According to Open Web Application Security Project (OWASP), command injection is one of the most serious and numerous attacks for web applications.
In addition, these attacks usually result in serious financial loss to companies and other entities, as they are attacks against the database, which contains valuable information such as credit card numbers and personally identifiable information (PII).
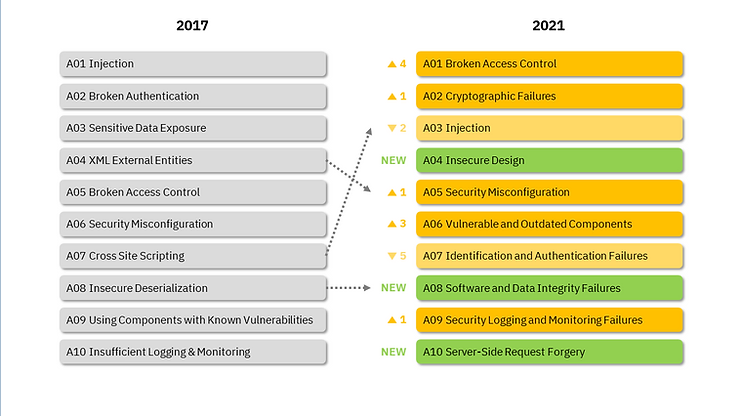
OWASP Top 10
Although there are numerous types of attack against databases, the most common is the SQL injection. It SQL injection sends SQL commands from the web form to the backend database.
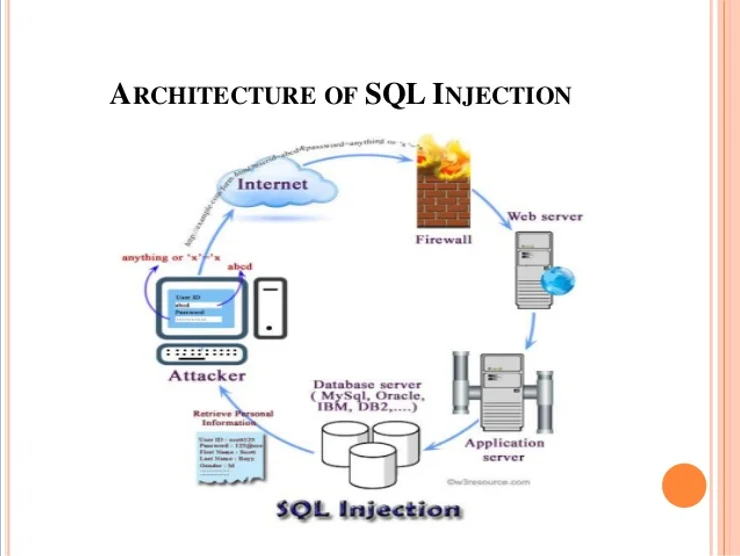
If these SQL statements are not cleaned up at the client (browser) level, they can be transferred to the database and cause chaos such as,
-
Exfiltrate data
-
Delete data
-
Add data
-
Update date
When testing for vulnerabilities SQL injection, these are some of the most common commands and special characters. The better you understand SQL, the more successful you will be with the attack SQL injection.
Notes
Single quote ('): Often used to end alphanumeric characters.
Double quote (“): Can also be used to terminate alphanumeric characters in some databases.
Comment sequences:
Double dash (–): This is an SQL comment and can be used to invalidate the rest of a query.
Hash (#): In MySQL, it is an alternative way to comment out the rest of the query.
Slash-star (/* … */): Multiline comment.
It can be used to comment out parts or the entire query.
Functions and commands
Period (?): Represents the end of one query and the beginning of another.
Logical operators: AND, OR.
Control functions: UNION, UNION ALL.
Boolean values
TRUE or 1=1: Always evaluates to true and can be used to handle WHERE clauses.
FALSE or 1=0: Always evaluates to false.
Time delay functions
SLEEP(x): In MySQL, causes a delay of x seconds.
WAITFOR DELAY 'hh:mm:ss': In SQL Server, causes a delay.
pg_sleep(x): In PostgreSQL, causes a delay of x seconds.
Retrieving information
@@version: (works on many databases).
CURRENT_USER: Retrieves the current user.
Hex encoding
Attackers may encode their payloads in hexadecimal to bypass the wrong filters.
wild cards
Percentage sign (%): Represents zero or more characters in SQL LIKE clauses. This was used in the recent MoveIT attack by C|op.
Special functions
CONCAT(): Used to concatenate strings in SQL.
CAST(), CONVERT(): Used for type conversion.
ASCII(), CHAR(): Functions to get ASCII values or characters, can be used in blind SQLi.
Sub-options and metadata queries
SELECT … FROM information_schema.tables: Used in databases such as MySQL and PostgreSQL to collect metadata about tables.
SELECT … FROM sysobjects …: Used in SQL Server to collect metadata.
Summary
The Injection attacks on web forms leading to a database leak is one of the most serious attacks that compromise page security.
These database attacks are used in the form of SQLi attacks, where SQL commands are sent to the backend database from unscanned input from the client (browser).
Although SQLi attacks are becoming more and more difficult, a thorough and deep understanding of SQL is necessary to carry out such an attack.



