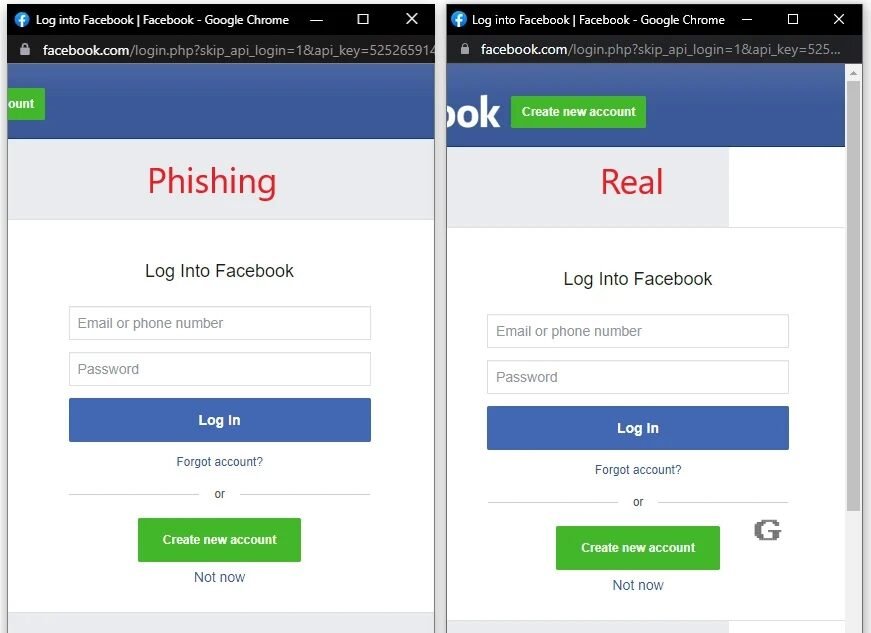
A phishing kit has just been released that allows malicious users to create credible and effective phishing logins using fake Chrome browser windows.

When you link to sites, you also see the option to connect with Google, Microsoft, Apple, Twitter or even Steam.
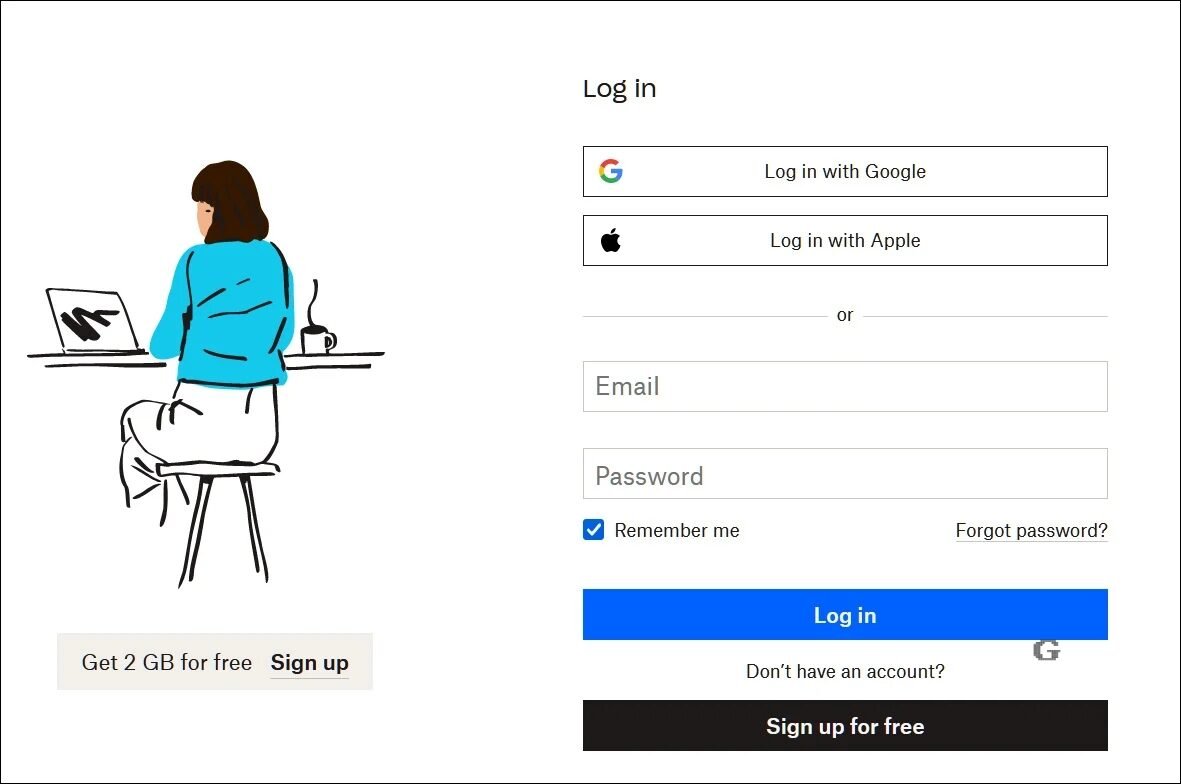
For example, the login form for DropBox lets you login using a account of Apple or Google, as shown below.
