As hackers, we often face the hurdle of cryptography and encryption. Every security engineer understands that encryption makes an attacker's job much more difficult. In some cases it can be useful to the hacker, to hide actions and messages.
Many applications and protocols use encryption to maintain data confidentiality and integrity. Before you can crack passwords and encrypted protocols like SSL and wireless, you need to have at least a basic familiarity with the concepts and terminology of cryptography and encryption.
For many new hackers, all the concepts and jargon of cryptography can be a bit difficult to understand. To begin with, cryptography is the science and art of hiding messages so that they are confidential, and then “hiding” them so that only the intended recipient can read them. Basically, we can say that cryptography is the science of secret messages.
With this brief overview for newcomers, I hope to dispel the fog surrounding this topic and shed some light on cryptography. I will try to familiarize you with the basic terminology and concepts so that when you read about hashing, wireless cracking or password cracking and the technologies encryption, have some idea of what is being considered.
Don't get me wrong, I don't intend to turn you into a cryptographer here (that would take years), but just to help familiarize the beginner with cryptography terms and concepts to help you become a reliable hacker.
I will try to use as simple words as possible to describe these technologies, but like everything in IT, there is a very specialized language for cryptography and encryption.

Let's start by breaking encryption down into different categories.
Encryption types
There are several ways to categorize cryptography, but for our purposes here, I've divided them into four main areas (I'm sure cryptographers will disagree with this classification system, but so be it).
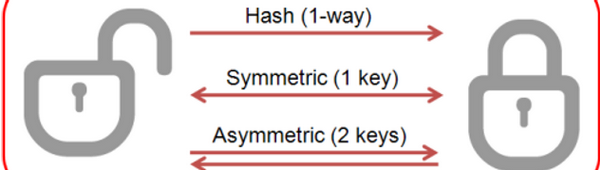
- Symmetric Encryption
- Asymmetric Encryption
- hashes
- wireless
A few words about the size of the key
In the world of cryptography, size matters! In general, the larger the key, the more secure the encryption. This means that AES with a 256-bit key is stronger than AES with a 128-bit key and may be more difficult to crack. In the same encryption algorithm, the larger the key, the stronger the encryption.
This does not necessarily mean that larger keys mean stronger encryption between encryption algorithms. Between algorithms, the strength of encryption depends on both the specifics of the algorithm and the size of the key.
Symmetric Cryptography
Symmetric cryptography is when we have the same key in the sender and receiver. It is the most common form of cryptography. You have a password or “key” that encrypts a message and I have the same password to decrypt the message. Anyone else can't read our message or data.
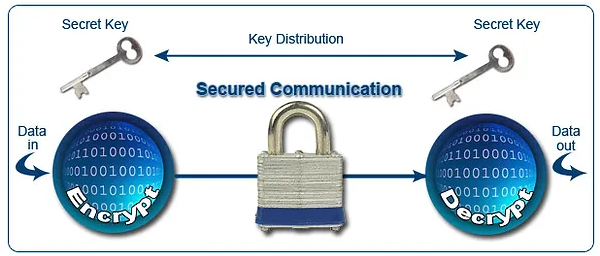
Symmetric cryptography is very fast, so it is suitable for mass storage or streaming applications. The disadvantage of symmetric cryptography is what is called key exchange. If both ends need the same key, they have to use a third channel to exchange the key, and therein lies the weakness.
If there are two people who want to encrypt their communication and they are 12.000 miles apart, how are they going to exchange the key? This key exchange is fraught with all the privacy issues of the medium they choose, whether it's a phone, post office, email, face to face, etc. The key exchange can be intercepted and make the confidentiality of the encryption questionable.
Some of the common symmetric algorithms you should be familiar with are:
- DES – This was one of the original and earliest encryption systems developed by IBM. It was found to be flawed and fragile and was used in the original hashing system of LANMAN hashes on early (pre-2000) Windows systems.
- 3DES – This encryption algorithm was developed in response to the flaws of DES. 3DES applies the DES algorithm three times (hence the name “triple DES”) making it slightly more secure than DES.
- BEA – The Advanced Encryption Standard is not an encryption algorithm but a standard developed by the National Institute of Standards and Technology (NIST). Currently considered the strongest encryption, it uses a 128, 196 or 256 bit key and has been occupied by the Rijndael algorithm since 2001. It is used in WPA2, SSL/TLS and many other protocols where confidentiality and speed are important.
- RC4 – This is a stream cipher (encrypts each bit or byte rather than a block of information) and was developed by Ronald Rivest, known as RSA. Used in VoIP and WEP.
- Blowfish – The first of the encryption algorithms by Bruce Schneier. It uses variable key length and is very secure. It is not patented, so anyone can use it without permission.
- Twofish – A stronger version of Blowfish that uses a 128 or 256 bit key and was a strong competitor to AES. Used in Cryptcat and the OpenPGP, including. It is also public domain without patent.
