The Smersh είναι ένα εργαλείο ειδικά διαμορφωμένο για pentesters, που usesfor tracking the progress of work in a company and creating interactions between them.

Project architecture
SMERSH uses many docker containers in its architecture, which means you have to allow some services. Below you will find the complete list of doors you need to open. In addition, you will see the shape that composes the database.

Port mapping
| Container | Default DNS |
|---|---|
| Api | api. {DOMAIN} |
| Bitwarden | bitwarden. {DOMAIN} |
| Client | OM DOMAIN} |
| Db | NOT EXPOSED |
| php | NOT EXPOSED |
| CodiMD | codimd. {DOMAIN} |
| db-codiMD | NOT EXPOSED |
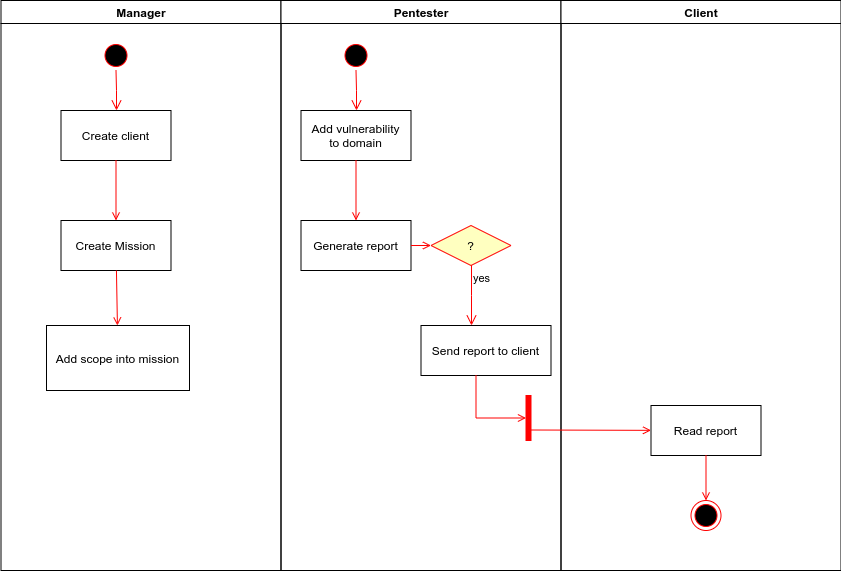
Application life cycle
SMERSH is designed in such a way that the person in charge of each company prepares the target and all that remains is the pentester to complete the vulnerabilities identified during the audit it will carry out.
Installation of the program
Information about installing the program, you will find here.





