In our today's guide, we will perform reconnaissance on a SCADA target using port scanning with nmap scripts.
Up to this point we have used passive recognition using Shodan and Google dorks, but now we will use a more active approach to find SCADA systems and do some active reconnaissance to get more information before developing or using an exploit.

Nmap is one of those tools that is essential in every hacker/penetration tester's toolbox. Although nmap has many different features (including nmap scripts (NSE)), it started out as a simple one sweeper doors and has remained the best door scanner available to us. As a result, every hacker/pentester should understand the basics of using nmap.
Key features of Nmap
When we can limit his pension Nmap for port scanning in its basic elements, it looks like this,
Simple enough, right?
nmap has many types of scans. Among the most useful and popular are,
T – this is the scan connections. It opens a three-way TCP “handshake” with the target system, thus offering us the most reliable results, but also the least stealthy, as the three-way handshake is recorded by the system.
S – stealth or SYN scanning sends a packet with the SYN flag enabled, thus opening a connection, but without completing the three-way handshake. Therefore, it is not recorded, but it is quite reliable.
U – T and S scans give us information about TCP ports, but not about UDP ports. This scan specifically looks for UDP ports.
X – the infamous XMAS scan. It activates the P, U and F flags and was able to elicit a response from some systems. Although still popular, its utility is now limited.
A – this scan sets the ACK flag, which would normally indicate an ongoing TCP communication. It can be used to confuse and bypass some stateless firewalls.
The most reliable, but least quiet scan
Let's start by attempting a -T or Connect scan against a SCADA target. I chose this one from search in Shodan for systems running on port 502 modbus (modbus is the most popular SCADA protocol). This happens to be a factory in Genoa, Italy.
kali > nmap -sT 88.147.125.34 -p 502
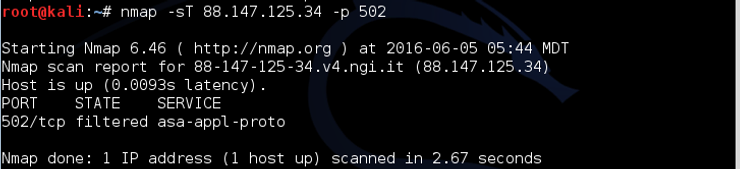
As you can see, nmap found port 502 filtered on this system. This usually indicates that the port is enabled but has a firewall blocking access.
Sometimes, a UDP scan can reveal more information. Let's try an nmap UDP scan on the same target and see if it reveals more information. The Switch for a UDP scan it is -sU.
kali > nmap -sU 88.147.125.34 -p 502
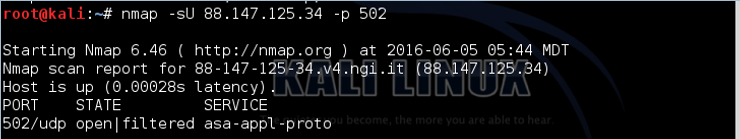
We see that this scan comes back saying port 502 is either open or filtered.
Nmap scripting engine (NSE)
In addition to being a great port scanning tool, nmap also has scripting capabilities. This adds significant capabilities to nmap via the Lua scripting language.
Nmap's scripting engine is one of Nmap's most powerful and, at the same time, most flexible features. It allows users to write their own scripts and share them with other users for networking, recognition, exploitation, etc.
These scripts can be used to:
- Network discovery
- More sophisticated and accurate OS version detection
- Vulnerability detection
- Backdoor detection
- Vulnerability exploitation
Find Nmap Scripts
From the terminal, let's search for Nmap scripts. All scripts should end in .nse (nmap scripting engine), so we can find the scripts using Linux's locate command with the *.nse wildcard. This should find all files ending in .nse, such as,
kali > locate *.nse
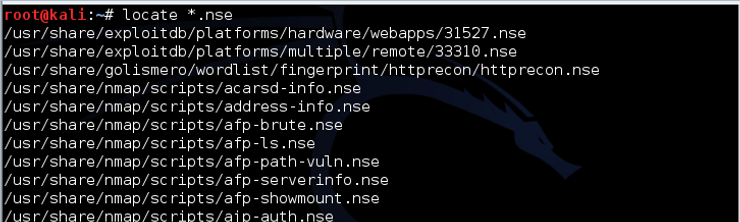
As you can see in the screenshot above screen, our terminal displays hundreds of nmap scripts.
