Once again, the time has come for her Symantec to share the latest findings of the annual report Internet Security Threat Report (ISTR), which investigates the current state of the threat landscape, based on the previous year's research and analysis.

Key trends from this year's report include: Mega Breach in the data report and targeted attacks, the evolution of malware and mobile ransomware, and the possible threat posed by the Internet of Things.
The year of Mega Breach in the data
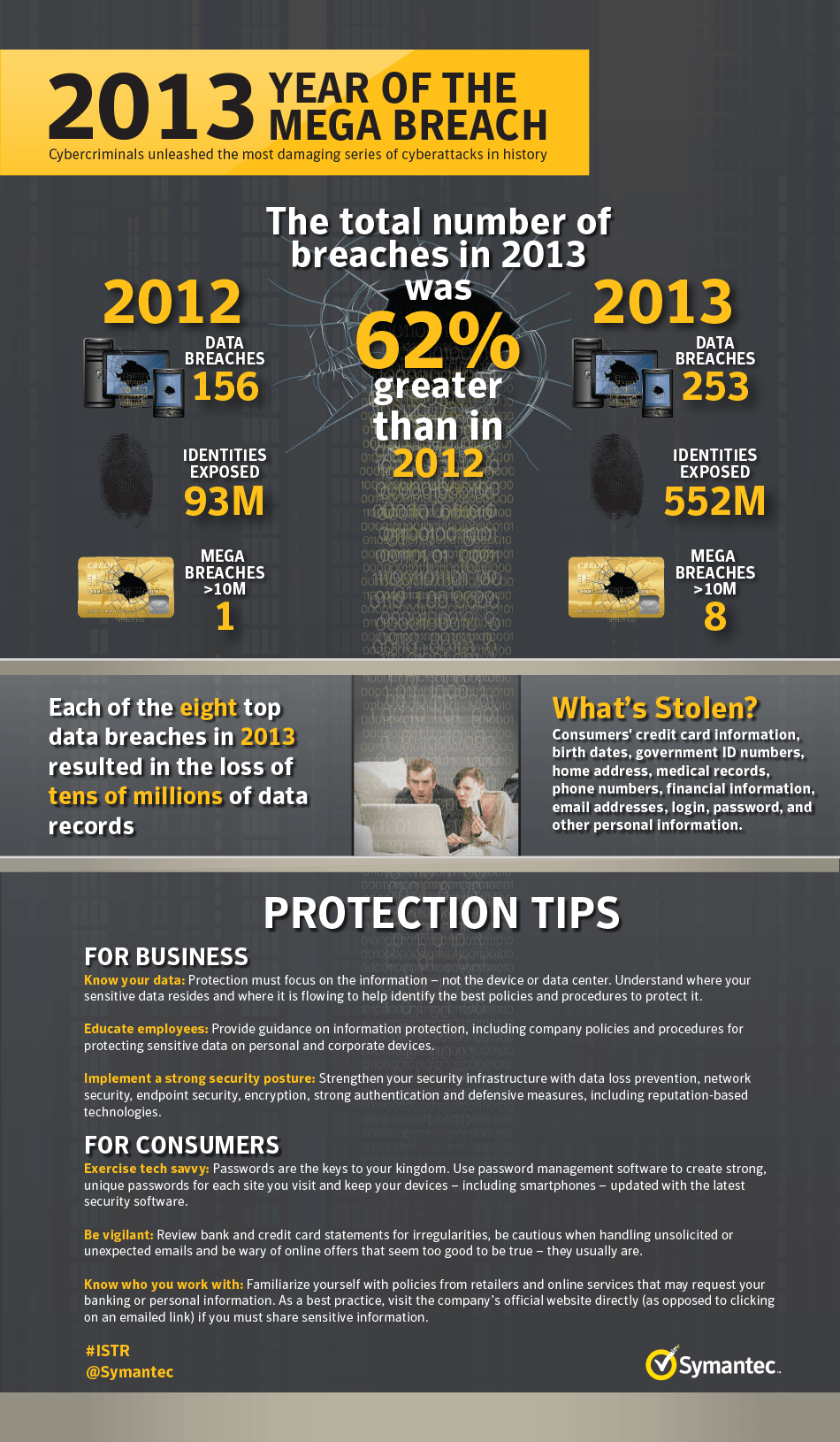
While 2011 has been characterized by many as "The Year of Data Violation," 2013 violations have far outweighed past years in size and scale. For 2013, Symantec discovered that the number of data violations increased by 62% compared to 2012, and translates to more than 552 million identities exposed last year - an increase of 368%. This was also the first year that each of the top eight 2013 data breaches caused the loss of tens of millions of identities - making it really the Mega Breach year in the information report. Compared with the previous year, only one breach of 2012 data has earned this distinction.
