Everyone has heard of it Bitcoin and for Blockchain but maybe they do not know exactly what they are and how they work. With this article we will try to enlighten you on the above concepts.

First of all, to do something that can be misunderstood. Bitcoin is not it Blokchain but not the reverse. There are two different things. Bitcoin is a digital coin based on Blockchain technology.
Well, rightly, you guessed, Blockchain is a technology, a digital method, a way of recording data, a whole philosophy if you want, which when it appeared almost changed the way of thinking in many human activities. And as you may have already heard, Bitcoin may well be eliminated, Blockchain never. It has come and will remain for a very long time. Let's go see.
What is Blockchain?
Blockchain is literally a digital calendar that is virtually impossible to breach. Although it can be applied to many human activities, we can now see it as an example in financial transactions since it first appeared in the Bitcoin digital currency.
For History
It first appeared in January of 2009 by someone or a group called Satoshi Nakamoto. It is still unknown today who or which group is hiding behind this name.
What exactly does it do?
Let's imagine that you are in Athens and you want to send money to a friend of yours in Giorgos, who is in Crete. To understand our example let's go back in time and imagine that we are in 2008. There was no Bitcoin and neither were digital transactions. So walk up to the bank you and tell the cashier to take money from my passbook and send 100 euros to Giorgos in Crete.
The Treasurer checks if you own 100 Euros and if he finds them sends an order to be deleted from you and transferred to George's bank account. Then you inform George by phone, and he's delighted to go to his bank to collect 99,50 euros. The bank naturally holds a commission of € 0,50 for its effort. But do not be lucky. 0,50 is not the actual bank profit. Probably these are the fewer.
The bank gains by holding a diary that records the entire transaction. That on February 31, Tade sent 100 euros to the poor. She did not naturally send the 100 euros to George but simply recorded the transaction and gave the order to her branch or another bank in Crete, to pay the money to George. This means that our entire financial system is based on 5-10 banks, which we trust to manage and keep a trading log.
And if you are wondering what the problem is, we report that banks are operating in a transaction as intermediaries and with the logic of being very limited in number, makes us deeply dependent on them. Would not it be better to be able to trade without intermediaries such as banks? So what did Satoshi Nakamoto think when he discovered Blockchain.
First of all, Blockchain wants more than 3 people to work. Let's make an example with 5 people. These 5 decide to make a separate currency and some transactions with it. They realize that in order for the new currency to stand on its own two feet they have to monitor the flow of funds and one person - let's call him George - decided to keep a list of all the actions in a diary. The calendar is empty at the beginning but on the 1st day the following transactions were recorded:
- a. Kostas gives Manoli 100 coins
- b. Manolis gives George 150 coins
- c. George gives Dimitris 50 coins
- d. Dimitris gives Maria 20 coins
One of the five, say, Dimitris, wickedly thinking, decides to steal and go secretly to George's calendar and makes a change:
- a. Kostas gives Manoli 100 coins
- b. THE
ManolisDimitris gives George 150 coins - c. George gives Dimitris 50 coins
- d. Dimitris gives Maria 20 coins
Hash Mode
George noticed that someone had altered his diary and decided to stop it. She found a program called Hash that converts text into a set of numbers and letters as in the table below.
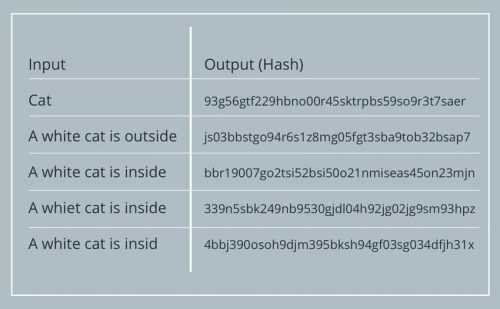
The hash is a series of numbers and letters generated by a function. A hash function is a mathematical function that takes a variable and random number of characters and converts it into a string with a fixed number of characters. Even a small change to the original string creates a completely new hash. In a nutshell, the hash function accepts a number or a word or mixed letters with numbers or a sentence or an entire text, and as a result it produces a fixed length set of numbers and characters. Reverse mathematical resolution is not possible. That is, if someone who knows the hash can not find, or know the original text. The hash function is one-way, from text to hash.
Happy that George found a solution to his problem, after each registration, he introduced a hash that represented this registration. The new calendar was now as follows:
- a. Kostas gives Manoli 100 coins
29f3e7d933dfa9aa6f28b56e2676197d - b. Manolis gives George 150 coins
e20a38184188d3cde4b31ba136ab7f9a - c. George gives Dimitris 50 coins
d1ce2082961d697493faef24ee227a23 - d. Dimitris gives Maria 20 coins
160830a92d8bf4634d24201092946d2e
Dimitris decided to change the entries again. At night he went to the calendar, changed the file, saw that there was a hash next to the transaction and created a new hash based on the altered transaction.
