A malware named Racoon , which is relatively new to dark web forums, can extract sensitive data from around 60 apps.

In the deepest layers of the web one can find anything that has to do with malware. The market there is constantly changing and so malware that a few years ago was expensive, is now available for a modest price, compared to what they can offer and the very rich set of features they have. Racoon is also classified in this category. A malware that first appeared almost a year ago and quickly gained popularity due to its generous features and subsequent low price.
Είναι επίσης γνωστό και ως Legion ή Mohazo ή Racealer. Το κακόβουλο λογισμικό Racoon προωθήθηκε αρχικά μόνο σε ρωσόφωνα φόρουμ του Dark Web, αλλά σύντομα έκανε την είσοδό του και στον αγγλόφωνο χώρο. Πρωτοεμφανίστηκε τον Απρίλιο του 2019 και διανεμήθηκε ως μοντέλο MaaS (malware-as-a-service = κακόβουλο λογισμικό υπό ενοικίαση) για $ 75 / εβδteam ή $ 200 / μήνα.
With this money, attackers gain access to a Racoon management panel that allows them to customize it to their liking, access stolen data, and download the builds of malware.
This model is widely adopted today, because it opens the door to a larger number of customers who want to try their luck as cyber criminals, but many of whom do not have the appropriate technical knowledge, but thus can depreciate the business.
An analysis by CyberArk found that it is written in C ++ and is far from being a complex tool. However, it can steal sensitive and confidential information from nearly 60 programs (browsers, encryption wallets, e-mail, and FTP clients).
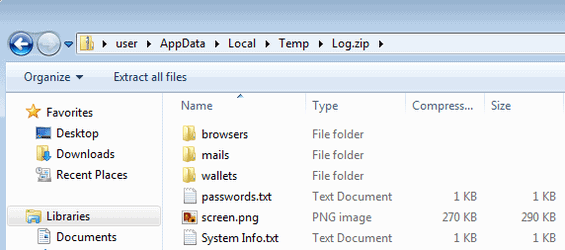
All popular browsers (Google Chrome, Mozilla Firefox, Microsoft Edge, Internet Explorer, Opera, Vivaldi, Waterfox, SeaMonkey, UC Browser) βρίσκονται στον κατάλογο των στόχων του, κλέβοντας τα cookies, το ιστορικό και πληροφορίες αυτόματης συμπλήρωσης.
Also in the spotlight are cryptocurrency applications such as Electrum, Ethereum, Exodus, Jaxx and Monero, in which it searches for wallet files in their default locations. However, Racoon can also scan the system to grab wallet.dat files no matter where they are stored.
In the email category, Racoon searches for data in at least Thunderbird, Outlook and Foxmail. In a report today, CyberArk researchers report that this "information thief" uses the following process to steal the data: it locates and copies the files with the sensitive information, applies decryption routines to them, and then puts the information into a text file. After fulfilling all its stealth capabilities, it bundles all the files it wrote to the temp folder into a zip file called Log.zip. It then sends the Log.zip to a C&C server.
Malware add-ons include system detail collection (operating system version and architecture, language, hardware information, list of installed applications).
Attackers can also customize the Raccoon configuration file to take pictures of the screens of infected systems. In addition, the malware can act as a dropper for other malicious files, effectively turning it into a stage-one attack tool.
Like all popular malware, Racoon is actively improving with fixes for various issues, new features and capabilities.
Analyzing a sample, the researchers noticed that they have released new versions that extend support for targeted applications, adding FileZilla and UC Browser. In addition, the option to encrypt the malware directly from the admin panel and download it in DLL format has been added.
Racoon does not use special techniques to extract information from targeted programs, but it is one of the most popular infostealers in cybercrime forums. THE Recorded Future notes in a report in July 2019 that it had the best-selling malware in the underground economy.
Three months later, the Cybereason researchers announced that the malware enjoyed positive reviews from the community, as many cybercriminals praised and applauded it, but with the biggest names of them criticizing it for its simplicity and lack of features in tools of the same type.
However, despite the simplicity of Racoon, it has spread to hundreds of thousands of computers around the world. This means that technical features are not necessarily what make attackers choose a malicious tool, but essentially a good balance between price, accessibility and capabilities.





