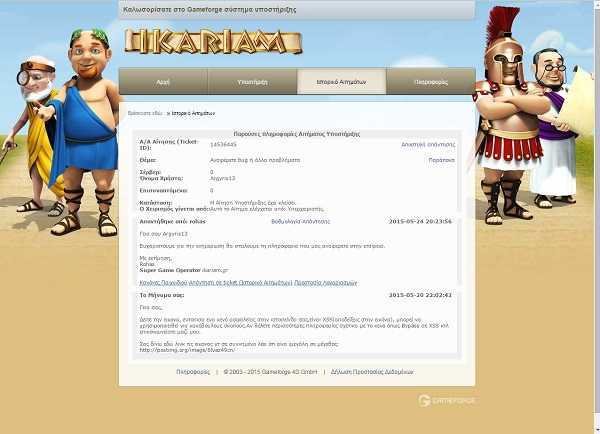
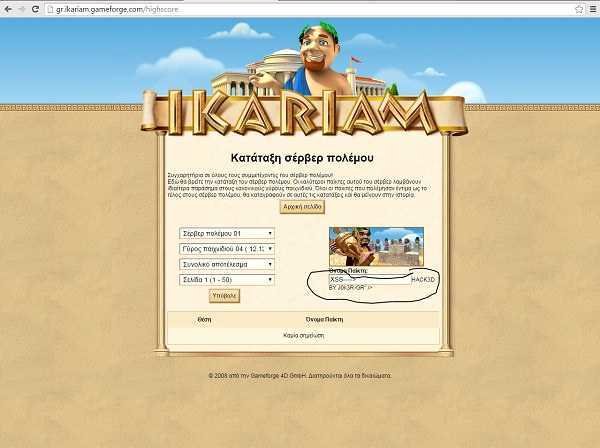
The reader of iGuRu.gr, J0k3R-GR, has notified us of an XSS weakness in the browser game ikariam.gr. We quote the notification e-mail sent to the site's managers.
"Look at the image, I found a security gap on your website, it's XSS (image proof), it can be used for malicious purposes."
And the evidence of vulnerabilityς
The image link to a higher resolution
http://postimg.org/image/
Continuing J0k3R-GR reports:
The ones vulnerabilities XSS we take advantage of them by inserting HTML or Javascript into a page. This code does not filter and can cause corruption in the site's code.
Thus a malevolent user can cause:
script>