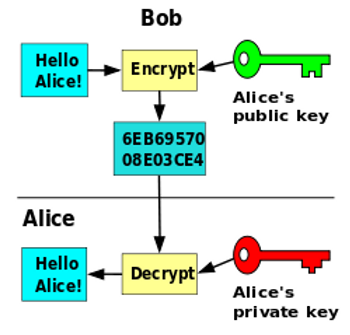
Asymmetric Cryptography
Asymmetric cryptography uses different keys at both ends of the communication channel. Asymmetric cryptography is very slow, about 1.000 times slower than symmetric cryptography, so we don't want to use it for bulk encryption or streaming communication. It does, however, solve the problem of key exchange. Since we don't need to have the same key at both ends of a communication, we don't have the problem of key exchange.
Asymmetric cryptography is mainly used when we have two entities unknown to each other that want to exchange a small piece of information such as a key or other identifying information such as a certificate. It is not used for bulk or stream encryption due to its speed limitations.
Some of the common asymmetric encryption schemes you should be familiar with are:
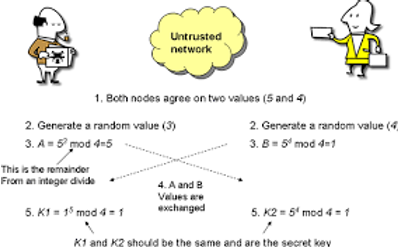
- Diffie-Hellman – Many people in the field of cryptography consider Diffie-Hellman key exchange to be the biggest development in cryptography (I would agree). Without delving into the math, Diffie and Hellman developed a way to generate keys without having to exchange keys, thus solving the key exchange problem that plagues symmetric key cryptography.
- RSA – Rivest, Shamir and Adleman is an asymmetric encryption system that uses the factorization of very large prime numbers as the relation between the two keys.
- PKI – Public key infrastructure is the widely used asymmetric system for exchanging confidential information using a private and a public key.
- ECC – Elliptic curve cryptography is becoming increasingly popular in computing as it is efficient and requires less computing power and energy consumption for the same level of security. ECC is based on the joint relationship of two functions that lie on the same elliptic curve.
- PGP – The Pretty Good Privacy uses asymmetric encryption to ensure the privacy and integrity of email messages.
hashes
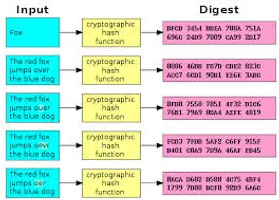
Hashes are one-way encryption. A message or password is encrypted in a way that cannot be reversed or decrypted. You might ask yourself, "What good would it do us to have something encrypted and then not be able to decrypt it?" Good question!
When the message is encrypted, a “hash” is created that becomes a unique, but undeciphered, signature for the underlying message. Each message is encrypted in such a way as to create a unique hash.
Typically, these hashes are of fixed length (an MD5 hash is always 32 characters). This way, the attacker cannot decipher any information about the underlying message from the hash length.
Because of this, we don't need to know the original message, we just need to see if any text produces the same hash to check its integrity (immutability).
This is why hashes can be used to store passwords. Passwords are stored as hashes, and then when someone tries to log in, the system hashes the password and checks if the generated hash matches the stored hash. In addition, hashes are useful for integrity checking, for example, with file or system file downloads.
In the world of encryption and hashing, a "collision" is when two different input texts produce the same hash. In other words, the hash is not unique.
This can be a problem when we assume all hashes are unique, such as in certificate exchanges in SSL. The NSA used this conflict property in the Stuxnet malware to give it what appeared to be a legitimate Microsoft certificate. Hashing algorithms that produce collisions are, as you might guess, flawed and insecure.
These are the hashes you should be familiar with.
- MD4 – This was an early Ron Rivest hash and has been largely deprecated due to conflicts.
- MD5 – The most widely used hashing system. It is 128-bit and produces a digitized message of 32 characters.
- SHA1– Developed by NSA, more secure than MD5, but not as widely used. It has a 160-bit digest that is usually rendered in 40-character hexadecimal. It is often used for certificate exchanges in SSL, but due to recently discovered flaws, it has been deprecated for this purpose.
Wireless Cryptography
Wireless cryptography has been a favorite topic of my readers as many here try to crack wireless access points. As you might guess, wireless cryptography is symmetric (for speed), and as with any symmetric cryptography, key exchange is critical.
- WEP – This was the original encryption system for wireless networks and was quickly discovered to be flawed. It used RC4, but due to the small key size (24-bit), it repeated the IV approximately every 5.000 packets allowing easy hacking in a crowded network using statistical attacks.
- WPA – This was a quick fix to WEP's flaws, adding a bigger key and TKIP to make it slightly harder to crack.
- WPA2-PSK – This was the first of the most secure wireless encryption systems. It uses a pre-shared key (PSK) and AES. It then salts the hashes with the AP name or SSID. The hash is exchanged during authentication in a four-way handshake between the client and the AP.
- WPA2-Enterprise – This wireless encryption is the most secure. Uses 128-bit key, AES and remote authentication server (RADIUS).
The importance of cryptography is enormous in the fields of computer security and telecommunications. Its main purpose is to provide mechanisms for 2 or more communication ends (eg people, computer programs, etc.) to exchange messages, without any third party being able to read the information contained except for the two main ends.





