There are many, many tools on the internet that can 'crack', 'fish', 'bypass' your passwords to anything.

Each one of these tools is specialized and addresses everything from your operating system code, your wifi code, even your connection code to a service.
Learn to be protected. These lessons are not meant to show you how to become the hacker, but what methods hackers use and how effective they are.
Lesson 3 - Break a wifi code with WPA / WPA2 encryption
Before we say anything we inform you that this lesson is 3 and the continuation of the 2 course. Before reading this article, please read first the 2 course and the 1 course, so that you can understand exactly what we will be presenting here today.
First of all, let's say as little as possible what and how is a WPA encryption:
The usual WPA version is personal (and not enterprise) and we will talk about it. It is inferior to the enterprise but it is the one we all have in our homes. The inferiority of WPA/WPA2-Personal compared to WPA/WPA2-Enterprise is due to the authentication method, which for all clients is done through a unique pre-shared key or PSK, and that is why you will see it mentioned and like WPA/WPA2-PSK.
That is, the access point (AP) is configured with a specific passphrase (an ASCII alphanumeric code from 8 to 63 characters, the well-known code that you all put on your router), which each client must know in order to be able to pass the authentication and to connect to the wireless network.
But how does WPA certification work? Enjoy the process and we hope you don't get "lost" along the way:
Initially, the basic code on the router, the passphrase, is encrypted using the method salt ("Salted" as we like to say) with the network name (ESSID or SSID) and the length of the name and then encoded by the method PBKDF2, corresponding to 4096 consecutive passes of the SHA-1 algorithm. The result is called a PMK (Pairwise Master Key) and is essentially a 256bit key.
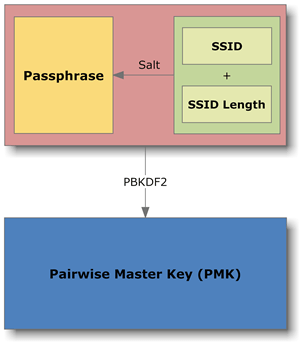
Note that encryption has so far been in it passphrase and network name, so the PMK can be created by the router itself or another access point, as well as by any client that knows these two pieces of information.
Thus, when the user of a client selects an available WPA/WPA2 network and enters the corresponding passphrase to connect, his computer creates the PMK and wirelessly declares his desire to the access point. This is followed by authentication, a communication of four alternating messages starting from the access point, also known as a 4-way handshake.
As for WPA cracking, the main interest lies in the first two messages:
- Access Point creates a random number (ANonce) and sends it to the client.
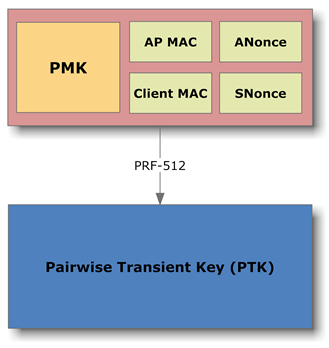
- The client, receives the ANonce and also creates a random number (SNonce). Then, using the PMK, ANonce, SNonce, its MAC address, and the Access Point MAC address, creates a new key called 512bit (Pairwise Transient Key) PTK (with the less complex PRF-512 algorithm). With PTK, the client encodes SNonce by creating a Message Integrity Code (MIC), a digital signature of SNonce. Finally, the client sends the unencoded SNonce and MIC to the Access Point (router).
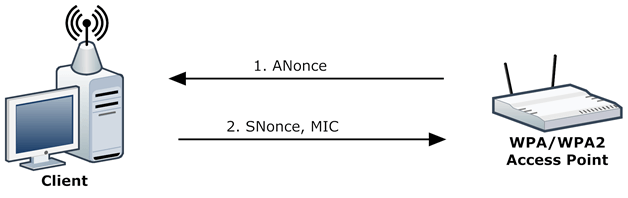
With these two steps, the Access Point is now able to certify that the client is "legitimate" after calculating in turn the PMK (since as an Access Point, it obviously knows its passphrase and SSID), then it calculates the PTK (since it knows the PMK, the necessary MAC addresses, the ANonce it generated and the SNonce it received in message 2), to sign the SNonce with the PTK and see if the result matches the MIC it received.
