The Microsoft Defender and Microsoft Edge on Windows 10 will automatically block potentially unwanted applications (PUA from potentially unwanted applications) by default from this month.
Since Windows 10 2004, that is May 2020 update, Microsoft has added the new "Block unwanted applications" setting Windows security that makes Microsoft Defender block these types of applications.

Since its release, this feature has been disabled by default, but starting this month, Microsoft will begin blocking PUAs when they are automatically detected on each computer.
"From the beginning of August 2021 we will start activating it by default to make it easier for you to keep your systems running at their best," Microsoft said in a brief statement today.
Windows 10 users who don't want to block PUAs by default can turn it off mode ανοίγοντας στην οθόνη ρυθμίσεων την καρτέλα Ασφάλεια των Windows. Κάνοντας κλικ στο στοιχείο Έλεγχος εφαρμογών και προγράμματος περιήγησης επιλέξτε τις ρυθμίσεις προστασίας βάση φήμης.
On the protection settings screen, you can turn off the "Block potentially unwanted applications" setting.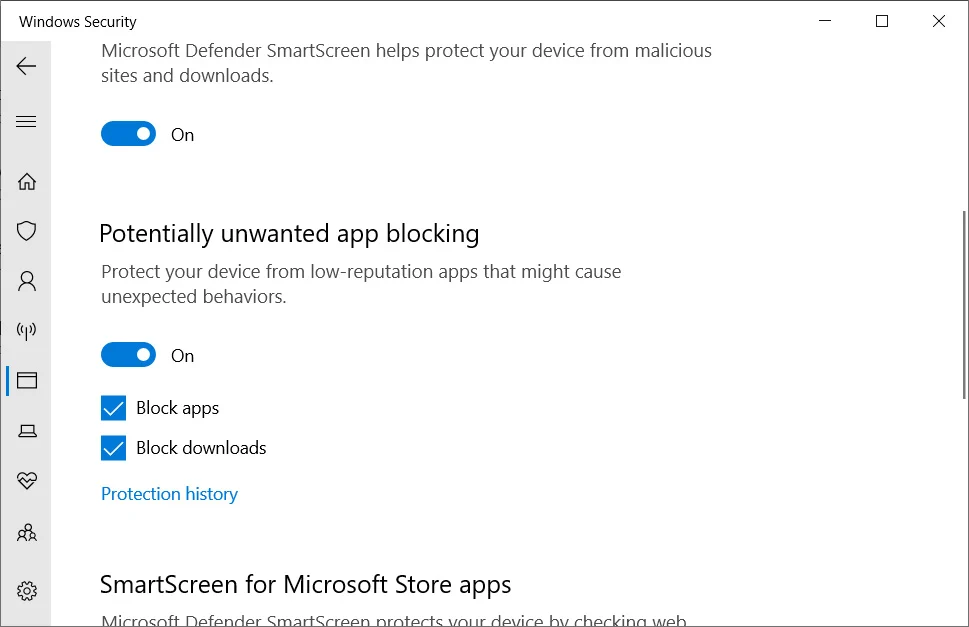
The “Block potentially unwanted applications” option will enable Microsoft Defender's PUA scanning and blocking feature. “Block downloads” will check if the “Block potentially unwanted apps” setting is enabled in Browser Microsoft Edge. If enabled, SmartScreen will block PUAs and PUPs when they are downloaded.
What are these applications?
Many of the unwanted applications, either PUA or PUP, are not malware, but they are very close.
They are usually created by legitimate companies that go beyond the limits and in most cases have unwanted behaviors on users' computers.
These programs are from browser extensions, adware, programs that send unauthorized usage data, system cleaners, anti-virus programs that use false positives, or programs that do not provide the promised functionality.
Microsoft's criteria for designating a program as a potentially unwanted application are as follows:
Advertising software: Software that displays ads or asks you to respond to queries for other products or services in completely different software. They contain software that inserts ads on web pages.
Torrent Software: Software used to create or download torrents or other files used specifically with peer-to-peer file sharing technologies.
Cryptomining Software: Software that uses your device's resources to extract cryptocurrencies.
Commitment software: Software that offers the installation of other software that does not have a digital signature from the same company. Also, software that offers the installation of other software designated as PUA based on the criteria described in this document.
Marketing software: Software that monitors and transmits user activities to applications or services for marketing research.
Avoidance software: Software that tries to avoid detection by security products, as well as any software that behaves differently in the presence of security products.
Malicious software: Software that identifies trusted security providers with their security products.
Unfortunately, there is also useful software that according to Microsoft meets these criteria and will be detected by the Microsoft Defender PUA blocker.
For example, mining applications and torrent software are not usually malicious, but can be detected by Microsoft Defender.
In these cases, it is recommended that you create exceptions in Defender to prevent these files from being quarantined instead of disabling the entire feature.