With the new method, when you click the sign-in with Google or Apple buttons, an identical browser window will appear with a single-sign-on (SSO), which prompts you to enter your credentials and sign in to the account.
Malicious users used to try to create these fake SSO windows using HTML, CSS, and JavaScript, but there was usually something that made them look suspicious.
Browser in the Browser attacks
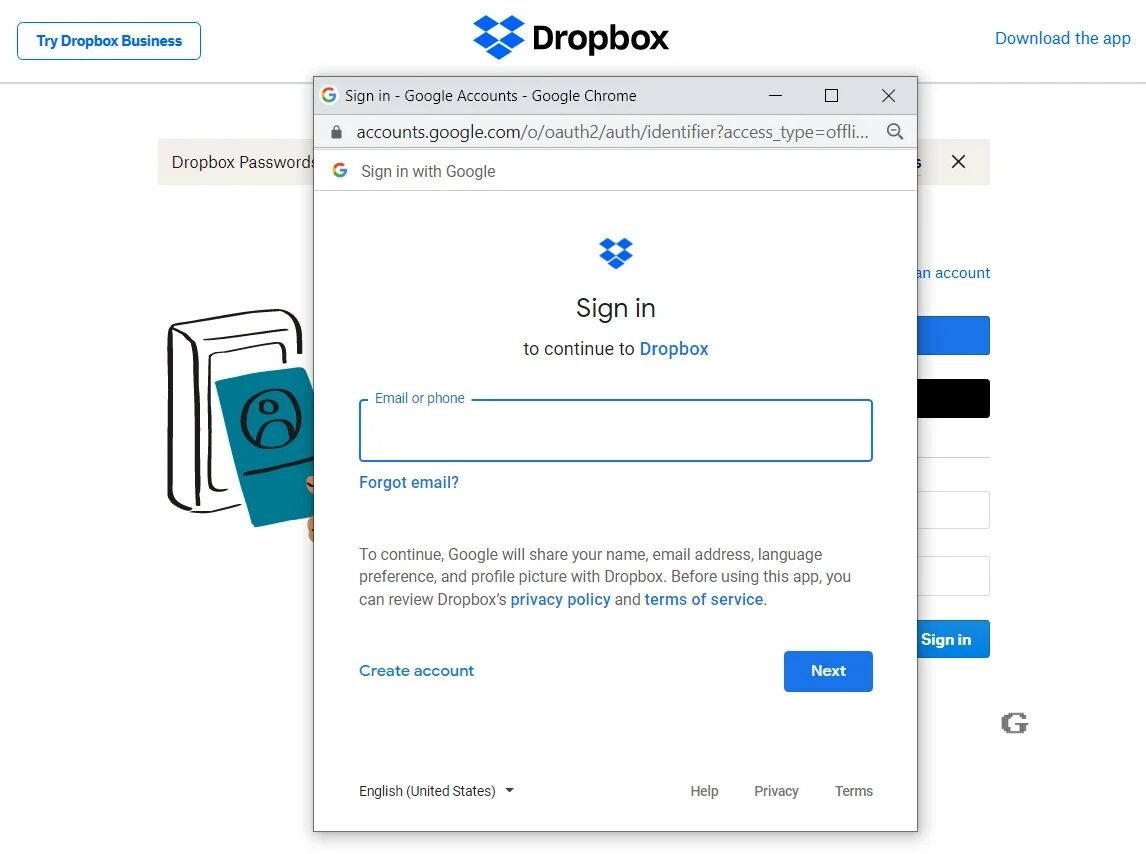
Here comes the new “Browser in the Browser (BitB) Attack” method that uses pre-made templates to creation fake but realistic Chrome pop-ups that include custom URLs and titles that can be used in phishing attacks.
This attack creates fake browser windows inside the actual browser windows (Browser in the Browser) to create compelling phishing attacks.
Browser attack templates are already in place in GitHub. Includes Google Chrome windows for Windows and Mac with dark and light variants.
Attackers can simply download the templates, edit them to contain the desired one address URL, the window title, and then use an iframe to display the login form.
Kuba Gretzky, the creator of the Evilginx phishing toolkit, tested the new method and said it works perfectly with the Evilginx platform, which means it can be adapted to steal 2FA keys during phishing attacks.
So in the next period it would be good to be more careful with each login form. With the pre-built templates for fake Chrome windows, very convincing login forms for phishing will appear.






Good evening George. You are obviously talking about 2FA code theft from applications that generate 2FA codes. We're not talking about passwords being sent to our cell phones, are we? This is only done via SIM swapping as far as I know.
look
In the end it is much simpler than I imagined. The fake page just asks you for the 2FA key, as soon as you receive it you enter it in the fake page you have entered and the username and password and the hacker has everything he needs!
Thanks!
Can we find somewhere in detail if it is true that it can actually steal 2FA keys ???
The article mentions it briefly, but in a search I made on the subject I did not find anything related to the 2FA keys
need tools to steal 2fa, the Evilginx phishing toolkit for example already steals 2fa The new technique made it easier