- a. Kostas gives Manoli 100 coins
29f3e7d933dfa9aa6f28b56e2676197d - b. Manolis gives George 150 coins
e20a38184188d3cde4b31ba136ab7f9a - c. George gives to Dimitris
505 coins
d1ce2082961d697493faef24ee227a23
2e9252e9b7ac9183cc32af4ee373acc4 - d. Dimitris gives Maria 20 coins
160830a92d8bf4634d24201092946d2e
George, the next day, remarked that someone had altered the diary again. He decided to complicate the recording of each transaction. After each record, it introduced a hash created by the transaction registration + the last hash. So that each entry depends on the previous one.
- a. Kostas gives Manoli 100 coins
29f3e7d933dfa9aa6f28b56e2676197d - b. Manolis gives George 150 coins - 29f3e7d933dfa9aa6f28b56e2676197d
5c1e8fc1a84af70c4847706f3e5af054 - c. George gives Dimitris 50 coins - 5c1e8fc1a84af70c4847706f3e5af054
9960e5687176870d6c32d10758ba8f07 - d. Dimitris gives Maria 20 coins - 9960e5687176870d6c32d10758ba8f07
62a154626243b2f41bb79e673a8d6948
If Demetris now tries to change the record, he has to change the hash in all previous entries. But Dimitris was stubborn and really wanted to make money easily. So she ate all night counting all the hashes and making new ones.
Nonce
But George did not want to give up. Decided to add a number after each transaction registration. This number is called "Nonce". The nonce should be selected so that the generated hash of each transaction ends in two zeros. Not an easy process, as it requires painstaking and endless tests until the right nonce is found.
- a. Kostas gives Manoli 100 coins 451
29f3e7d933dfa9aa6f28b56e26761900 - b. Manolis gives George 150 coins 13 – 29f3e7d933dfa9aa6f28b56e26761900
5c1e8fc1a84af70c4847706f3e5af000 - c. George gives Dimitris 50 coins 467 – 5c1e8fc1a84af70c4847706f3e5af000
9960e5687176870d6c32d10758ba8f00 - d. Dimitris gives Maria 20 coins 56 – 9960e5687176870d6c32d10758ba8f00
62a154626243b2f41bb79e673a8d6900
Now, to make new, corrupted files, Dimitris will have to spend hours and hours choosing the Nonce for each line. The most important thing in this encryption system is that not only people, but the fastest computers can not account for nonce so fast.
Nodes
Later, George realized that there were too many records and that he could not keep the diary forever because he was just a middleman, a bank. So when he wrote 2.000 transactions, he turned them into a spreadsheet of a page and gave them to Maria. Maria checked out all the transactions and found them right.
George spread the diary to over 5.000 computers, which were all over the world. These computers are called Nodes (nodes). Each time a transaction is made, it is sent to all nodes and must be approved by them. Each node checks the validity of the transaction. Once a node controls a transaction that is created, there is a kind of electronic vote, as some nodes may think the transaction is valid and others think it is a scam.
The nodes listed above are computers. Every nobe has one copy of the digital calendar, in other words Blockchain. Each nobe checks the validity of each transaction. If the majority of nodes say that a transaction is valid then it is registered in a block. So now the issue becomes much safer but also much freer. If Dimitris, who also owns a Nobe, changes an entry, all the other computers that have the original hash would see the change. They would not allow the change to happen since the majority would say that it is not right and Dimitris would be excluded from the Nobe network.
Block
This spreadsheet created by George is called a block. Each Block contains 2.000 records. When records arrive at 2000, the block is filled, closed, sealed and placed immediately after the previous Block. That is, it forms a chain with all the previous Blocks existing since the beginning of the coin. At the same time, a new Block Blank is created. The entire Block family is the blockchain (the block with the blocks). Each nobe has a copy of Blockchain.
Blockchain is updated every ten minutes. This is done automatically. No master or host computer instructs computers to do so. Once the spreadsheet is updated, it can no longer be changed. So, it's impossible to hack it. You can only add new entries to it. And the spreadsheet is updated at the same time on all computers in the network.
What if there are many who want to steal? If the insolvent formulas in our example, which are all nobe and everyone has a copy of the transaction, become three (more than half), then the protocol will collapse. The setting is known as “51% Attack ”. In the event that the majority of network nodes decide to steal the rest of the network, the protocol will fail based on its design because it simply relies on the majority. The blockchain will not be the right one, but it will be modified in the interest of the malicious. Although unlikely to be a scenario, it is one of the few (if not the only) Blockchain security vulnerabilities.
Stamping the block and evidence of work
By filling a block with transactions the nodes will have to seal before joining the blockchain. So the 5 nodes of our example just realize that a block is filling trying to find a specific number (nonce) which when attached to the block transaction list along with the previous block hash and all this is given at the input of the hash function, will result in the created hash ending in two zeros.
It is not an easy process and requires computing power and power consumption. As soon as one of the 5 finds this number, he announces it to the other 4. They check the number and if they agree, they all place it on their computer, seal the Block and adapt it to the Blockchain. The task of finding and verifying this is called "Proof of Work ”Or as an acronym PoW. But what if someone disagrees? The majority just wins and the one who disagrees has to delete his own wrong block, download the block from the others and save it to himself.