If it matches, then obviously the client knows the same passphrase as the Access Point and is therefore indeed "legitimate". If you have not already "lost" in the process, be careful that no sensitive information, such as the passphrase or any other key, is transmitted over the air.
In addition, for each client, all this connection to Access Point also occurs periodically, each time that Access Point decides that the PTK should be renewed.
But how do these knowledge help in finding the passphrase and, consequently, in breaking the WPA?
First, let's say that the encryptions used in ciphers like salt and PBKDF2 are one-way. That is, an initial phrase is coded and gives us an "unintelligible" result, but this process cannot be reversed, we cannot find the original phrase from the unintelligible result.
So the logic to compare and to certify that the ¨incomprehensible” result is the right one, is to do the same process, to encode the original phrase, and to compare the results.
So also in the WPA. Despite the extensive use of (known) encodings, the only parameter that cannot be directly known to a third party, is the passphrase, which - anyway - is the point. Otherwise, the SSID of the Access Point (and thus its length) and the MAC addresses of the Access Point and a connected client can be easily found with a network scanner.
Similarly, with a wireless network sniffer that "happens" to be active at the time of authentication of a client with the Access Point, the ANonce, SNonce and MIC of the SNonce can be found freely circulating in the air.
And with all this evidence, a program can take sequential passphrase (brute force or dictionary) and to repeat for each verification process which also makes the Access Point, until, for some passphrase, the signature of SNonce with PTK to match the MIC. This will be the requested passphrase.
Our point is that although the process is automated, that is, you give a computer a table with millions of common codes and tell him to perform the above procedure for each one of them until he finds the code, so our theme is time.
Indeed. You see, for each passphrase that this theoretical cracking program would try, it would have to generate a different PMK. But, as mentioned, generating the PMK requires 4096 consecutive passes of the SHA-1 algorithm, an extremely time-consuming process that will result in essay only a few dozen passphrases per second. And this is not a practical solution.
A smart cracker would usually deal with one like this problem creating a table of pre-calculated hash values, such as a rainbow table.
That is, you would assign a fast system (or preferably a cluster) to calculate all the PMKs that correspond to the passphrases contained in some list or some big dictionary. This process would be just as time-consuming, but would only be done once. From then on and for every attack, the cracker would use the ready table he created, eliminating the need to calculate PMKs, which would send the attack time skyrocketing.
But in the case of WPA, remember that the passphrase, before being encoded to create the PMK, is "salted" with the Access Point's SSID.
This means that if a table is created with precomputed PMK values, it will be useless for attacks on networks with a different SSID than the network it was designed for. In a few words, if we change the name of our network with something irrelevant then we greatly increase the time we find our code from a cracker, to a point where we can say that in combination with a good password he's never going to find it, no matter how powerful and fast a machine he has.
This is the reason that lately the networks have started to put their name and a number as default network names (SSID), such as OTE23E561, or OTE123456 or OTENET2317 etc. Remember that in the past the default names were simply OTE, linksys, wind, dlink , netgear, hol etc
In practice, therefore, today's general WPA break is virtually impossible. Surprisingly, this does not mean that wireless networks using WPA are general safe.
You see, the majority of administrators of such networks, do not know that the security provided by WPA is due to the rarity of the passphrase and the SSID. So, often use common SSIDs (eg myhome, mywlan, dimitris, kostas, spiti, etc.) or leave the default SSID of the router (eg default, linksys, netgear, dlink etc.) or leave the predefined provider's SSID (e.g., otenet, hol wifi, connex, etc.).
At the same time, they use no or very complex passphrase to be able to remember them and easily share them.
