Windows Group Policy is a powerful tool that lets you configure many aspects of the operating system. Most settings are designed to give computer administrators the ability to monitor and control typical accounts.

If you manage computers in a company environment or if you manage multiple accounts in your home, then you should know the capabilities and benefits of your Windows to properly control the use of your employees' computers and your family.
Below we will see 8 tweaks for Windows 10 that we consider important to know and will certainly make it easier for you to work of the administrator.
Note: H processinggroup policy is not available in the standard and home version. You must have the Pro or Enterprise edition to use it.
How to access the Group Policy Editor Windows
First, make sure you are logged in as an administrator before attempting to get into Group Policy editing. There are many ways to access Group Policy Editor. For convenience, we suggest you open the "Run" window of Windows (or press Win + R at the same time) and there write the word "gpedit.msc" and click OK.
Tweak 1. Record account logins
Through the policy group, you can force Windows to record all successful and failed attempts to connect to the computer from any user account. You can use this information to track who you log on to the computer and whether an unauthorized person has attempted to connect or not.
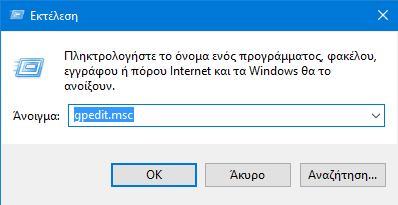
In the Group Policy Editor, scroll to the location below and double-click "Check Login Events".
Computer Settings> Windows Settings> Security Settings> Local Policies> Control Policy
Here, select both check boxes next to "Success" and "Failure" and click OK. Windows will start recording and keeping a log file.
To view these logs, you must have access to another useful Windows tool, Event Viewer. Open "Run" again and type "eventvwr" to open the Windows event viewer.
Go to "Windows Logs" and then to "Security". In the middle of the table, you should see all the recent events. Do not be confused by all these facts, all you need to find are successful and failed connections. Successful connections have "Event ID: 4624", and failed connections have "Event ID: 4625". Just look for these event IDs to find the links and see the exact date and time they were made.
Double-clicking on these events will show more details, along with the exact name of the linked user account.
Tweak 2. Disable access to Control Panel
The Control Panel or Control Panel is the center of all Windows settings, both for security and usability. However, these settings can be disastrous in the wrong hands. If you are dealing with a novice user who should be using the computer or if you suspect that someone may be "corrupting" these sensitive settings, then you should deny access to the Control Panel.
To do this, scroll to the site in Group Policy Editor User Settings> Management Templates> Control Panel and double-click "Block Access to Control Panel and Computer Settings".
Select the "Activate" option to deny access to the Control Panel. Normally the Control Panel option should be removed from the start menu and no one will be able to access it from anywhere, including the Run window.
All options in the Control Panel will be banned and access to them by any other method will cause an error.
Tweak 3. Forbid users to install new software
It can take you some time to clean a computer that is infected with malicious software. To make sure that users do not install infected software by any means, you will need to disable Windows Installer from Group Policy.
Navigate to Computer Settings> Administration Templates> Windows Components> Windows Installer and double-click "Disable Windows Installer".
Select "Enable" and then "Always" from the drop-down menu in the "Options" panel. Users will no longer be able to install new programs on the computer.
Tweak 4. Turn off removable storage devices
USBs as well as other forms of removable storage devices can be very dangerous for the PC. If someone accidentally (or deliberately) connects a USB-infected USB to the computer, it could infect the entire PC or could steal sensitive data.
To prevent users from using portable storage devices, go to User Settings> Administration Templates> System> Removable Storage Access, and double-click Removable Disks: Block Read Access.
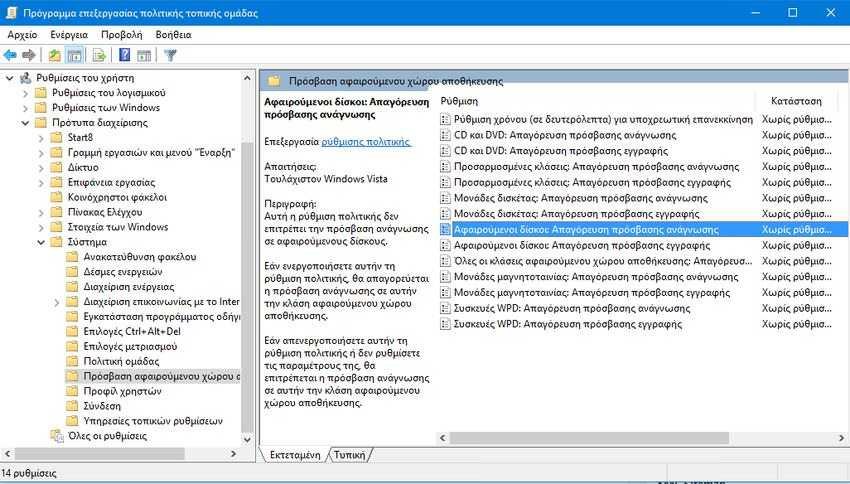
Enable this option and the computer will not read any kind of data from an external storage device. Additionally, there is an option below that is listed as “Removable disks: Deny access enrollments". You can enable it if you want no one to be able to write data to a removable storage device.
