If you ever get hit by ransomware that encodes the names of encrypted files using the .stn extension, then you are a victim of Satan, not the "Prince of Darkness", but the new Ransomware service of the same name. Yes a new Ransomware as a Service is released online.
The new ransomware was detected on Wednesday by Xylitol security researcher and as it turns out, the new RAAS is marketed through underground forums.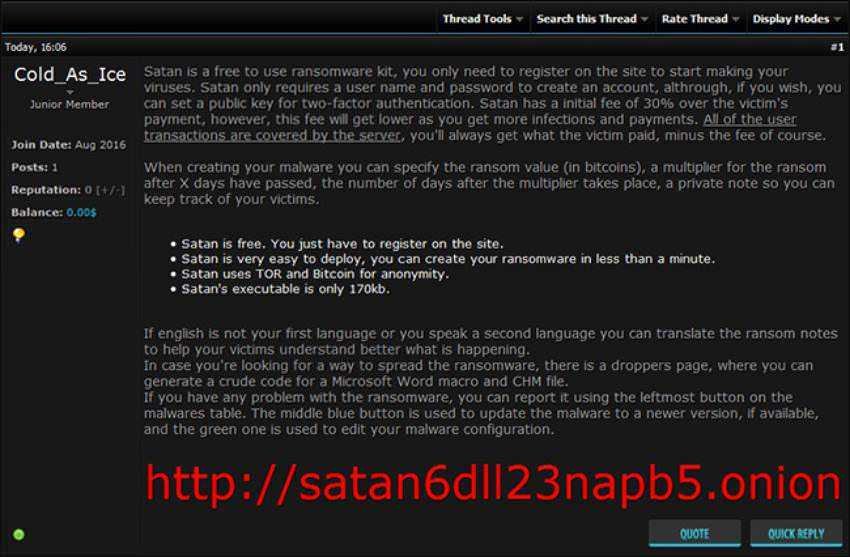
Anyone can use Satan for free, as the seller states, but they will have to give 30 percent of each successful paymentransom in exchange for providing the service.
A visit to the Tor's website reveals a well designed page that offers users the ability to create a variation of malware to their preferences.
Stakeholders can choose dropper hide techniques and have the ability to translate the ransom note, change ways to communicate with the victim, or choose how malware will communicate with them.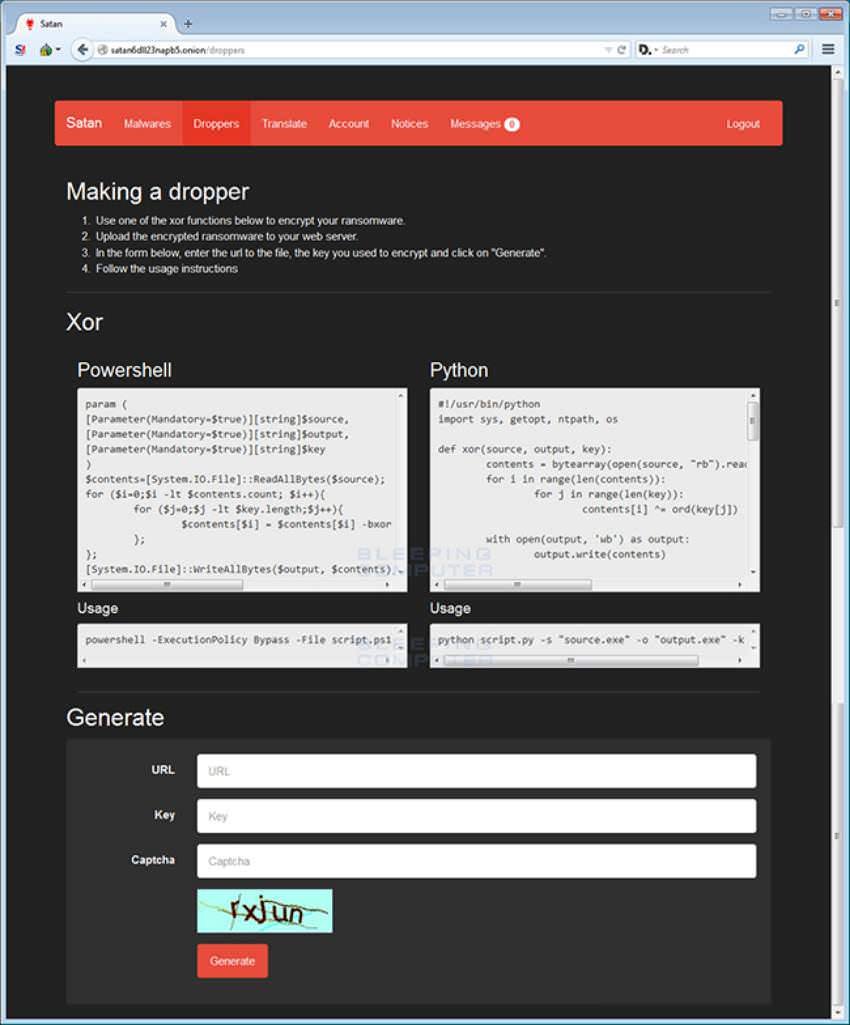
Through this site, registered users using the service can also see how many of the attacks with the ransomware were successful, and the amount they have earned so far.
At this time, we do not know the method encryptions that Satan uses, so it's probably too early to talk about a decryption tool.
So beware of your online walks because, unfortunately, Satan RAAS is extremely easy to use and accessible to anyone who has no hesitation even if it does not have any special knowledge.





