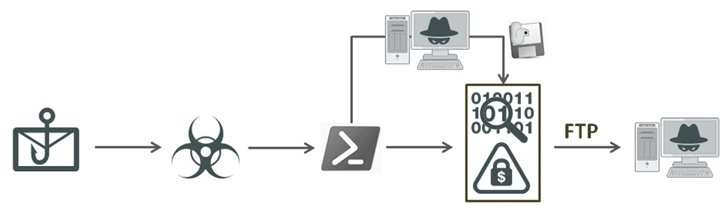
A new data-stealing malware called EvilExtractor is available for sale and targets files from Windows systems.

"It includes several modules that all work through an FTP service," said Cara Lin, a researcher at Fortinet FortiGuard Labs. “It also contains environment control and Anti-VM features. Its main purpose appears to be to steal browser data and information from exposed endpoints and then upload it to the attacker's FTP server.”
Η company network security said it observed a wave of attacks spreading the malware in March 2023, with the majority of victims located in Europe and the US. While EvilExtractor is marketed as an educational tool, it has been adopted by hackers as an information stealer.
The attack tool is sold by a hacker named Kodex on cybercrime forums like Cracked dating back to October 22, 2022. It is constantly updated and incorporates various modules to extract system metadata, passwords and cookies from various web browsers, as well as to record keystrokes and even act as ransomware by encrypting files on the target system.
The malware is also said to have been used as part of a phishing email campaign detected by the company on March 30, 2023. The emails trick recipients into launching an executable file disguised as a PDF document under the guise of confirming its “details their account".
The “Account_Info.exe” binary is a cloaked Python program designed to launch a .NET loader that uses a Base64-encoded PowerShell script to launch EvilExtractor. The malware, except for the collection files, can also activate the camera and capture screenshots.
"EvilExtractor is used as a comprehensive information thief with multiple malicious features, including ransomware," said Lin. “The PowerShell script can escape detection in a .NET or PyArmor loader. Within a very short period of time, its developer has updated several functions and increased its stability."
The findings come as Secureworks' Counter Threat Unit (CTU) details a malicious SEO campaign used to deliver the Bumblebee malware loader via rogue installers of legitimate software.
Bumbleebee, first recorded a year ago by Threat Analysis Group της Google και την Proofpoint, είναι ένας αρθρωτός φορτωτής που διαδίδεται κυρίως μέσω τεχνικών phishing. Υπάρχει η υποψία ότι αναπτύχθηκε από παράγοντες που σχετίζονται με την business Conti ransomware as BazarLoader replacement.
The use of malicious ads to redirect users looking for popular tools such as ChatGPT, Cisco AnyConnect, Citrix Workspace and Zoom to fake websites that host infected installation files has been on the rise in recent months, after Microsoft began blocking macros by default from Office files downloaded from the web.
In an incident described by the company cyber securitys, the attacker used Bumblebee malware to gain an entry point and moved laterally after three hours to attack with Cobalt Strike and legitimate remote access software such as AnyDesk and Dameware. The attack was eventually stopped before it progressed to the final ransomware stage.





