Ransim is a simulator of Windows devices that simulates the attacks of ten ransomware families on your system.
The ransomware is no doubt a relatively new category of threats that has gained prominence in a very short space of time.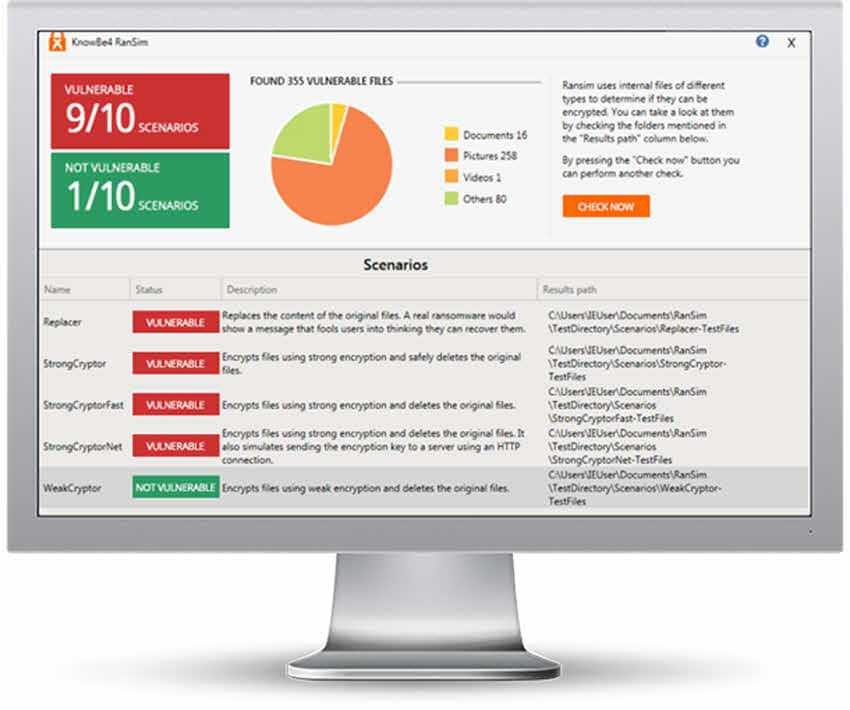
Security companies have begun to release protection tools from ransomware, but no one knows whether they are effective, or how long they will stay as the malware code continually changes.
So RanSim is designed to simulate attacks on a computer system, which will help you find out if your system is protected by ten common ransomware attacks.
If you try to download Ransomware Simulator “RanSim” 1.0.2.2 from official webpage you will be asked to register before being given the option λήψηs. We downloaded it for you, and uploaded it to GDrive. So you can download it without giving your details.
Application developers suggest keeping your security software closed as the simulation will look suspicious and may block RanSim. The new Premium Malwarebytes for example blocks the execution of RanSim's actions.
RanSim is very easy to use. Provides information about the ransomware test scripts and just pressing one button you can start the test.
Η essay it won't take more than a minute. The program will download the test files from the Internet, but will not harm your files on the local system. It will list the files and display information about the vulnerabilities it discovered.
The application checks for the following ransomware:
- InsideCryptor — encrypts files using strong encryption and overwrites most of the content of the original files with the encrypted data.
- LockyVariant - simulates the behavior of a recent version of Locky ransomware.
- Mover - Encrypts files in a different folder using strong encryption and safely deletes the original files.
- Replacer - Replaces the content of the original files. A real ransomware would show a message that fools users into thinking they can recover them.
- Streamer — Encrypts files and writes data into a single file, using strong encryption, then deletes the original files.
- StrongCryptor - Encrypts files using strong encryption and safely deletes the original files.
- StrongCryptorFast - Encrypts files using strong encryption and deletes the original files.
- StrongCrytptorNet - Encrypts files using strong encryption and deletes the original files. It also simulates sending the encryption key to a server using an HTTP connection.
- ThorVariant - Simulates the behavior of a recent version of Thor ransomware.
- WeakCryptor - Encrypts files using weak encryption and deletes the original files.
RanSim after the end of the simulations lists the number of successful and failed attacks during the test.





