ESET researchers analyzed the Turla cyberespionage group's new PowerShell-based tools. These tools are more resistant to attacks and appear improved functions avoiding detection mechanisms.
The popular APT (Advanced Persistent Threat) team, also known as Snake, recently started using PowerShell programming scripts, which can instantly download and run executable files and malware libraries.
Using PowerShell-based tools, Turla cybercriminals can bypass the detection techniques that are activated when a malicious executable file appears on a disk.
Turla is a well-known cyber espionage team, which stands out for the use of complex malware in its attacks.
Its actions are believed to date back to at least 2008, when US military systems were breached. It is also involved in serious attacks on many government agencies in Europe and the Middle East - including the German Foreign Ministry and the French Army.
Recently, ESET researchers have identified a number of attacks using PowerShell programming scenarios against diplomatic missions in Eastern Europe. "These are probably the same scenarios that Turla uses against other global targets," said ESET researcher Matthieu Faou, who led the study.
ESET researchers have published one article with the results of their analysis of the PowerShell scripts that the Turla team uses to help counter the attacks. "In addition to the new PowerShell loader used by Turla, we discovered and analyzed several interesting payloads, such as a backdoor cuts based on an RPC protocol and a PowerShell backdoor, which uses OneDrive, Microsoft's cloud storage service, as a Command and Control server,” says Faou.
PowerShell loaders, which, when detected, are classified by ESET under the generic name PowerShell / Turla, stand out from the common droppers for their ability to remain in the system, as they regularly load into memory only the built-in executable files.
In some samples, the Turla cybercriminals had modified PowerShell scripts to bypass the Antimalware Scan Interface (AMSI). This technique, which was first discovered at the conference Black Hat Asia 2018, results in the antimalware product being unable to receive data from the AMSI for scanning.
"However, these techniques do not prevent the detection of real malicious charges in memory," explains Matthieu Faou.
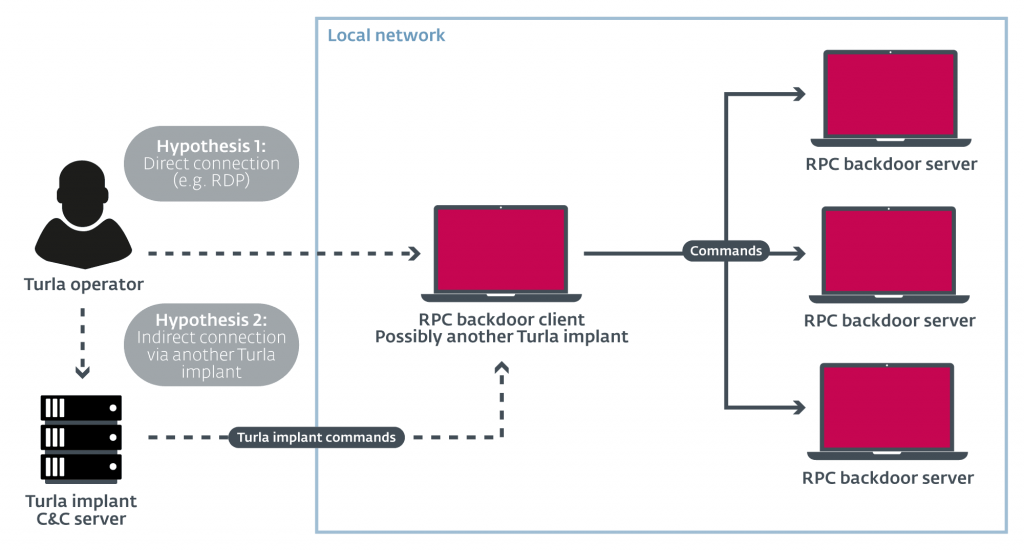
Among the malicious cargoes recently used by Turla, two stand out. One is a whole set of backdoor based RPC protocols. These backdoors are used to perform sideways movement and take control of other machines on the local network without relying on an external C&C server. Also of interest is PowerStallion, a lightweight PowerShell backdoor that uses Microsoft's OneDrive cloud storage service as a Command & Control server.
"We believe this backdoor is a tool to regain access in the event that Turla's main backdoors are removed and cybercriminals can no longer access the compromised computers," said Matthieu Faou.
ESET researchers continue to closely monitor the APT Turla team and other similarly important teams, researching their methods, tactics and procedures to help organizations protect their networks.
More details can be found in the relevant article on ESET's blog, WeLiveSecurity.com.
____________________
- Mageia 7 RC with Linux kernel 5.1.5 and KDE Plasma 5.15.4
- Google, WhatsApp, and Apple slap at GCHQ
- The Honda electric car brings the exterior mirrors in





