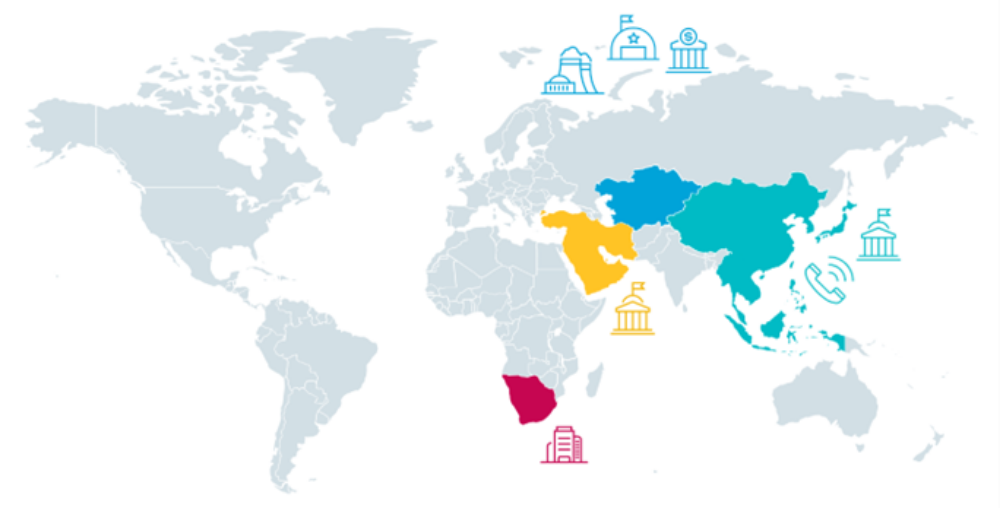
ESET researchers uncovered a hitherto unknown team cyberespionage they called Worok. The Worok group has attacked various "high-profile" public and private sector organizations in industries such as telecommunications, finance, shipping, energy, and defense. The targets are mainly in Asia, the Middle East and Africa.
To attack their targets, the Worok team develops its own cyberespionage tools, while also leveraging existing ones. So the team has used ProxyShell vulnerabilities to gain initial access in some cases, while the PowHeartBeat backdoor they use has various capabilities, including command/process execution and upload and download files.
According to ESET telemetry, the Worok group has been active since at least 2020 and continues to be active today.
"We have strong suspicions that malware operators are seeking to extract information from their victims because they are targeting high-profile companies in Asia and Africa, focusing on public and private organizations, with a particular emphasis on government agencies," says the researcher ESET Thibaut Passilly who spotted the Worok team.
In late 2020, Worok targeted governments and corporations in many countries. From May 2021 to January 2022, she took a hiatus from her activities, but returned in February 2022 doing attack:
• To an energy company in Central Asia and
• In a public sector enterprise in Southeast Asia
"Although the information we have at this stage is limited, we hope that the publicity given to this group will encourage other researchers to share information," adds Passilly.
For more technical information about the Worok team, see the blogpost “Worok: The big picture”At WeLiveSecurity.
Illustration of Worok's target areas and sectors