SARENKA is an Open Source Intelligence (OSINT) tool that helps you acquire and understand Attack Surface.

The main objective is to gather information from search engines for devices connected to the Internet ( https://censys.io/ , https://www.shodan.io/). Displays data on Common Vulnerabilities and Exposures (CVE), Common Weakness (CWE) and also has base data where CVEs are assigned to CWE.
Returns data about the local machine – local installed software (from the Windows registry), local network information (libraries python, popular cmd commands).
At the moment the application also has simple tools such as hash calculator, shannon entropy calculator and very simple port scanner. More cryptography-math tools and authentication scripts will be added.
Specifications
- receives data from https://censys.io/ via ip
- data from https://www.shodan.io/ via ip
- download data DNS
- download data WHOIS
- banner grabbing
- find CVEs from C.W.E.
- pdf for reports
You can also:
- calculate hashes string base
- calculate the shannon entropy based on the user string
Installation
SARENKA requires:
Download from repository
$ git clone https://github.com/pawlaczyk/sarenka.git
Go to the source list
$ cd sarenka / sarenka
We run sarenka.py
$ python sarenka.py
Getting started
#### Create accounts for the following services:
Running a backend application - default http://localhost:8000 /
# go to sarenka / sarenka $ python backend / manage.py runserver
Run frontent application - default http://localhost:3000/
# go to sarenka / sarenka / frontend folder $ npm start
Application snapshots
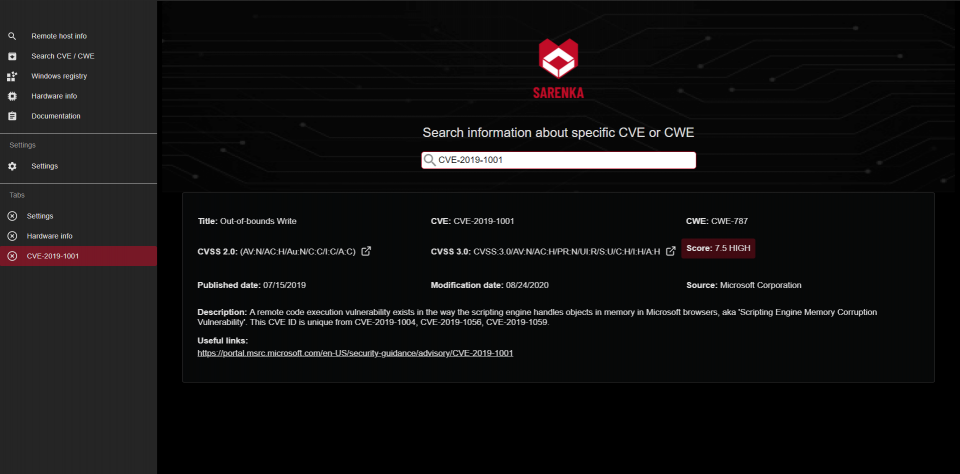
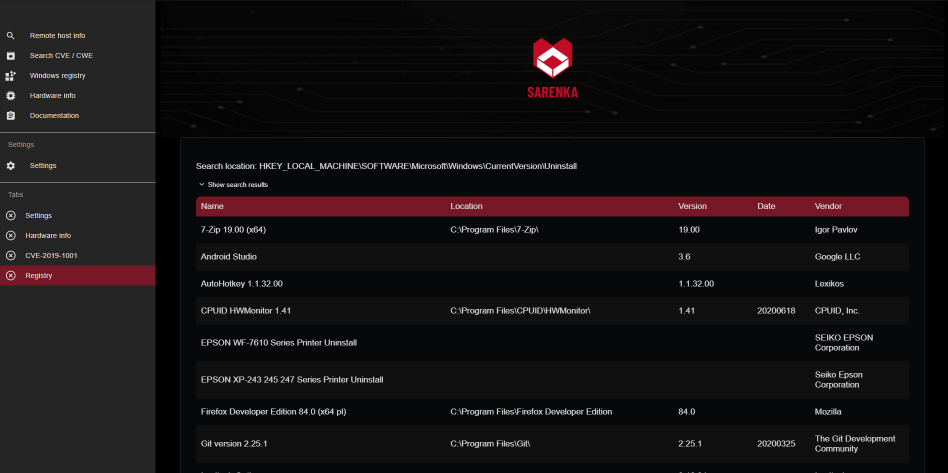
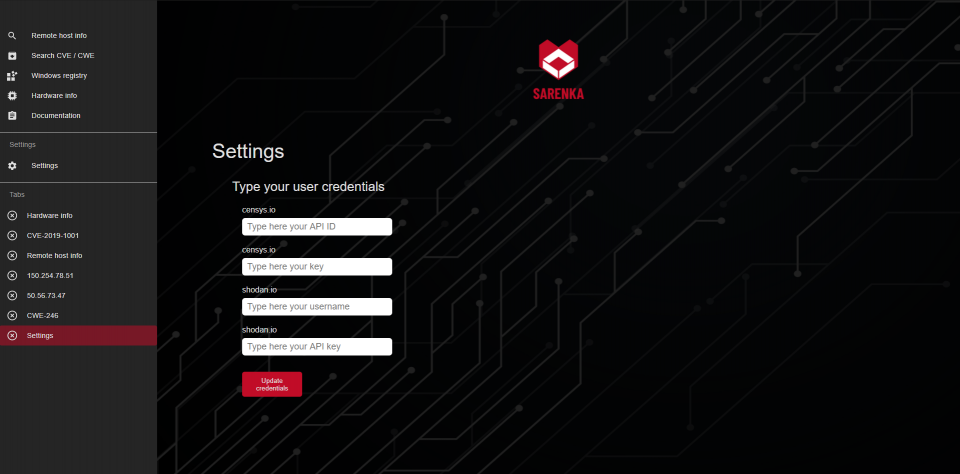
You can download the program from here.