Attackers look at Small and Medium Sized Enterprises
As seen in previous Symantec ISTR reports, small and medium-sized businesses (SMBs) are a key target for attackers, and this year was no exception to that trend. In 2013, SMBs accounted for more than half of targeted attacks (61%) – up from last year's 50% figure in 2012 – with midsize businesses (2.500+ employees) seeing the largest increase.
Attacks on businesses of all sizes increased, with an overall increase of 91% compared to 2012. As last year, cybercriminals developed watering holes and spear-phishing techniques to increase the efficiency of their activity. Spear-phishing operations progressed at a slow and low pace, relying less on email to carry out their attacks (down 23%). Watering hole attacks also allowed bad guys to run more drives through drive-by-down targeting of victims on frequently visited websites. Their efforts were aided by a 61% increase in zero-day vulnerabilities, which allowed attackers to install themselves on poorly patched websites and infect their victims with little or no effort.
Η government remained the most targeted industry (16% of attacks). But this year, Symantec didn't just look at the volume of attacks. No one is more favored, we all have to worry about targeted attacks, but looking at the results the company was faced with some surprises. If you are a secretary at a mid-sized company, I have bad news for you – you are at the top of the attackers' "most wanted" list.
Malware and Madware of portable devices invade users' privacy
According to Symantec, while many download new applications to their mobile devices without a second thought, many malicious applications contain very troublesome and unwanted features. 33% of the new malware threats recorded by 2013 detected users and 20% collected data from infected devices. 2013 also featured the first Remote Access Tool (or "RAT") toolkit for Android devices. When executed on a device, these RATs can control and make phone calls, read and send text messages, receive GPS coordinates of the device, activate and use the camera and microphone and access folders stored in the device - all without the victim's knowledge and consent.
The development of Ransomware launches and becomes even more dangerous
As Symantec had predicted in previous reports, ransomware, the malware that locks computers and files, developed rapidly in 2013. ransomware has experienced an explosive growth of 500% in recent years and has remained a highly profitable business for " bad ", offering a net profit of $ 100 to $ 500 USD for each successful ransom payment. We have also seen attackers become more dangerous and take data hostage using high quality encryption and threatening to delete the information forever if the reward is not paid within the given time frame.
The Future of ID: Internet of Things
Which of these items has been hacked in the past year: a refrigerator or a baby intercom?
When we ask Symantec customers this question, they usually answer, "Both". The right answer is baby interphone. Despite what you may have heard in the news, refrigerators that are connected to the internet have not yet been attacked. But never say 'Never'. 2013 security researchers have demonstrated attacks on cars, security cameras, televisions and medical equipment. The moment of the refrigerator will come. The Internet of Things follows him, and threats are certain to follow. In this year's report, the company refers to what we have seen so far, such as the Internet-connected device that is at greater risk today - the home router.
What's next? With personal details and financial information being stored on IOT devices, it's only a matter of time until we find a refrigerator that has been tampered with. At this time, security is a second thought for most manufacturers and users of these devices and will probably need a major security incident until they really worry. However, starting the debate about the possible dangers now, we will be much more prepared when that day comes. This year's ISTR kicks off the debate.
For more details, see the whole Internet Security Threat Report, Vol. 19.