- Check Point Research (CPR) has uncovered three recent malicious campaigns of one of the most prevalent malware on the market – Agent Tesla. These operations were targeted against organizations in the US and Australia and used as bait purchases of goods and delivery of orders
- During the investigation, we discovered that these threat actors had a database of 62.000 emails, including individuals and organizations from different categories
- In addition to campaigns originating from victim companies, the group maintains a large number of servers, which are used to protect their identity
- Despite the efforts of the threatening factors to maintain their anonymity, CPR revealed their true identity and source of origin, reconstructed their steps in the attacks carried out, with continuous monitoring of their activity
Well known malware
The Agent Tesla malware is an advanced remote access trojan (RAT) that specializes in stealing and exfiltrating sensitive information from infected machines. This malware can collect various types of data, including keystrokes and login credentials used in browsers (such as Google Chrome and Mozilla Firefox) and in email clients used on infected machines. The agent tesla has a notorious history of repeatedly being included in monthly reports of the top 10 malware families since 2020.
The Source: Two Cybercrime Factors
CPR has identified the activity of 2 cybercrime actors behind the Agent Tesla operations with evidence suggesting they are linked:
– “Bignosa” (main threat actor)
– “Gods”
The main perpetrator, “Bignosa”, appears to be part of a group that operates malware and phishing campaigns targeting organizations, as evidenced by email databases of US and Australian businesses as well as private individuals. “Bignosa” used Cassandra Protector for obfuscation and various malware families, signaling a secondary level of cybercrime tactics and tools.
With a dual identity, “Gods”, also known online as “Kmarshal” who earlier participated in phishing attacks, later switched to malware campaigns. He also demonstrated skills in web design and phishing operations.
During our investigation, we traced the links between various clues, made connections and secured the identities of these two threat actors, including their photos from their LinkedIn pages. They appeared to be of African descent, with one of them holding legal missions within his business.
Their technical level seemed to be different, with “Gods” being more experienced, while both communicate via Jabber, an open technology for instant messaging, with “Gods” providing assistance to “Bignosa” on matters of varying difficulty. . Using Agent Tesla, however, was no obstacle for either of them. We also tracked their malicious activity behind Agent Tesla and shared all discoveries with the relevant law enforcement agencies.
Recent campaigns
