The gang running the LocKBit ransomware has apologized for encrypting their computers of SickKids Children's Hospital in Canada and sent them the decryption code.

The Hospital for Sick Children (SickKids) is a research hospital in Toronto that focuses on providing health care to sick children. On December 18, the hospital suffered a ransomware attack that affected internal and corporate systems, the hospital's phone lines and website.
While the attack only encrypted a few systems, SickKids said the incident caused delays in receiving lab and imaging results and resulted in longer patient wait times.
On December 29, SickKids announced that it had restored 50% of the systems I prioritized, including those causing diagnostic delays or treatments.
Two days after SickKids' last announcement, and 13 days since the attack, the LockBit ransomware gang apologized for the said hospital attack and provided him with a decryptor without demanding a ransom.
The text of the extortionists stated the following: “We formally apologize for the attack on sikkids.ca and return the decryptor for free. The partner who attacked this hospital violated our rules, has been banned and is no longer in our partner program."
Ransomware as a business
The LockBit function runs as Ransomware-as-a-Service, that is, it is a whole business with operators and affiliates.
The operators where they are and those who have made the ransomware keep the decryption keys (or encryptors) and the websites where you can find them and the partners or members of the “company” break into the victims' networks, steal data and encrypt the devices.
As part of this agreement, LockBit operators keep about 20% of all ransoms and the rest goes to the partners who have done all the work.
While ransomware operators allow their partners to encrypt pharmaceutical companies, dentists and plastic surgeons, they prohibit them from encrypting “medical institutions” where attacks could lead to death.
It specifically refers to the operating policies of the ransomware (the link only opens with tor: lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd.onion/rules ):
“Encryption of institutions is prohibited where damage to archives could lead to death, such as cardiac centers, neurosurgery departments, maternity hospitals and the like, that is, those institutions where surgical operations can be performed on high-tech equipment using computers.” .
So the attack on the hospital was considered high risk and they sent the keys back, but it doesn't explain why LockBit didn't provide a decryptor sooner, and it took 13 days where patient care was affected for so long.
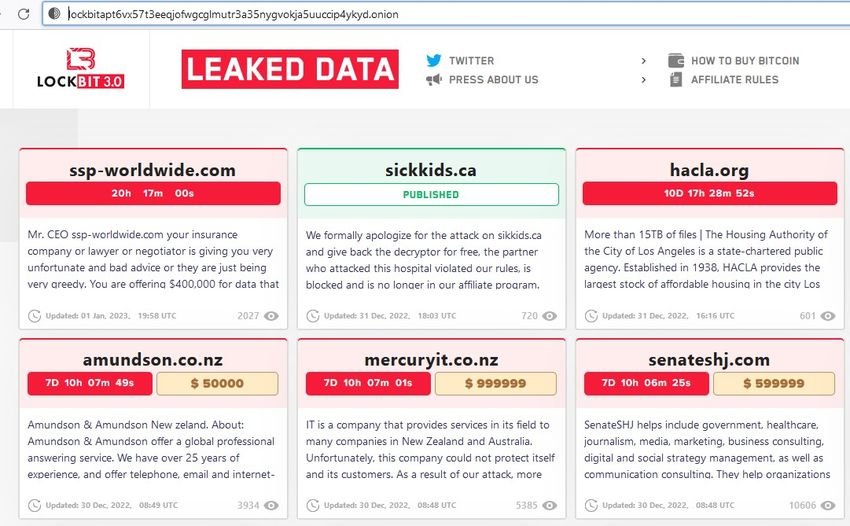
Let's not laugh, extortionists are illegal and no angels. Apparently they saw something and got scared. After all, LockBit has a history of encrypting hospitals and not providing encryptors, as seen in its attack on the Center Hospitalier Sud Francilien (CHSF) in France, where a $10 million ransom was demanded and patient data eventually leaked.
And the attack on the French hospital led to the referral of patients to other medical centers and the postponement of surgeries, which could lead to significant risk to patients.
On the other hand, this is not the first time that a ransomware gang has provided a free decryptor to a healthcare organization. In May 2021, the Conti Ransomware operation provided a free decryptor to Ireland's national health service, the HSE, after facing increased pressure from international law enforcement.





