When WannaCry hit around the world in mid-May, it has been reported many times that extensive use of the old Windows XP operating system has helped spread the infection very quickly.
The UK's National Health Service was one of the most high-profile victims of the attack – and many of its bespoke systems are still running Windows XP. Microsoft if you remember was quick to release an update security for the long unsupported operating system.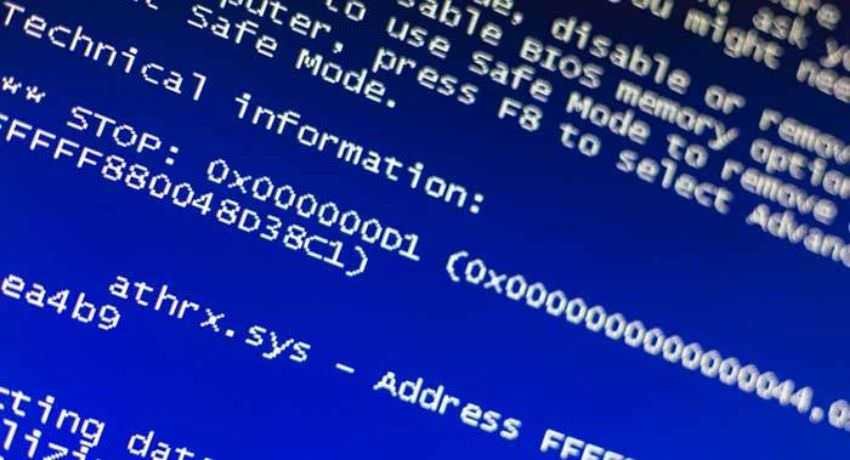
And while Windows XP systems were among those hit by WannaCry, later an analysis showed that 98 percent of the victims used Windows 7.
But that doesn't mean WannaCry didn't work for targets running Windows XP. According to a new report from Kryptos researchers, while this particular operating system was mostly the most dangerous to fall victim to ransomware, many attacks they simply led to system crashes and the appearance of "blue screenof death.” After that a system reset was required.
Researchers tested WannaCry ransomware on some operating systems in a test environment: Windows XP with Service Pack 2, Windows XP with Service Pack 3, Windows 7 x64bit with Service Pack 1, and Windows Server 2008 with Service Pack 1.
While Windows 7 attacks successfully installed WannaCry, after many attempts, supposedly vulnerable Windows XP was much more resistant to ransomware than expected, and the operating system running the 2 Service Pack was not infected at all.
However, Windows XP with SP 2 was affected, but instead of being infected with WannaCry and asking for a ransom in exchange for locked files, the system displayed a blue-screen of death and repeated reboots.
The phenomenon was undoubtedly disappointing for organizations that found their systems to make continuous restarts but at least were not infected by ransomware.
This does not mean that Windows XP is not vulnerable, as this operating system remains a popular target for cyber criminals who are trying to exploit the weaknesses of unaware systems.
WannaCry caused chaos across the globe, and the identity of the attackers remains unknown. Security companies such as Symantec and Kaspersky have linked the attack with the Lazarus team, which is believed to have acted for North Korea.
Meanwhile, the linguistic analysis of ransom notes that appeared to victims of malware suggests that the writer or at least the one who wrote the ransom note was Chinese.





