Over one third of all webpages on the Internet are powered by one of these four key open source platforms: WordPress, Joomla, Drupal, and Magento.
This makes life of hackers much easier as they can simply focus on exploiting vulnerabilities on a platform of them, or one of the most popular plugins and extensions they use.
Sucuri, a security company focused on detecting cyber attacks and restoring hacked websites, recently released fresh statistics data for the hacked websites.
Based on Incident Response Team reports and Malware Research Team of the company, in the first quarter of this year, 78% of successful compromises were on websites with WordPress. Websites using Joomla reached 14%, Magento 5%, and Drupal 2%.
Magento's e-commerce sites were hit with exploits that allowed remote code execution in February of 2015, and an XSS hole that could lead to a violation of the online store in January of 2016. Apparently, not all administrators regularly update their installations.
In fact, webmasters with Magento are the worst of their kind: 97% of Magento installations, according to Sucuri experts, were old versions at the time of cleaning. WordPress admins on the other hand were better, since "only" 56 percent of the installations were in an older version: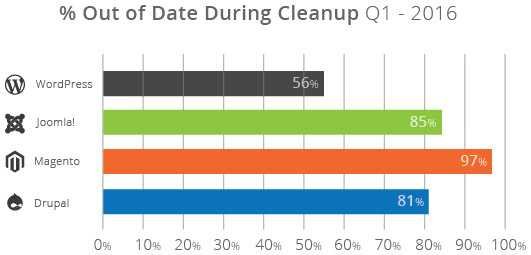
"The top three software vulnerabilities that affected most websites in the first quarter were through the RevSlider, GravityForms and TimThumb plugins," the researchers said.
"For all three of these plugins there was a fix available for at least a year, while for TimThumb it existed many years ago (since 2011).
The problem with RevSlider, in particular, is that it's built into WP themes, and many of the platform's users don't even know they're using it.
Magento websites are usually infringed by information leaked to customers.
For the remaining platforms, SEO Spam (31%, and this percentage continues to increase), drive-by-download infections (60%), hacking tools (exploit or DDoS tools), and phishing. Defacements by hacktivists were barely noticed.
In two-thirds of the cases, Sucuri's cleaning team discovered backdoors in websites, as attackers wanted to be sure they could get access and after cleaning the hacked website.
"On average, we clean up 132 files per hacked website," say the researchers.
"This shows how deeply malware can be embedded within a website. The above also explains why Google reports a 30% recurrence rate, a rate measured through webmaster tools. ”
Here we have to mention that WordPress sites, although they first come in the rate of infections for us can be considered the most reliable. Of course, always be in the latest update.





