WiKey: Scientists at Michigan State University and Nanjing University in China discovered that it is theoretically possible to accurately detect keystrokes using Wi-Fi signals from a simple router.
Researchers report that in environments with minimal signal interference, an attacker could use the malfunctions he records on WiFi signals from the router to detect the keys being pressed on a laptop computer, thus bypassing passwords.
For their experiment, they called WiKey, researchers used off-the-shelf equipment such as a TP-Link TL-WR1043ND WiFi router and a Lenovo X200 laptop.
To capture the tiny changes in Wi-Fi signals, researchers used the MIMO's Multiple-Input and Multiple-Output router, a set of features that allow each of the antennas to send multiple Wi- Fi on the same channel.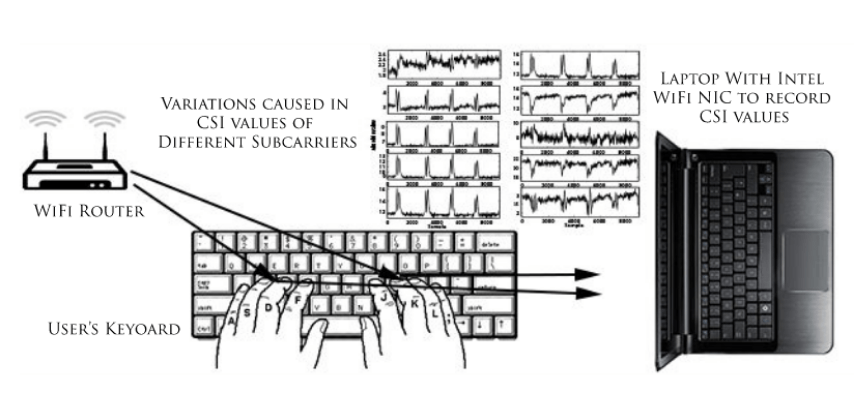
Researchers used these multiple Wi-Fi signals, which they were able to collect with a scanner and scan the room to create an environment map.
Because of this, WiKey only works in rooms with minimal movement and from one to no human presence.
When someone starts typing, WiKey is able to pick up the disturbances in Wi-Fi signals caused by the movement of the user's fingers on the keyboard.
The team managed to develop a special algorithm to locate the keys from the drive and retrieve the text typed on the computer.
In an environment with little traffic and a slow-typing user, the accuracy of the system was 97,5 percent. In a real environment, with Wi-Fi signals and faster user typing, the accuracy of the system was between 77,43 percent (30 samples) and 93.47 percent (80 samples).
Despite the lower precision, many malicious users will have more chances of success if they know about three-quarters of your password.
One drawback is that in a real-world scenario, a target that is not alone (2-3 people with a laptop one close to each other) makes the attack useless, as WiKey is not able to distinguish the target.
You can download the research paper titled Keystroke Recognition Using WiFi Signals (PDF) by Kamran Ali, Alex X. Liu, Wei Wang, and Muhammad Shahzad.





