CommandoVM is a fully customized Windows-based security distribution for penetration testing (penetration tests). It has a variety of hacking tools not included in Kali Linux that highlight the effectiveness of Windows as a platform for attacks.
System requirements
Minimum System Requirements
- Windows 10
- 60 GB Hard Drive
- 2 GB RAM
Proposed system requirements
- Windows 10 22H2
- 80+ GB Hard Drive
- 4+ GB of RAM
- 2 network adapter
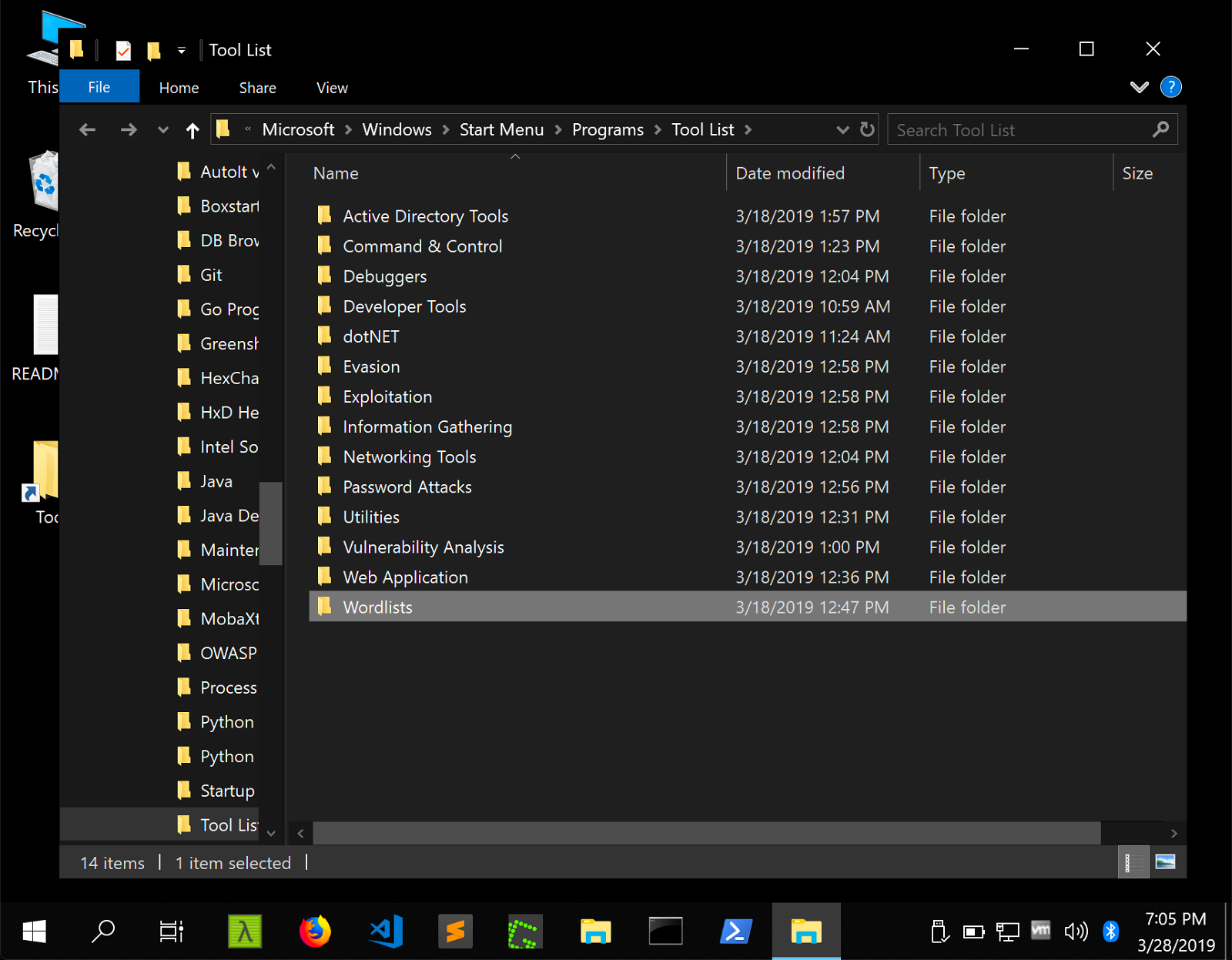
Pre-installed Programs
Active Directory Tools
- Remote Server Administration Tools (RSAT)
- SQL Server Command Line Utilities
- Sysinternals
Command & Control
- Covenant
- PoshC2
- WMImplant
- WMIOps
Developer Tools
- dep
- Go
- Go
- Java
- Python 2
- Python 3 (default)
- Ruby
- Ruby Devkit
- Visual Studio 2017 Build Tools (Windows 10)
- Visual Studio Code
Evasion
- CheckPlease
- Demiguise
- DefenderCheck
- DotNetToJScript
- Invoke-CradleCrafter
- Invoke-DOSfuscation
- Invoke-Obfuscation
- Invoke-Phant0m
- Not PowerShell (nps)
- PS>Attack
- PSAmsi
- Pafishmacro
- PowerLessShell
- PowerShdll
- StarFighters
Exploitation
- ADAPE-Script
- Monitor API
- CrackMapExec
- CrackMapExecWin
- STEAM
- EvilClippy
- Exchange-AD-Privesc
- FuzzySec's PowerShell-Suite
- FuzzySec's Sharp-Suite
- Generate-Macro
- GhostPack
- The red
- SafetyKatz
- seat belt
- SharpDPAPI
- SharpDump
- SharpRoast
- SharpUp
- SharpWMI
- GoFetch
- Packet
- Invoke-ACLPwn
- Invoke-DCOM
- Invoke-PSImage
- Invoke-PowerThIEf
- Kali Binaries for Windows
- luckystrike
- MetaTwin
- Metasploit
- Mr. Unikod3r's RedTeamPowershellScripts
- NetshHelperBeacon
