New leaked secret documents reveal that the CIA targets and violates home and public wireless routers for years in its attempt to conduct illegal surveillance.
The leaked documents are part of an ongoing series of leaks circulating WikiLeaks website, revealing the work of the elite of the CIA hacking team, called the Engineering Development Group.
Dozens of files include user and installation guides, manuals, and other "secret" maps and graphs that reveal several suites of hacking tools that allow the organization to conduct targeted network and computer exploitation.
One of the tools is called CherryBlossom, and allows the service to monitor a target's internet activity, redirect it Browser, detect email addresses and phone numbers and more.
Routers or routers remain a prime target for both information services and hackers, because they act as a central Internet connection point as well as on entire networks. What makes routers a very attractive goal is that safety flaws that make it easy to exploit are not often revealed, and of course there are not so many updates.
According to a document dating back to 2010, by mid-2012 the CIA had developed implants "for about 25 different devices from 10 different manufacturers", including its routers Asus, Belkin, D-Link, Linksys and Netgear.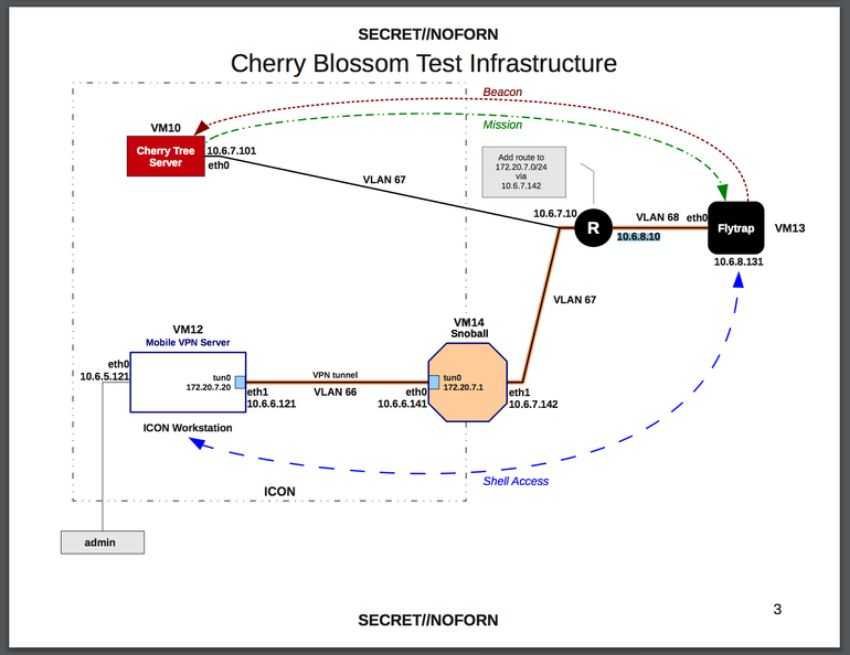
It is unclear whether malicious implants are still functioning or withdrawn.
Please be reminded that Wikileaks released documents in the Vault 7 series from 7 March, exposing more and more Coca-Cola Hacker tools.
"Year Zero"CIA exploits popular hardware and software.
"Weeping Angel"The spying tool that the service uses to penetrate smart TVs, turning them into disguised microphones.
"Dark Matter"Exploits targeting iPhones and Mac.
"Marble” the source code of a secret anti-forensic framework. It is essentially an obfuscator used by the CIA to hide the real source malicioussoftware.
"Grasshopper"A framework that allows the information service to easily create custom malicious software to violate Microsoft Windows and bypass any virus protection.
"Archimedes"- a MitM attack tool allegedly created by the CIA for targeting computers within a local area network (LAN).
Scribbles” a piece of software designed to add 'web beacons' to classified documents to allow intelligence to monitor leaks.
Athena:is designed to be able to gain complete control over infected Windows computers, allowing the CIA to perform many functions on the target machine, such as deletion data or installing malware, stealing data and sending it to CIA servers.
CherryBlossom tool that monitors a target's internet activity, redirect the program browsing, να ανιχνεύει διευθύνσεις ηλεκτρονικού ταχυδρομείου και αριθμούς τηλεφώνου και πολλά άλλα, μέσω του router