So, the aspiring cracker does not need to take into account either all the possible SSIDs, not all possible passphrases. It's just a few precomputed PMK tables for the most common SSIDs, based on an equally common password dictionary. Indeed, such tables are ready to be downloaded to the internet, making the finding of the passphrase in such shared networks a ten-minute case.
And such tables are widely circulated online and for Greek networks.
And well, will you tell us that it is ever possible to have my personal code in a dictionary? how has the cracker pre-guessed it? And yet, imagine a file with millions of pre-guessed codes (you might be able to make some guesses now too), which has no limit of imagination and length. If, for example, your password is of the style "name-year of birth" then you are lost, there is a file with all Greek names and with a four-digit number next to them starting from 1 to 9999, ie dimitris1970 or dimitris1981 is inside and so at some point he will find it.
Let's do the theory:

The tools we need: Of course Kali linux installed on a laptop (or running with a usb live), and some files with codes. Some such small files already exist in Kali, but others can be found on the internet, for example, you can download and try the following for educational purposes only, this here 13 GB or also this here 1,36 GB or also this here42MB with Greek names.
There is still his set Renderman. It consists of 1000 tables for 1000 most commonly used SSID, according to WiGLE project. They are distributed all together, in one giant torrent of 33Gb. The list of SSIDs they cover is available here and the dictionary on which they are based here.
We start… ..
1. Open your router, set it to WPA or WPA2 encryption and give it a common name and password. Open a console (terminal) in Kali and type the following to see what linux names (and if you have) the wireless network card
airmon-ng
2. Suppose the result tells you that you have wlan0 (give the following commands for the corresponding name of your wireless network card).
On the same console, type the following to set the wireless controller to monitor mode:
airmon-ng start wlan0
3. The result should be monitor mode enable on mon0 (or mon1 etc).
Next move to the same console to see the following wireless networks in your area
airodump-ng wlan0
The results of the above command are two arrays. In the upper table you can see all active Access Points (routers) in the area and in the lower table you can see a list of clients connected to them. For now, from the first table choose a strong active Access Point (AP for short) that you want to attack (meaning yours).
This AP should have a name (ESSID column) for which you have the corresponding table with precomputed PMK. It should also use the WPA or WPA2 protocol in its PSK version (ENC and AUTH columns). After choosing an AP, note somewhere its name, MAC address, and the channel it operates on (ESSID, BSSID and CH columns) and if you want to terminate airodumb-ng press Ctrl-C.
4. Open a new console and using this information, enter:
airodump-ng –c channel -w namecapture_file –-bssid MAC_addressof_AP wlan0
e.g. : airodump-ng –c 1 –w tutorial –-bssid E0:1D:3B:3D:E9:44 wlan0
With the above command, you ask airodump-ng to capture all the data circulating in the air that is about the specific AP and save it to the file you specified (in our example, you named it tutorial.cap). But you don't want any data.
You want the ones exchanged between the AP and a client during the authentication process. So, first check the bottom panel shown by airodump-ng to see if there is any client connected to the AP. If the table is empty, then there is no client connected and all you can do is wait for someone to connect. If there is a connected client, first note the MAC address of the client (STATION column).
5. Then open a third console and enter:
aireplay-ng –-deauth 5 –a AP_MAC_address –c client_MAC_address wlan0
e.g. : aireplay-ng –deauth 5 –a E0:1D:3B:3D:E9:44 –c 14:89:FD:56:E7:1E wlan0
With the above command, aireplay-ng will send deauth packages to the client, forcing it to repeat the authentication process so that airodumb-ng can capture the data it needs.
Either with normal or artificially induced authentication, when airodump-ng captures the necessary data, it will display (at the top of the console it occupies) the message “WPA handshake” followed by the MAC address of the AP (be careful, never while airodump-ng captures the authentication data successfully every time, it might not show this message.
So, if it happens that after running aireplay-ng or the normal authentication of a client, the message in question does not appear, try to proceed to the next step immediately). At this point you can now stop capturing data with airodump-ng (Ctrl-C).
