Symantec warns of exacerbation Trojan Viknok. Before Ransomware appeared, clicks scams were among the most popular and most effective ways to make money for cybercriminals.
Η technique "Click-Fraud" is the practice of collecting clicks on advertisements with the aim of increasing revenue for the websites that use it.
According to Symantec, a new malicious software was used by cyber criminals to collect clicks. Last month, the company's researchers noticed an increase in infections from a malware named Trojan.Viknok.
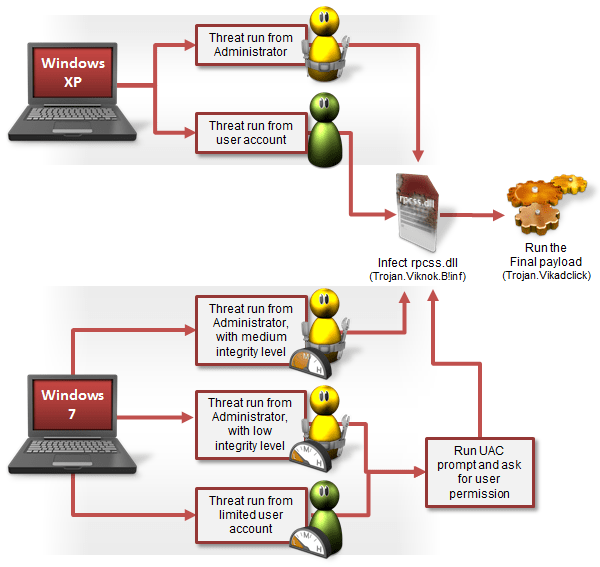
Το Trojan.Viknok παρατηρήθηκε για πρώτη φορά από τους ερευνητές ασφαλείας τον Απρίλιο του 2013. Οι ερευνητές κατάλαβαν ότι το κακόβουλο λογισμικό ήταν μια εξελιγμένη απειλή, επειδή είχε την ικανότητα να μετατρέψει τον υπολογιστή των θυμάτων σε ένα botnet. Για να το κάνει αυτό, το κακόβουλο λογισμικό μπορεί να αποκτήσει προνόμια διαχειριστή του λειτουργικού συστήματος για να μολύνει τα αρχεία του συστήματος σε πολλαπλά λειτουργικά συστήματα των Windows, όπως στις εκδόσεις 32 και 64 – bit των Windows XP, Vista και 7.
Then, infected computers from Viknok were used by cyber criminals to conduct ad-click-fraud.
"The scammers behind the current Viknok campaign are trying to add more and more victims to their AdClick botnet to make more money," Symantec said in a statement.
How does Viknok infect their computers?
Viknok is quite sophisticated as mentioned above and infects victims' computers by injecting its payload into the system's DLL files. Cybercriminals use several methods to infect files, such as rpcss.dll, a library that runs every time Windows starts. Thus, since an attacker could infect the rpcss.dll file, the malicious code executes every time Windows starts.
«Σε πολλές περιπτώσεις , η procedure της μόλυνσης είναι εντελώς λαθραία, η απειλή δεν δείχνουν καμία προειδοποίηση προς το χρήστη. Το κακόβουλο λογισμικό είναι επίσης δύσκολο να ανιχνευθεί, δεδομένου ότι δεν παρουσιάζει καμία ύποπτη διεργασία να εκτελείται, ούτε μολύνει κάποια από τα βασικά σημεία του συστήματος” αναφέρουν οι ερευνητές της Symantec στο blog τους.
When the malware starts running, User Account Control ( UAC ) of the system asks the victim to give the necessary rights. If the user does not give their permission, their system will not be infected. But the malware disguises itself as a process that is home to the user, in order to extract their permission and gain the rights they need.
Once the system owner has been granted permission, the attacker can remotely send commands and load different websites. The websites offer car insurance, travel tickets, domain name listings, and many other services.
The number of Viknok infections has skyrocketed over the past few months. From January to April, the number of unique infections rose from 10.000 to 22.000. Over 16.500 unique Viknok infections have been seen in the first week aloneteam of May. The majority of victims are in the United States.





