In accordance with recent Symantec 2016 Internet Security Threat Report (ISTR) Theft 21, the number of publicly disclosed business data breaches has increased significantly over the last few years.
Modern organizations and businesses that know their opponents, while at the same time aware of their own strengths and vulnerabilities, can better stand in the ongoing cyber security war. However, one should not wait to be challenged in order to strengthen its attitude towards security. 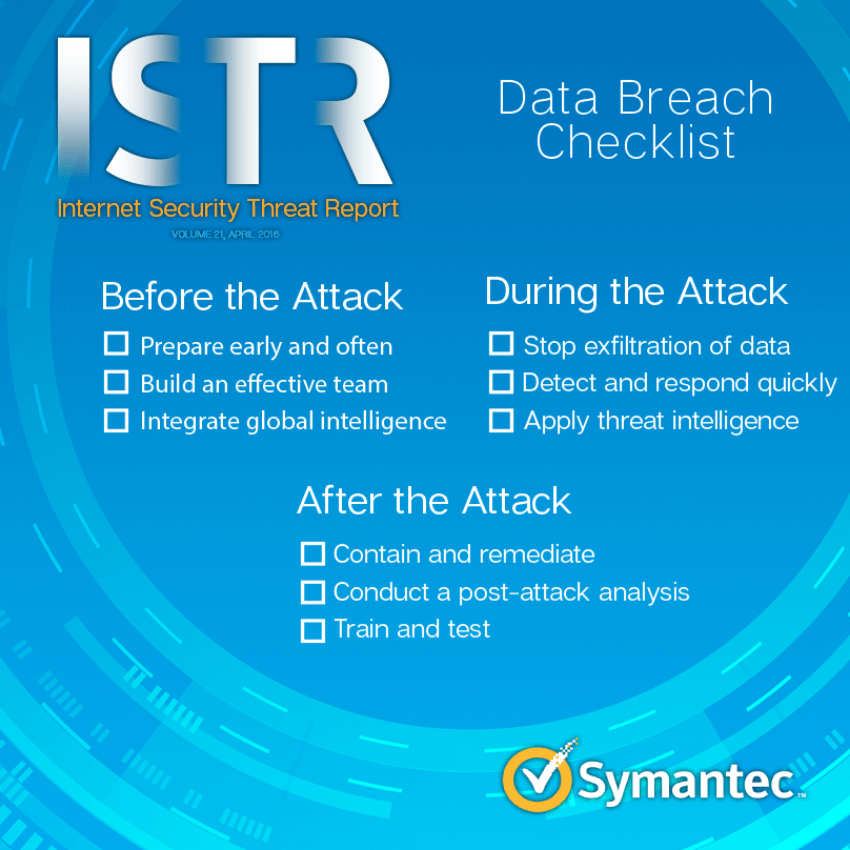
But what measures should an organization take to ensure its valuable data against cyber criminals?
Her experts Symantec have created a very comprehensive list of seven cyber-security checkpoints based on best practices as recorded in the recent 2016 Internet Security Threat Report (ISTR), its annual report Symantec, which provides an overview and analysis on global cyber threat activity.
The following checklist is intended as a guide for managers security and help before, during, and after an attack.
- Verify that all devices that are allowed to be connected to corporate networks have adequate security measures
Use active monitoring and configuration management to maintain a valid inventory of all devices that are connected to your business network. This includes servers, workstations, laptops as well as remote devices. - Deploy Policy Policy
Where possible, restrict unauthorized use of devices such as external portable hard drives and other similar removable media. Such devices may introduce malware software και να διευκολύνουν τις παραβιάσεις της πνευματικής ιδιοκτησίας, είτε εκούσια ή ακούσια. Εάν επιτρέπονται οι εξωτερικές συσκευές πολυμέσων, τότε θα πρέπει να γίνεται automatic scan for viruses when connected to the network and always use a data loss prevention solution (Data Loss Prevention- DLP) that monitors and limits the copying of confidential data to unencrypted external storage devices.
- Symantec: The key is in constant updating and repair
Processes such as update, patch, and migrate from outdated and unsafe browsers, applications, and browser plug-ins should be a fixed process that should be repeated at regular intervals and with reverence. This also applies to operating systems, not only on all computers but also on mobile, ICS and devices IoT. Always make sure you have the latest virus updates and intrusion prevention definitions available by using auto-updates from manufacturers. 
Most software vendors work diligently to provide patches facing the vulnerabilities of the software, however, one patch can only be effective if implemented correctly and timely. Where possible, automate the implementation of young people patches to maintain protection against vulnerabilities throughout the organization.
-
Enforce an effective password policy
Make sure all passwords are strong and at least 8 -10 characters with a mixture of letters and numbers. Encourage users to avoid using the same passwords for multiple sites as well as sharing passwords with others should be banned. Passwords should be changed on a regular basis, at least every 90 days.
- Securing with regular backups
Create and maintain on a regular basis backups of critical systems as well as endpoints. In the event of data security emergencies, backups should be easily accessible to minimize downtime and employee productivity.
- Limit to email attachments
Format them mail servers so as to block or remove messages containing attachments commonly used to spread viruses, such as.vbs,.Beat,.exe,.pif, and the files.scr. Businesses should investigate archive policies PDF which may be included as e-mail attachments. You should also make sure that mail servers are adequately protected by security software and that e-mail are scanned diligently.
- Application procedures infection and incident response
- Keep contact information with the security software company you are working with so that you are ready to immediately deal with any infection or attack on your systems.
- Make sure that a backup and recovery solution is available to repair the loss in the event of a successful attack or catastrophic loss of data.
- Make use of post - infection detection capabilities websites portal, solution endpoint security and firewalls to identify infected systems.
- Isolate infected computers to avoid the risk of further infection inside the organization and restore the systems using reliable backup media.
- If network services are infected by malicious code or other threat, disable or block access to these services until a patch
Η Symantec has a wide range of applications that can protect organizations and businesses across its entire range of IT systems.