Malware campaigns were meticulously prepared, rather than just launching spam with a simple click. Using phishing emails with topics related to the purchase of goods and the delivery of orders, the attackers attempted to trick victims with a social mechanism into initiating the malware infection. These emails were sent from the servers deployed by the threat actors right before the campaigns with the main purpose of anonymity. The malware itself was protected by Cassandra Protector, adding anti-detection capabilities to make it harder to catch.
The diagram below shows the timings of the preparation and execution steps of these attacks: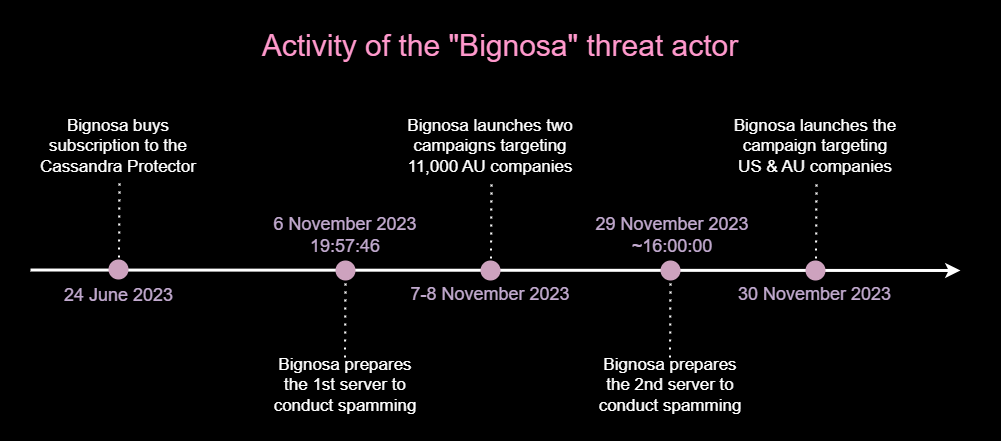
The basic scheme of the first two functions is shown in the diagram below:
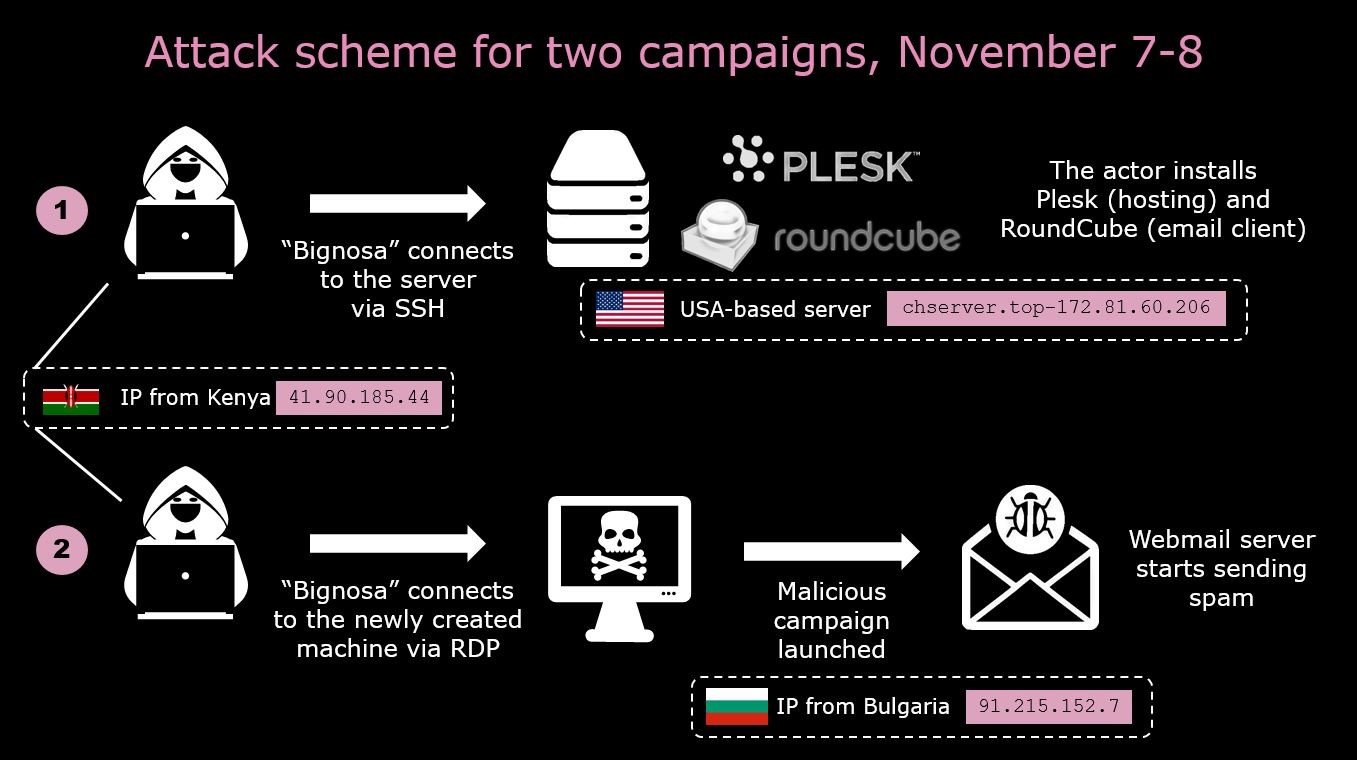
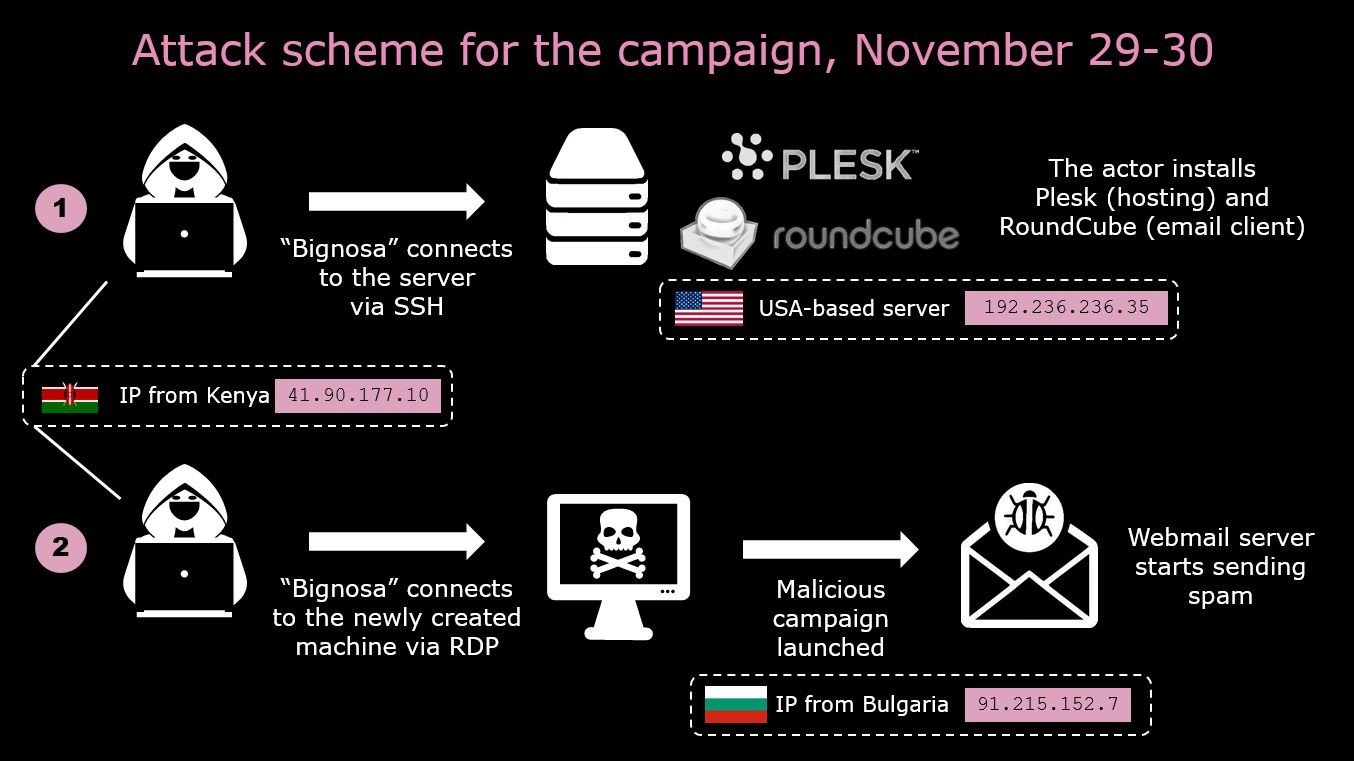
The main scheme for the third attack is similar to the first, except for the different addresses used on the attacking machines:
To get more information and follow our investigation with full details on the threat actors discovered, visit the Link
Conclusions and recommendations
This research highlights the importance of cyber security vigilance. The identification of these threat actors was made possible through the meticulous analysis of digital fingerprints, demonstrating the power of digital forensics.
To mitigate the risks of being affected by such threats, it is important to:
– Keep operating systems and applications up-to-date through timely patches and other means.
– Be wary of unexpected email messages with links, especially from unknown senders.
– Raise employee awareness of cyber security issues.
– Consult security experts for any doubts or uncertainties.