Όσοι προσπάθησαν να δουν την Πέμπτη την Washington Post από κάποια κινητή συσκευή, τους υποδέχτηκαν pop-up μηνύματα από την γνωστή χακτιβιστική ομάδα Syrian Electronic Army (SEA).
One of the texts has told visitors that the page has been violated, while others have been propagandistic about military operations in Syria and Yemen.
In fact, the web server της εταιρείας και η ιστοσελίδα δεν παραβιάστηκαν. Οι hackers κατάφεραν να εμφανίζουν τα μηνύματα τους μέσω της υπηρεσίας Instart Logic, ένα δίκτυο διανομής περιεχομένου (CDN) που χρησιμοποιεί η εταιρεία.
So those users προσπάθησαν να έχουν πρόσβαση από τα κινητά τους στην ιστοσελίδα της Washington Post ανακατευθυνόταν αυτόματα σε μια διαφορετική ιστοσελίδα που ελεγχόταν από τους hackers. Όλο αυτό το διάστημα η γραμμή διευθύνσεων του προletterbrowser showed that you were on the correct website.
According to the newspaper, the site was under the control of hackers for about 30 minutes and no damage was caused.
Shailesh Prakash, head security of the Washington Post, said the attack affected "the mobile site" but that it did not affect any of the published articles.
Kenn White, a computer scientist in North Carolina, was able to get the JavaScript code used by hackers to display the following alerts:
“You've been hacked by the Syrian Electronic Army!”
"US govt is training the terrorists to kill more Syrians."
"Saudi Arabia and its allies are killing hundreds of Yemens people everyday!"
"The media is always lying."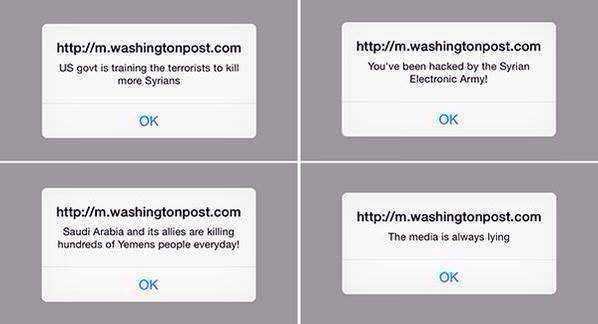
The offense had no other consequences, Syrian Electronic Army could easily (if they wanted) direct the company's visitors to a website that distributes malicious software.
But this group of hackers does not get used to such actions, since their motivation is not economical.