Tweak 5. Prevent users from starting specific applications
The policy group also allows you to create a list of applications that you will prevent from launching, that is, running on your system. It is a good setting to prevent users from "eating" their time with applications that are not approved by you. Go to User Settings> Administration Templates> System and double-click "Do not run specific Windows applications".
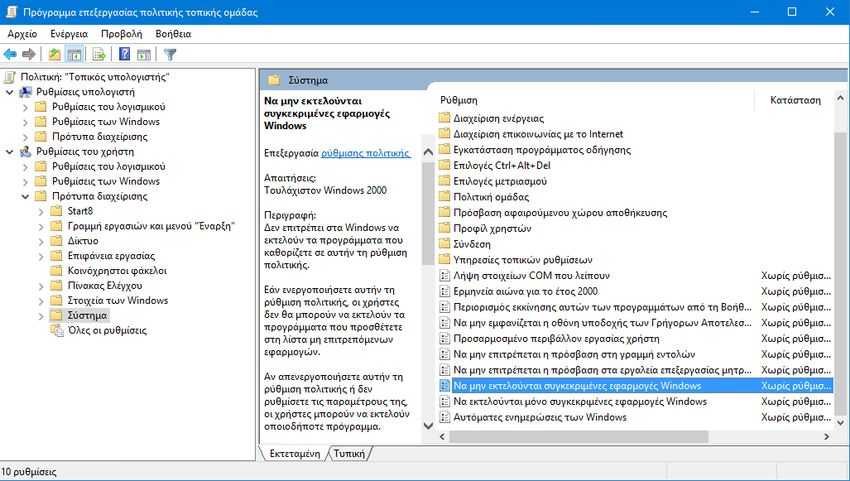
Select this option and click the "Show" button below to start creating the list of applications you would like to block.
To create the list, you must enter the executable name of the application along with an .exe at the end to block the application. For example, CCleaner.exe, CleanMem.exe or Launcher.exe. The best way to find the exact executable name of an application is to look in the application folder in Windows File Explorer and copy the exact name of the executable file (along with the ".exe" extension).
Enter this executable name in the list and click "OK" to start the lock. There is also in the group policy below the option "Run only specific Windows applications". If you want to disable all types of applications except specific ones, then use this option and create a list of the applications you want to allow. We would say that this Tweak is aimed at a really strict working environment.
Tweak 6. Disable Command Prompt and Windows Registry Editor
If the Dashboard is dangerous in the wrong hands, then the Command Prompt and the Registry Editor are a disaster. Both of these tools can easily make Windows unusable, especially Registry Editor, which could damage Windows so much that you would have to format.
If you are concerned about computer security and want to disable both Command Prompt and Windows Registry Editor, go to User Settings> Management Templates> System and double-click "Deny Command Prompt" and " do not allow access to registry editing tools ”. Just turn them both on.
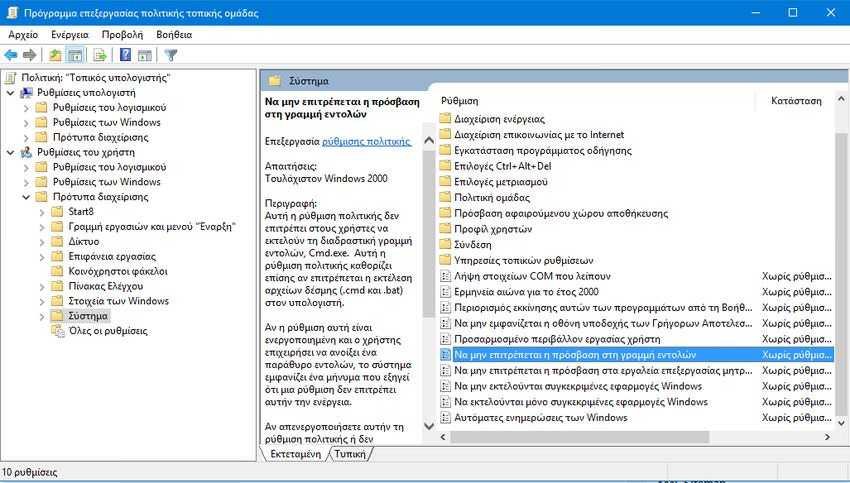
Tweak 7. Hide Partitions from the computer
If there is a specific disk with sensitive data inside the computer, you can hide it so users will not be able to see it. It is a good measure to keep users away, but should not be used as a method to protect data from prying eyes.
Go to User Settings> Administration Templates> Windows Components> File Explorer, and select "Hide specified drives in My Computer".
