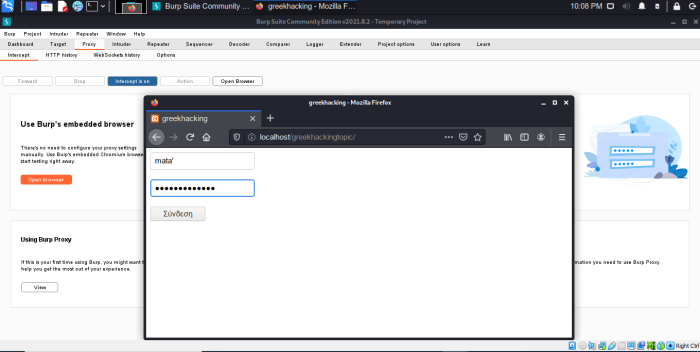
Make sure the intercept is “ON”. So we put some random credentials with an "ear" at the end in both username and password. (eg username', password'). After we press it button connection burpsuite will show us some results with POST method.
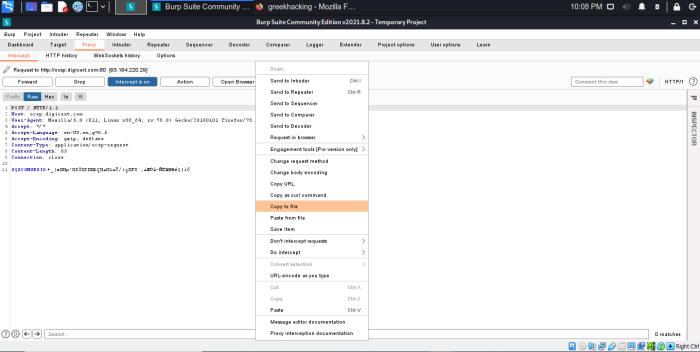
Right-click on the results and select copy to file to save them to a file.
After we press-name the file (in our case grhacking) and press save so that it saves the file in the path we have chosen, we open sqlmap which is an incredible tool in my opinion which will help us to automatically do the sql injection attack. We open sqlmap and write “sqlmap -r (for the file) grhacking –dbs (to find the database)
sqlmap -r grhacking --dbs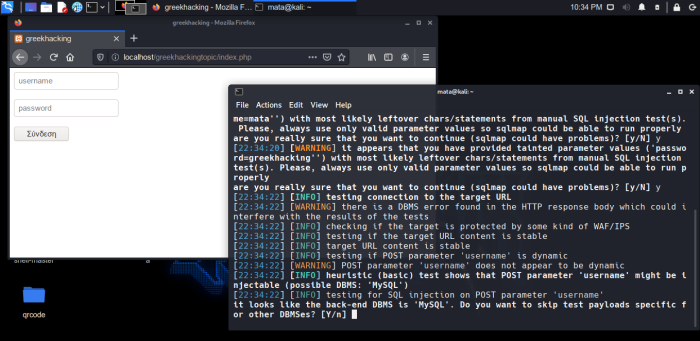
POST parameter 'username' might be injectable (Possible mysql Base). For those of you who didn't understand, he found our base vulnerable, something which is very important.
Why; let's see below.
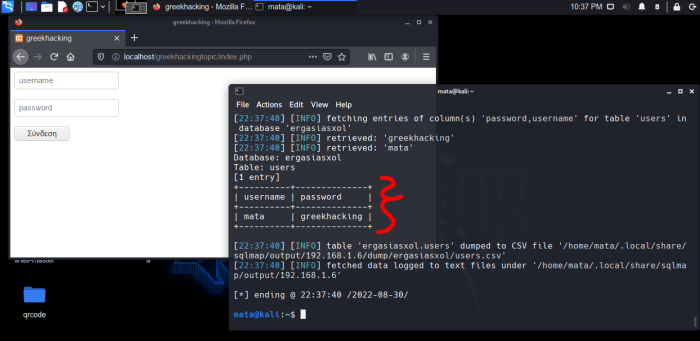
So after we write some commands to find the appropriate ones tables and columns so that he can dump them, we see the results... With which the hacker will be happy but we will cry... because with these elements he gets access to the dashboard. username: mata , password = greekhacking
So let's see how we can protect our personal data from this attack. Let's go back to the code I showed in the previous screenshot, and put the filters. I will explain after you see the picture.