The person who found the special number wins a compensation fee for computer power, which now stands at 12,5 BTC, and thus becomes the first miners. That's why all the nodes do not expect the nonce to be ready, but they try mining to win the reward.
Important points to keep in mind:
- A Blockchain is a type of calendar or spreadsheet that contains transaction information.
- Each transaction creates a hash.
- A hash is a series of numbers and letters.
- Transactions are listed in the order in which they appeared. The registration order is very important.
- The hash is dependent not only on the transaction but also on the previous transaction hash.
- Even a small change in a transaction creates a completely new hash.
- Nodes check the hash to make sure that a transaction has not changed.
- If a transaction is approved by the majority of nodes then it is written in a block.
- Each block refers to the previous block and together they make the blockchain.
- A Blockchain is effective as it is spread over many computers, each of which has a copy of Blockchain.
- These computers are called Nodes.
- Blockchain is updated every 10 minutes.
Now imagine this whole process of transactions, which eliminates intermediaries, not limited to currency but as a technique spread to all human actions. Imagine seeing this in many traditional sectors such as: banking, insurance, entertainment, government and others. Although it is still in an early stage of development, blockchain technology usesalready in real life for cryptocurrencies, government data storage, etc. and many in both the private and public sectors are exploring potential use cases.
If you take it a step further, at a political-philosophical level, think of many activities going beyond the state control of each country and relying on a blockchain shared in nodes that are scattered around the globe. For example, a record and identification of all the inhabitants of the Earth, which no state would have the data or a registration and issue of car registration plates.
Wallets, digital signatures
George gathered the remaining 4 and made a team of 5 people. He has to explain the new currency to them. Giorgos was really honest (not like Dimitris who tried to steal), he confessed to the team the initial mistakes he made and apologized deeply. To prove his honesty, he gave back their coins to Maria and Manolis.
George explained why this can never happen again. He decided to implement something called a digital signature to confirm each transaction. But first, he gave everyone a wallet.
What is wallet?
A wallet is a series of numbers and letters, such as 18c177926650e5550973303c300e136f22673b74. This is an address that will appear in various blocks within the Blockchain as the transactions are made. There are no visible records of who did what transaction with whom, only the number of a wallet. The address of each particular wallet is also a public key.
A wallet is basically a document that contains a public address that can be used to download Bitcoins and a private key that allows you to spend or transfer Bitcoins stored at that address. A wallet can be created using services such as BitAddress ή Bitcoinpaperwallet which allow users to create a completely random Bitcoin address and a private key to it.
Digital signature
To make a transaction you need two things: a wallet, which is basically an address, and a private key. The private key is a series of random numbers, but unlike the address, the private key must be kept secret.
When someone decides to send coins to anyone else, they must sign the message containing the transaction with their private key. The two keys system is at the center of encryption and its use was preceded by the existence of Blockchain. It was first proposed in the 1970 decade.
Once the message is sent, it is transmitted to the Blockchain network. The network of nodes then checks the message to make sure the transaction it contains is valid. If it confirms the validity, the transaction is placed in a block and then can not change any information about it.
Principles of Blockchain
Shared database
Blockchain is basically a database and each Blockchain node has access to the entire Blockchain. No node or computer modifies the information it contains. Each node is able to validate the Blockchain records. All this is done without one or more intermediaries controlling everything.
It is architecturally decentralized, and there is no case for one or more failure points that would destroy the Blockchain.
Peer-to-Peer Transfer (P2P)
According to the first principle, communication between nodes always takes place directly between them and not through a central node. Information about what happens in the Blockchain is stored at each node and then transferred to neighboring nodes. Using the P2P transmission system, information is disseminated over the entire network.
Transparency but pseudonym
Anyone who has access to Blockchain is able to see each transaction and its hash value. Someone using the Blockchain can be anonymous if he or she wants it or can give his identity to others. All you see in Blockchain is a transaction file between your wallet addresses.
Εγγραφές
Once a Blockchain transaction is logged and Blockchain is updated, it is impossible to convert this block. This is because this transaction log is associated with the history of each previous one. Blockchain files are permanent, chronologically sorted and available to all other nodes.
Why is it impossible to disable Blockchain?
Since there are nodes around the world, it is almost impossible to occupy the entire network.






Good job my friend. Really popular and complete.
All I will add is this: since the banks - with this process - are left out of the game, they are now trying to enter the world of intangible currencies, so that they can also receive commissions from them.
In short - once again - they are trying to become the parasites of the economy.
Vibrant and complicated !!!! the whole system that you managed to show us very well.
One of my remarks: The two key system (you refer to it as a two key system - it is probably two keys)
Top article!
ps: 31 February from when? :)
the author of the article and his bravo. I understood the irrelevant right away!
I just now fully understand the function of the blockchain.
A great thumbs up to the article editor!
Thanks.