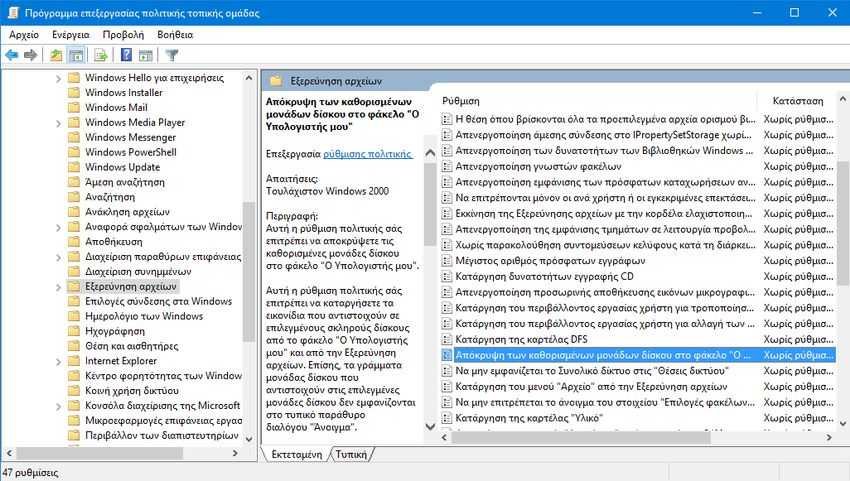
Once enabled, click the drop-down menu in the "Options" panel and select which disk you want to hide. The discs should be hidden as soon as you click "OK".
Tweak 8. customize the Start Menu and the taskbar
Group Policy offers dozens of tricks for the Start Menu and taskbar to customize to your liking. These tricks are ideal for both administrators and regular users looking for a way to customize the Windows Start menu and taskbar. Go to User Settings> Management Templates> Taskbar and Start Menu and you'll find all the tweaks along with an explanation of what they do.
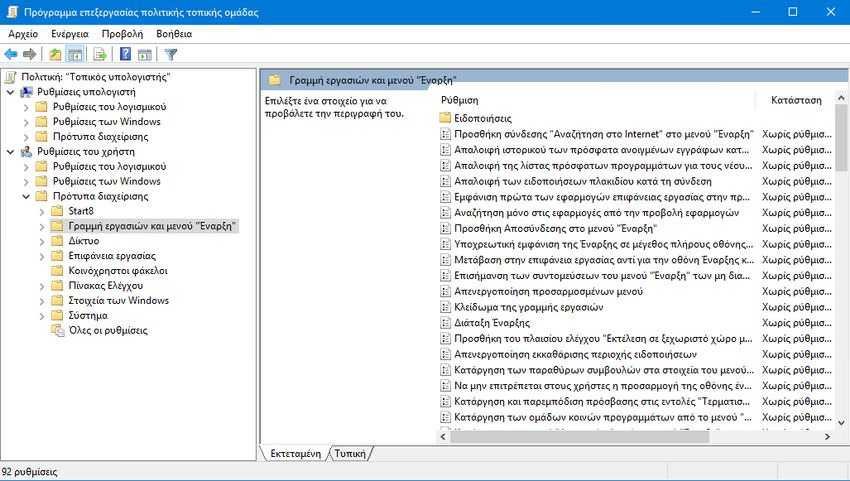
Τα tweaks που θα βρείτε είναι πολύ εύκολο να τα καταλάβετε, γι ‘αυτό δεν χρειάζεται να σας τα εξηγήσουμε κάθε ένα ξεχωριστά. Εκτός αυτού, τα Windows ήδη προσφέρουν μια λεπτομερή περιγραφή για κάθε ρύθμιση. Μερικά από τα πράγματα που μπορείτε να κάνετε είναι να αλλάξετε την λειτουργία του κουμπιού εκκίνησης, να αποτρέψετε τους χρήστες να τοποθετούν προγράμματα στη γραμμή εργασιών, να περιορίσετε την δυνατότητα αναζήτησης, να αποκρύψετε τις ειδοποιήσεις, να αποκρύψετε το icon της μπαταρίας, να αποφύγετε αλλαγές στη γραμμή εργασιών και στις ρυθμίσεις μενού, να αποτρέψετε τους χρήστες από τη χρήση οποιεσδήποτε επιλογής ηλεκτρικής τροφοδοσίας, να αφαιρέστε την επιλογή “Εκτέλεση” από το μενού έναρξης και ένα σωρό άλλα κόλπα.
Time to show who the boss is.
The above Group Policy settings should help you take control of a PC and ensure that nothing goes wrong, even if it is used by users other than you. Group Policy has hundreds of options to control various Windows features, just the above are just a few basic settings for an administrator. We hope you have a keen interest in spending the time to explore all the hidden diamonds inside it. But for good and for bad, and since group policy is labyrinth in setup and tricks, it would be a good idea to have created a system restore point before making any changes.