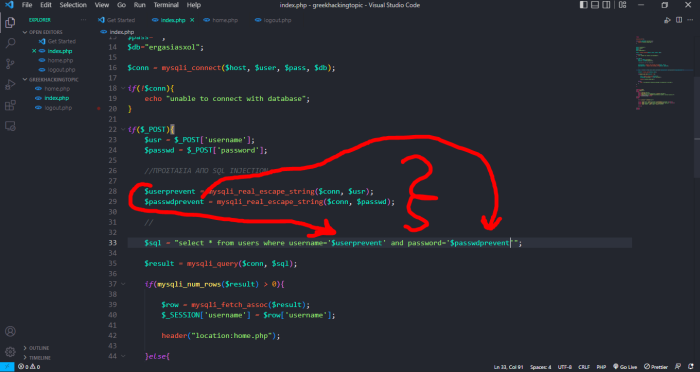
Where I have put the slashes is the so-called comment which the code does not see. So we skip it. We create a new variable which is $userprevent and inside it we put the mysqli_real_escape_string filter. In parentheses are the connection that I have defined as $conn and the $usr that I have defined for the POST of the username above “$usr = $_POST['username'];”
We do the same for the password.
So after this is done, the next step is to apply the variables to make the filters work to protect our base. we apply them by going to the $sql variable that we have defined for the communication of the elements with the POST method to the textboxes that the user will log in. I have also shown you this with darts. (You can see the differences in the above screenshot I showed with code and in this screenshot).
So let's attack again to see what happens again.
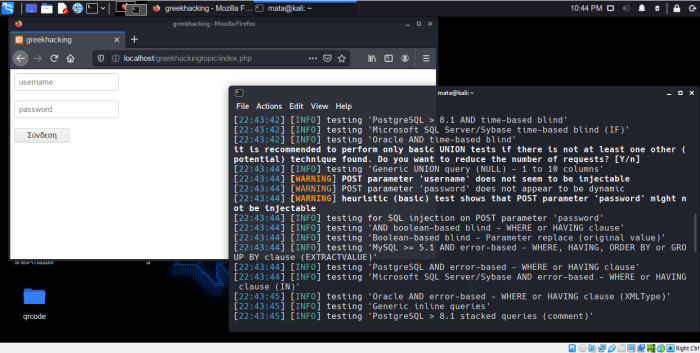
As we can see the sqlmap cannot respond because we have now put filters and it throws us POST parameter does not seem to be injectable. [WARNING].
And of course below it throws us a CRITICAL error and rejects us.
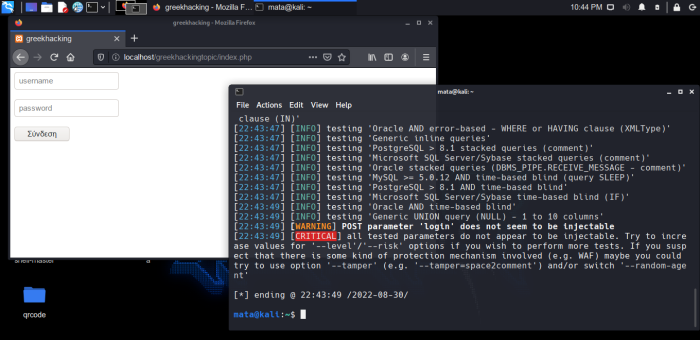
This was the guide on how you can protect yourself from a SQL INJECTION attack on a POST method.
At some point I will also write about how to protect yourself from a SQL INJECTION attack on the GET method. Thanks to those who read to the end, I hope you learned something from me and I hope I wrote and showed it as thoroughly as I could. Good Hacking (ethical of course). : )
Article author: Vassilis Burandanis