6. All you have to do is assign the passphrase search to aircrack-ng, already having a dictionary on your disk. On the console, type:
aircrack-ng -w namefilewith–b SSID codesofAP namefile_capture
e.g. : aircrack-ng –w word-passwords.txt –b E0:1D:3B:3D:E9:44 tutorial-01.cap
Here, before writing the aircrack-ng command, give the console the ls command to see the file names of your directory and therefore the name of the capture file created in step # 4 by the airodump-ng command. We then asked to name this file tutorial but if there is a file with the same name then the airodump-ng command does not crash but creates a file named tutorial-01. So make sure you give aircrack-ng the correct name for your file.
Alternatively for step 6 you can use the cowpatty command if you have a file with precomputed PMK codes stored on your disk.
6a. (alternative to 6). All you have to do is assign the passphrase to coWPAtty. On the console, type:
cowpatty –r namecapture_file –d filetableprecomputed_PMK –s SSIDof_AP
e.g. : cowpatty –r tutorial-01.cap –d linksys.wpa –s Linksys
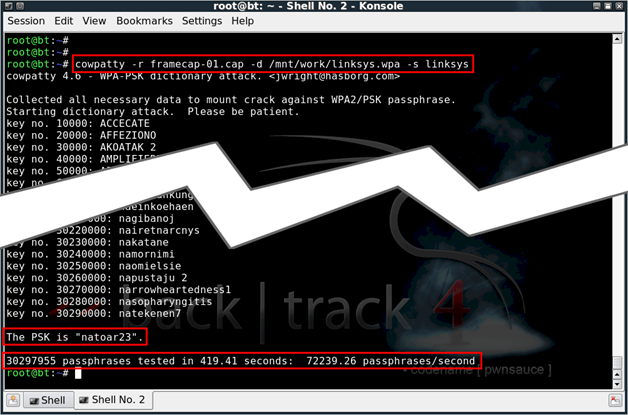
Both ways leave your computer alone to work. If you look at how your system works from then on, you will see that all the cores are working 2% and your machine is "giving its due".
If everything goes well and your code is in the code file then at some point it will inform you that it has found it and it is so and so.
If you absolutely want to try the technique on an AP, for the SSID of which you do not find a ready-made precomputed PMK table, you can use a simple dictionary file.
Just change the syntax of coWPAtty and instead of “–d table_file”, put “-f dictionary_file”. Of course, the process will be hundreds of times slower and impractical for massive dictionaries.
If you want to test the technique often on a certain AP (because, for example, the owner changes the passphrase often), but you do not find a ready-made precomputed PMK table for the corresponding SSID, you can create your own table.
You will need a dictionary and the genpmk tool, which comes with coWPAtty (and thus Kali linux). To build, open a console and type:
genpmk –f filedictionary –d namefiletable –s therare_SSID
e.g. : genpmk –f word-passwords.txt –d preco-table.wpa –s mitsos
In conclusion:
But what did all this teach us? That if we want to be safe then we must:
a. use only WPA or WPA2 encryption,
b. to change the default network name to something unusual, such as "geiaxara" or "geia_sou_geitona" or "mitsos"
c. to enter an unusual code that is not related to (or only) our name, age, address, team, city, animal etc (don't forget that we will be hacked by our neighbor who might know some information about us).
We also understand your need to not want to mess with incomprehensible alphanumeric symbols that will be difficult to remember and manage. So we suggest a huge phrase that you like and easily remember together with an unrelated number-symbol as a good solution, like say “arnaki_aspro_kai_paxi_(@)” or “ta-maura-matia-sou-otan-ta-vlepo- me-zalizoune-1000” or “to.1821.egine.i.epanastasi.stin.ellada” are quite good, easy to remember and easily recognized by customers.
In the next lesson we will show you how to "break" the code of our WPA wireless network with the raven program and how the hackers will easily and quickly create their own dictionary with the crunch and cupp programs.
dimitris - iGuRu.gr






ayto edo breika edo gia windows kai mou kanei douleia http://www.filesnack.com/files/ctu8vay8