The Pepper it is an open source tool code to perform static malware analysis on Portable Executables.

Installation
root @ kali: ~ # git clone https://github.com/Th3Hurrican3/PEpper/
root @ kali: ~ # cd PEpperroot @ kali: ~ # pip3 install -r requirements.txt
root @ kali: ~ # python3 pepper.py ./malware_dir
Snapshots
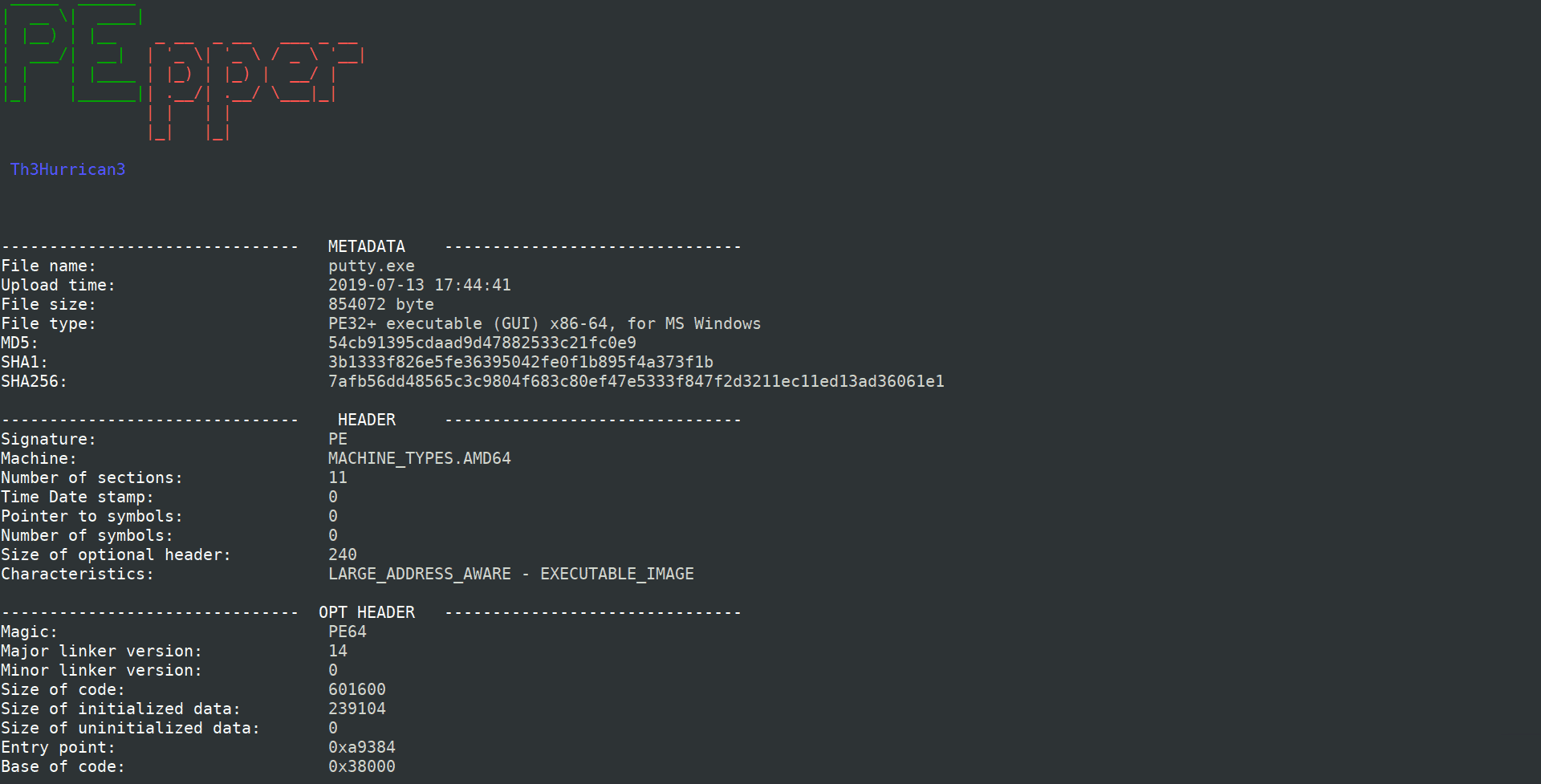
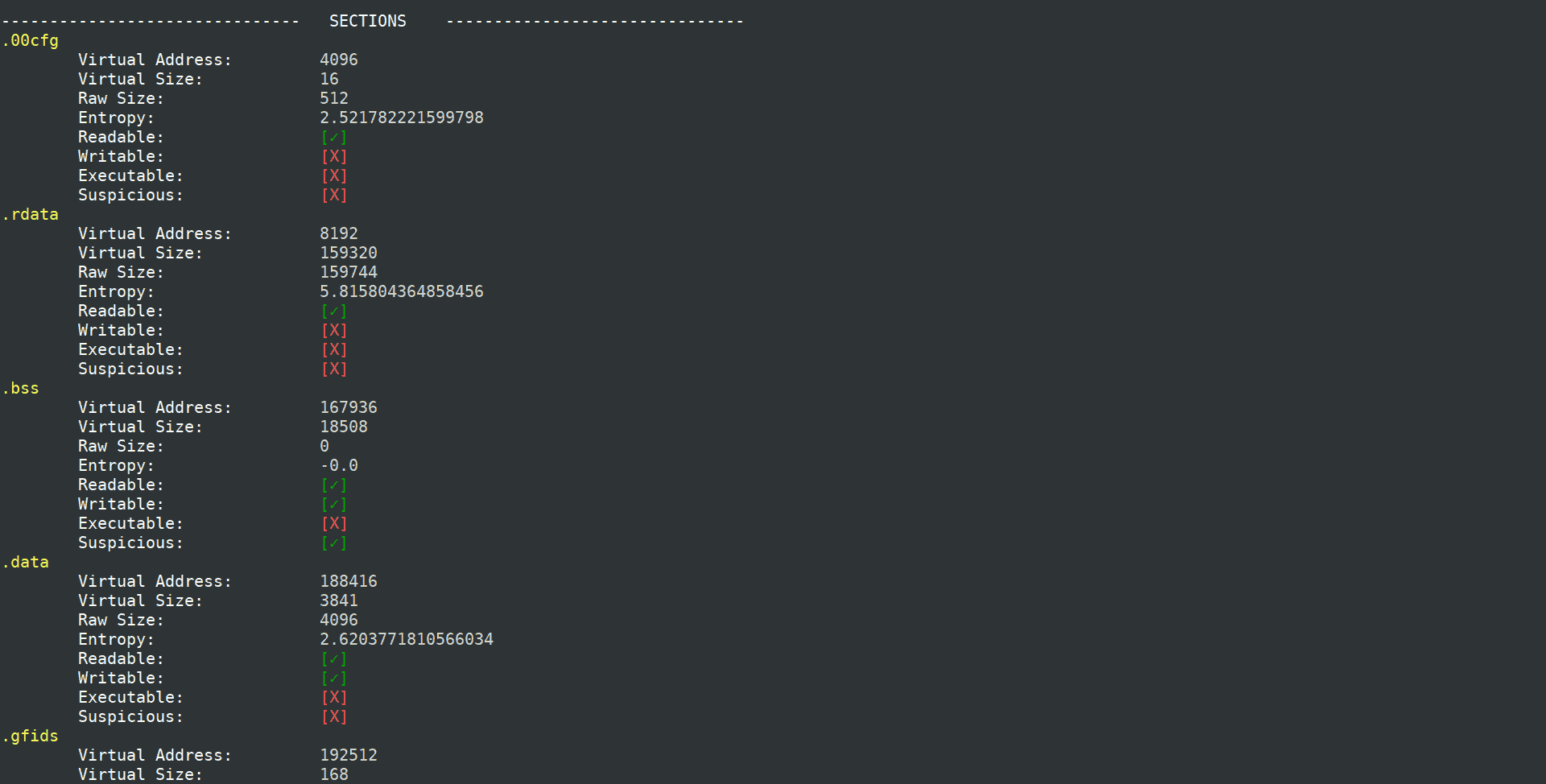
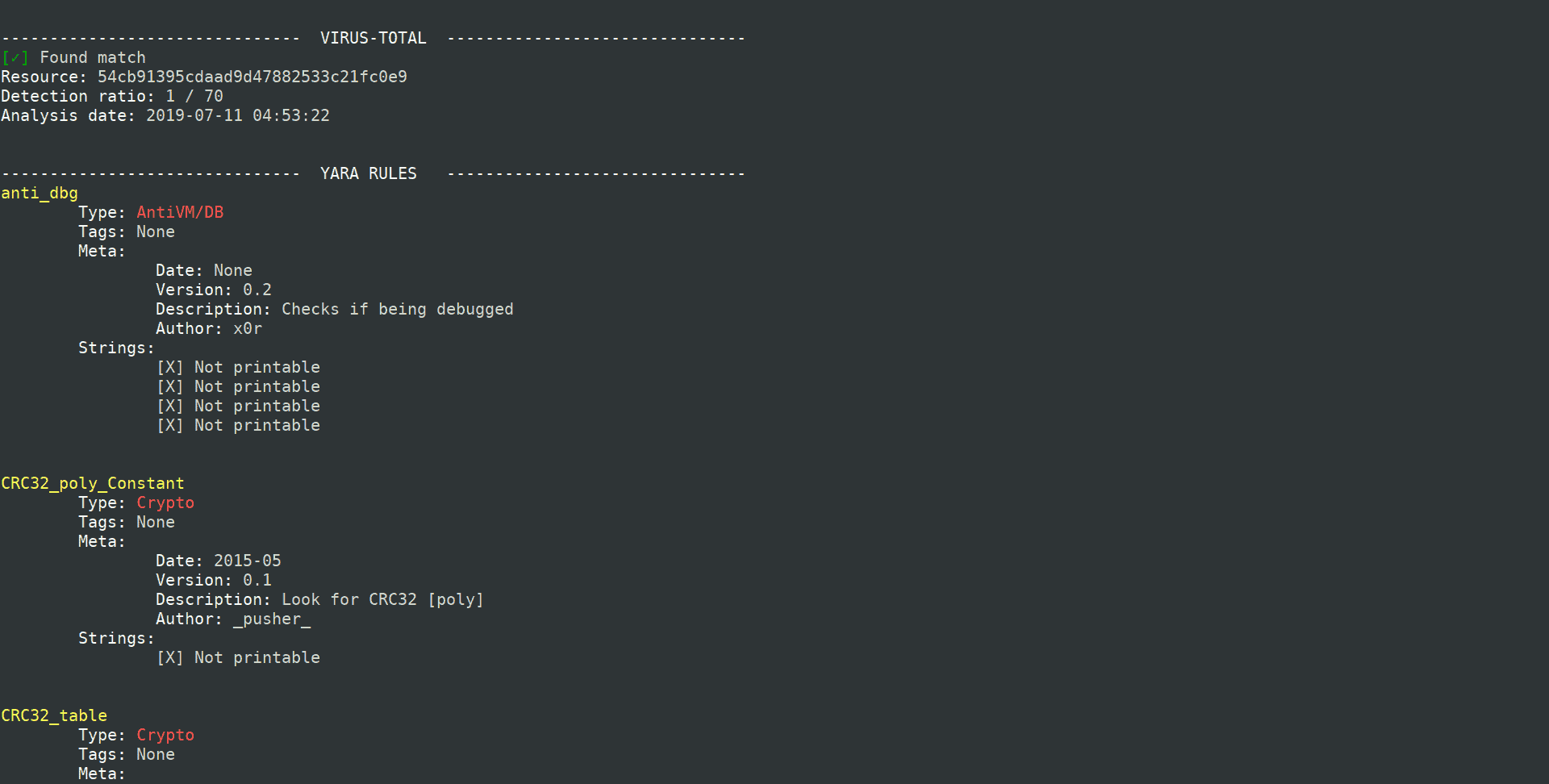
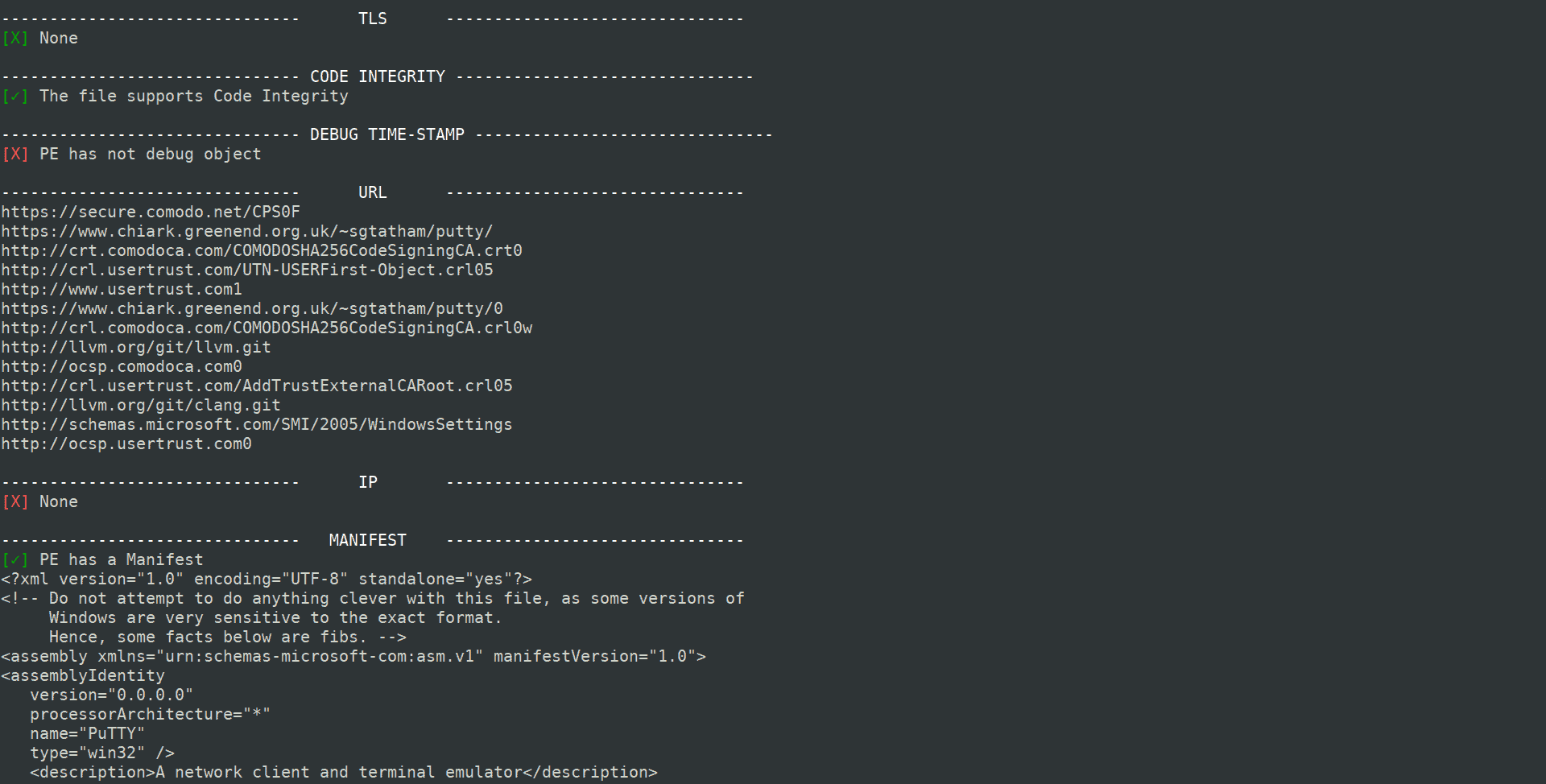
CSV output
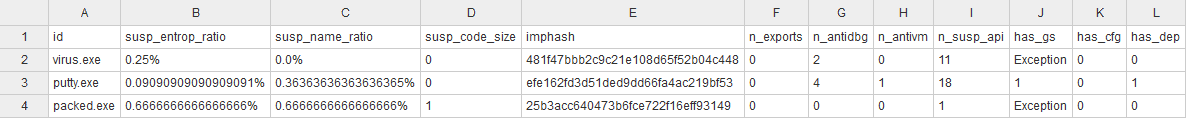
Application features
- Suspicious entropy of ratio
- Suspect names ratio
- Suspicious sizes of codes
- Suspect debugging time-stamp
- Numbers from export
- Numbers from anti-debugging calls
- Numbers from virtual-machine detection calls
- Numbers from suspicious API calls
- Numbers from suspicious strings
- Numbers from YARA rules
- Numbers from URL who discovers
- Numbers from IP who discovers
And much more…
Note
- Can be run in single or multiple PE (placed in a directory)
- The output of the results will be saved (in the same pepper.py directory) as output.csv
- To use VirusTotal scan, add your private key to “virustotal.py” (required connection on the Internet)