- nishang
- Orca
- PSReflect
- PowerLurk
- PowerPriv
- PowerSploit
- PowerUpSQL
- PrivExchange
- Ruler
- SharpExchangePriv
- SharpExec
- SpoolSample
- UACME
- impacket-examples-windows
- vsown
Information Gathering
- ADACLScanner
- ADExplorer
- ADOffline
- ADRecon
- blood hound
- dnsrecon
- Get-ReconInfo
- GoWitness
- Nmap
- PowerView
- Dev branch included
- SharpHound
- SharpView
- SpoolerScanner
Networking Tools
- Citrix Receiver
- openvpn
- Proxycap
- PuTTY
- telnet
- VMware Horizon Client
- VMware vSphere Client
- VNC-Viewer
- WinSCP
- Windump
- Wireshark
Password Attack
- ASREPRoast
- CredNinja
- DSInternals
- Get-LAPSPasswords
- Hashcat
- Internal Monologue
- Inveigh
- Invoke-TheHash
- KeeFarce
- KeeThief
- LAPSToolkit
- MailSniper
- Mimikatz
- Mimikittenz
- RiskySPN
- SessionGopher
Reverse Engineering
- DNSpy
- Flare-Floss
- ILSpy
- PEview
- Windbg
- x64dbg
Utilities
- 7zip
- Adobe Reader
- AutoIT
- Command
- Cyber Chef
- Gimp
- Greenshot
- Hashcheck
- Hexchat
- HxD
- Keepass
- MobaXterm
- Mozilla Thunderbird
- Neo4j Community Edition
- Pidgin
- Process Hacker 2
- SQLite DB Browser
- Screentogif
- Shellcode Launcher
- Sublime Text 3
- TortoiseSVN
- VLC Media Player
- WinRAR
- yEd Graph Tool
Vulnerability Analysis
- AD Control Paths
- Egress-Assess
- Grouper2
- NtdsAudit
- zBang
web applications
- Burp Suite
- Fiddler
- Firefox
- OWASP Zap
- Subdomain-Brute force
Wordlists
- FuzzDB
- PayloadsAllTheThings
- SecLists
και άλλα πολλά...
Application snapshots

Video installation guide
User guide in video
You will find a guide to installing and using the program here.





