A Chinese security researcher has discovered a new phishing attack that is almost impossible to detect and can fool even the most alert internet users.
The hacker says he can use a known vulnerability in Chrome browsers, Firefox and Opera to display fake domains of legitimate services such as Apple, Google, or Amazon. This can easily steal the credentials and other sensitive information of each user.
What did we know to date to protect against phishing attacks?
Σε γενικές γραμμές, έπρεπε να ελέγχουμε τη line διευθύνσεων ότα φορτωθεί η σελίδα και αν η connection is secured with HTTPS.
Of course, we also looked for other small details whether there are spelling mistakes, or imperfections in the design of the page. 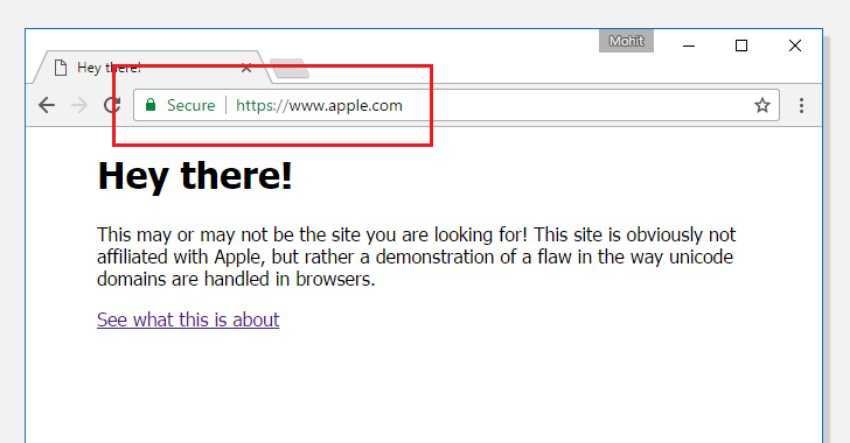
Η demo site (note: currently experiencing downtime due to high traffic), set up by Chinese security researcher Xudong Zheng, who discovered the attack seems to be genuine.
"It is impossible to identify a page as fake without carefully looking at the site's URL or SSL certificate," said Xudong Zheng.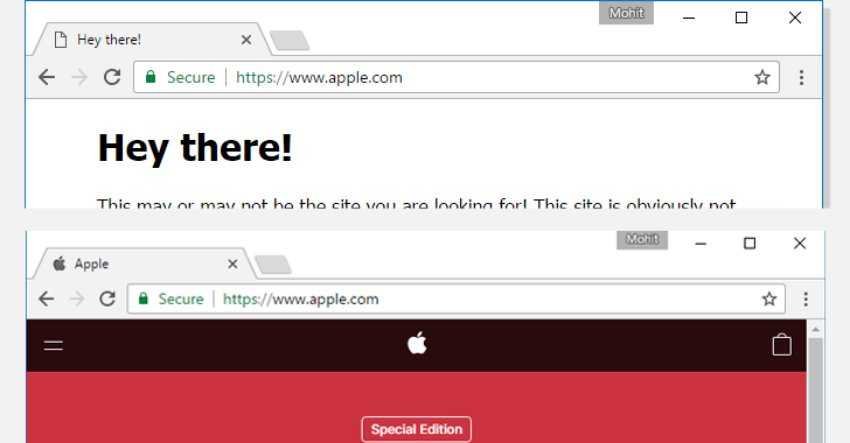
Although your web browser displays "apple.com" in the address bar with a secure SSL connection, the content of the page comes from another server (as shown in the image above).
There is also another website (PoC) created by Wordfence security experts to prove the vulnerability of browsers.
The "homography" attack has been known since 2001, but the Companies browsers didn't seem to fix the problem. It's a type of spoofing attack where a web page address looks legitimate, but isn't because a character or characters have been replaced with Unicode characters.
Many Unicode characters, which are alphabets, (Greek, Cyrillic, and Armenian) are used in the internationalized domains. Characters look the same as Latin, but are treated differently from computers as they completely change the web address.
For example, the Cyrillic Letter 'a' (U + 0430) and Latin 'a' (U + 0041) look the same but are treated differently from the browsers.
However, what appears in the url is the Cyrillic "a" which of course leads the browser to another address.
So the only "obvious" way to know if the page is fake is from the Certificate.
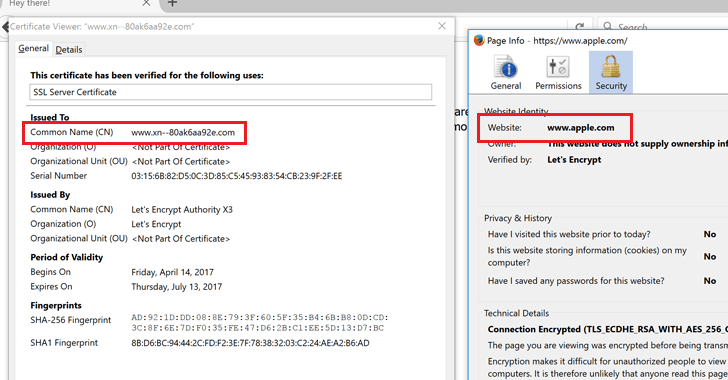
By default, many web browsers use "Punycode" encoding to display Unicode characters in the URL and to protect against such homogenous phishing attacks. Punycode is a special encoding used by the web browser to convert Unicode characters to ASCII (AZ, 0-9) characters supported by the Domain Names (IDNs) system.
Zheng reported vulnerability to the affected developers of browsers.
While the Mozilla Foundation is still looking for a solution, Google is reported to have already repaired the vulnerability in the Chrome Canary 59 experimental version. We expect a permanent solution with the release of Chrome Stable 58, which will be released later this month.
For you using Firefox, follow these steps to temporarily fix the problem:
Type about: config in the address bar and press enter. Promise to be good guys παιδιά
Type Punycode in the search bar.
The settings of the browser will display the parameter titled: network.IDN_show_punycode
Double click or right click and select change to change the value from false to true.
Unfortunately, there is no similar setting in Chrome or Opera.