The basic syntax for running these scripts is as follows:
In our case here, we want to use a specific script to find modbus nodes at modbus-enabled sites (although SCADA sites use many different protocols, modbus is the most popular). In other words, if we know that the site uses modbus, this script can discover each of the nodes and their ID.
In addition to the standard syntax, we need to add the script argument 'modbus-discover.aggressive=true' to our command. The command should look something like this.
kali > nmap –script modbus-discover.nse –script-args='modbus-discover.aggressive=true' -p 502 88.147.125.34
When we run it and it is successful, it should be able to provide us with an output of all the modbus nodes in the system.
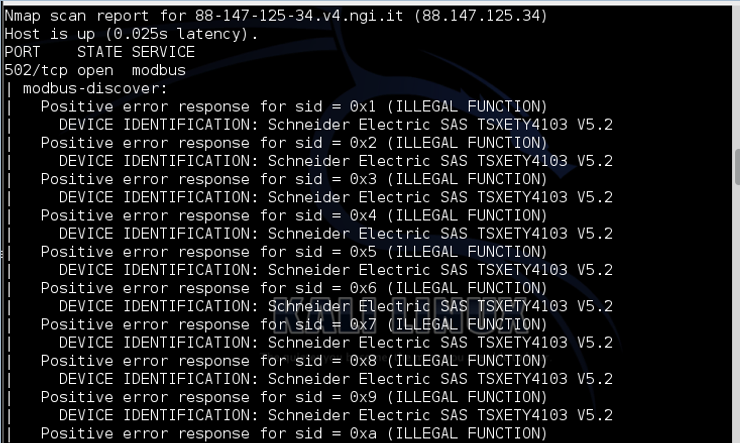
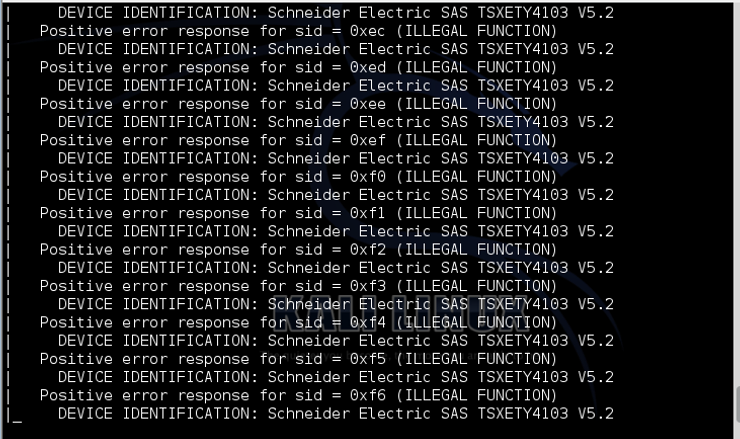
As you can see, it was able to successfully identify the nodes as Schneider Electric SAS version 5.2 and found every single one of the nodes.
Found nodes from 1 (0x01) to 262 (0xf6). This provides valuable information to the attacker as it not only identifies the PLC and version, but also the communication protocol (modbus) and each of the nodes. As SCADA attacks require deep knowledge of ICS operations, this information may be enough for attackers to begin planning their attack on this infrastructure.
SCADA infrastructure is among the most valuable and vulnerable systems in the world. If one of these systems is compromised (as many have been), it can not only cost the company millions of dollars, but it can also cost many lives (eg power grid, water treatment). We were able to not only find these devices, but also enumerate each of their nodes, enabling exploitation of these devices and systems.




