A recent operation has been launched by hackers in their attempt to steal codes from Steam. They use the newest Browser-in-the-Browser phishing technique, which is quite difficult to detect at first glance.

The way
The Browser-in-the-Browser (BitB) technique that we spoke to you in March 2022, is a modern attack method that involves creating fake windows of your browser, inside the active window, making it appear as a normal pop-up login page for a targeted login service.
Hackers using the BitB phishing method create fake login forms for Steam, Microsoft, Google and any other service.
Steam campaign
The Group-IB reports that the phishing you use in the observed Steam campaign is not widely available on forums piracyor on dark web markets. Instead, it is used by hackers through Discord or Telegram channels to coordinate them attacks their.
Potential victims are targeted with direct messages on Steam, inviting them to join a team for LoL, CS, Dota 2 or PUBG tournaments.
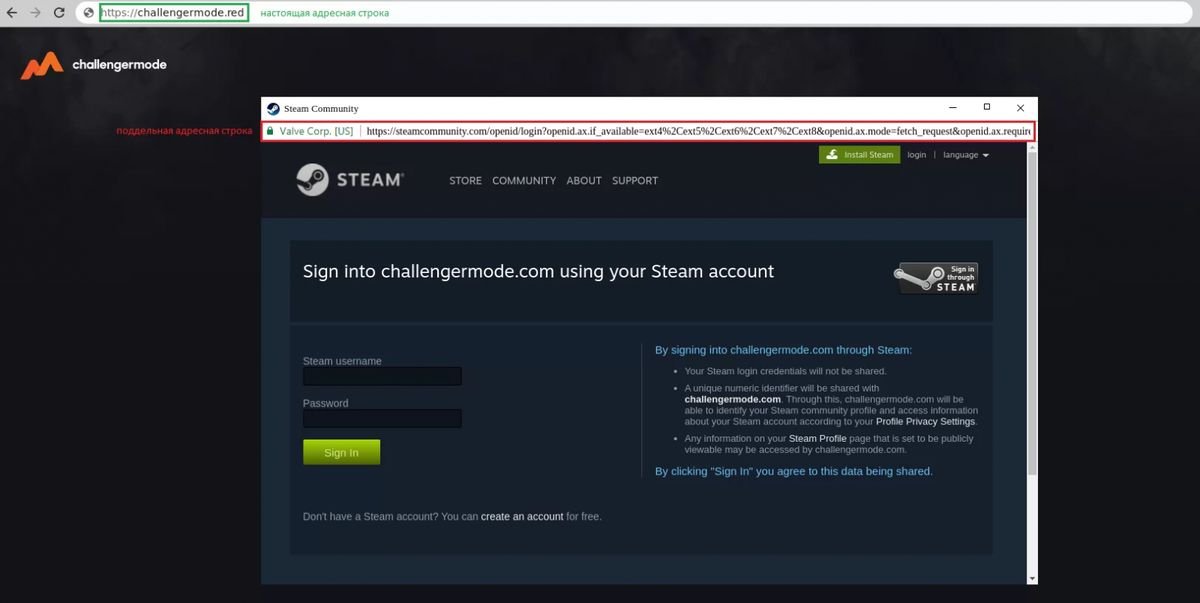
To join a team and play in a competition, guests are required to log in through their Steam account. However, the new Steam login page window is not a real browser window overlaid on the existing website, but rather a fake window created on the current page, which makes it very difficult to detect as a phishing attack.
The landing pages even support 27 languages by detecting the language from the victim's browser preferences and loading the correct one.
Once the victim enters their credentials, a new form asks them to enter their 2FA code. If the second step is unsuccessful, an error message is displayed.
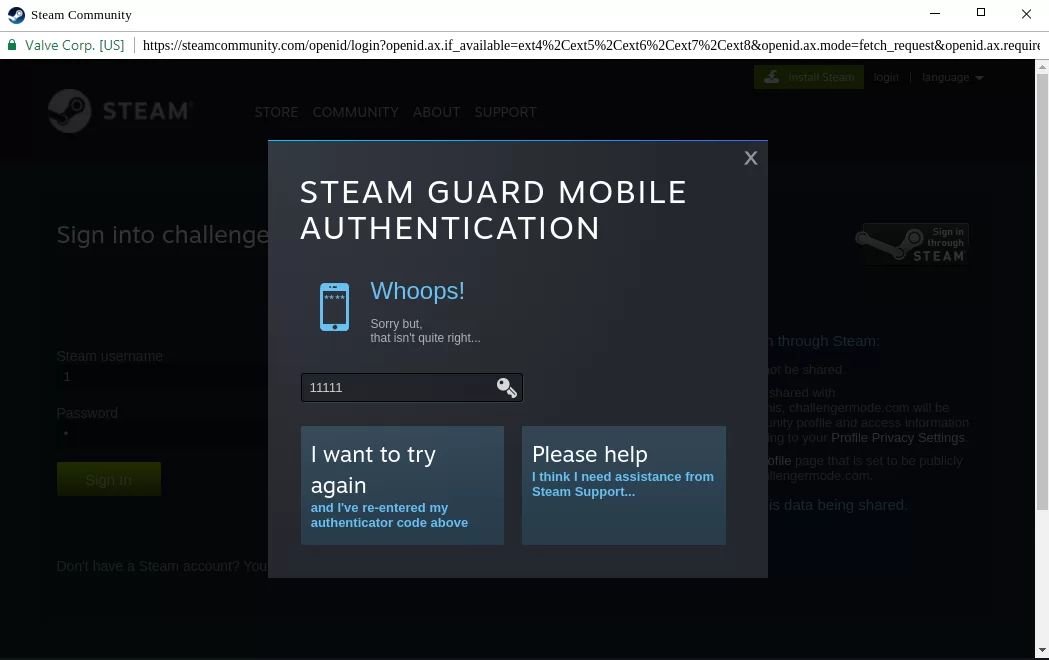
If the control again identity είναι επιτυχής, ο χρήστης ανακατευθύνεται συνήθως σε μια νόμιμη address, to minimize the chances of the victim realizing the fake window.
At this point, the victim's credentials have already been stolen and sent to the hackers. Criminals act quickly on stolen Steam accounts, changing passwords and email addresses to make it harder for victims to regain control of their accounts.
How to detect a BitB attack
In all BitB (browser) phishing cases, the URL in the phishing window is the same as the legitimate one, as hackers are free to display whatever they want since it is not browser window, but just to fake rendering it via Javascript.
The same goes for the SSL certificate lock symbol, which indicates an HTTPS connection, creating a false sense of security for victims.
Even worse, this phishing allows users to drag the fake window, minimize, maximize and close it, making it very difficult to detect it as a fake browser window in the browser.
As the technique requires JavaScript, aggressively blocking JS scripts will prevent the fake link from appearing. However, most people do not block Javascript scripts, as this would break many popular websites.
A good method of spotting the fake window is to try to move it out of bounds of the main browser window. If it cannot be moved to the surface work it's not a window.
Other ways of checking to detect BitB attacks are:
- Check if it opens one new window in the taskbar, assuming you've ungrouped programs on the Windows 10 taskbar. If there's no new window on the taskbar, then it's not a real window. Unfortunately, Windows 11 does not support unbundling at this time.
- Try to change the size of the window. If you can't, it's probably a fake browser window.
- The fake BiTB browser windows they will close if you minimize them.
In general, be very careful with direct messages you receive on Steam, Discord, or other game-related platforms, and avoid following links sent by users you don't know.





