A new targeted attack was detected through TeamViewer, which aimed at stealing financial information from government and economic targets across Europe and beyond.
Check Point researchers announced on Monday that the attacks were specifically aimed at government and financial officials, as well asfaces from various embassies in Europe, Nepal, Kenya, Liberia, Lebanon, Guyana and Bermuda.
The attack began with a standard phishing email containing a malicious attachment claiming to be a “highly privacy” document from the United States.
The subject line said “Military Financing Program” and the .XLSM document had it logo of the US State Department.
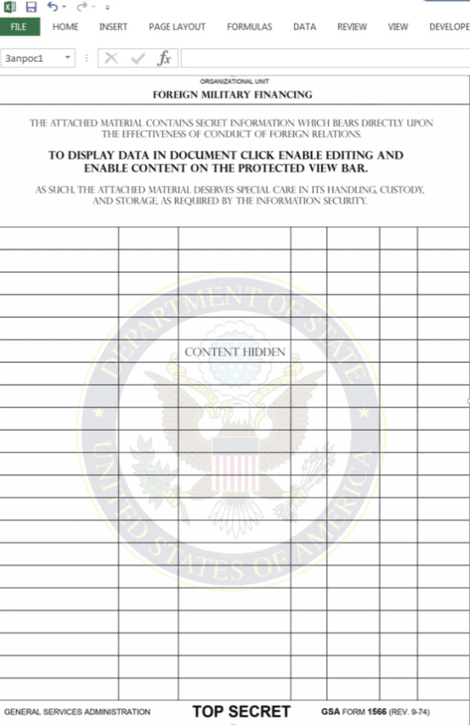
So if someone opened the document and enabled the macros, two would come out archives – a regular AutoHotkeyU32.exe program and a malicious TeamViewer DLL.
AutoHotkeyU32 was used to send a POST request to the intruder's command and control (C&C) server, but also to download more malicious scripts capable of capturing screenshots of the target computer, stealing information, and then sending it to the attacker. .
TeamViewer is often used by businesses for remote PC access. However, due to its capabilities, the software is also used by scammers to gain access to remote systems.
The malicious parchange with the TeamViewer DLL provided attackers with modified functionality, and hiding each connection to TeamViewer. So victims didn't know someone was logged into their computer.
The main targets of this attack as mentioned above were public financial sector players and according to the researchers the would-be hacker was a Russian.
_________________
- GR and EL domains: Attack to the Greek Internet Name Registry
- Windows 10 Fall Creators support fee immediately upgrade
- Mathesis: Ancient Greek Technology 1 (Basic Technologies)
- Edge with Chromium allows video streaming on 4K
- Mark Zuckerberg: help from regulators & governments





