The Hafnium hacking team managed to breach hundreds of thousands of facilities Exchange worldwide. An update is currently available to close the security holes, but it may be too late.
However, Microsoft has also provided some tools to check Exchange installations for signs of breach.
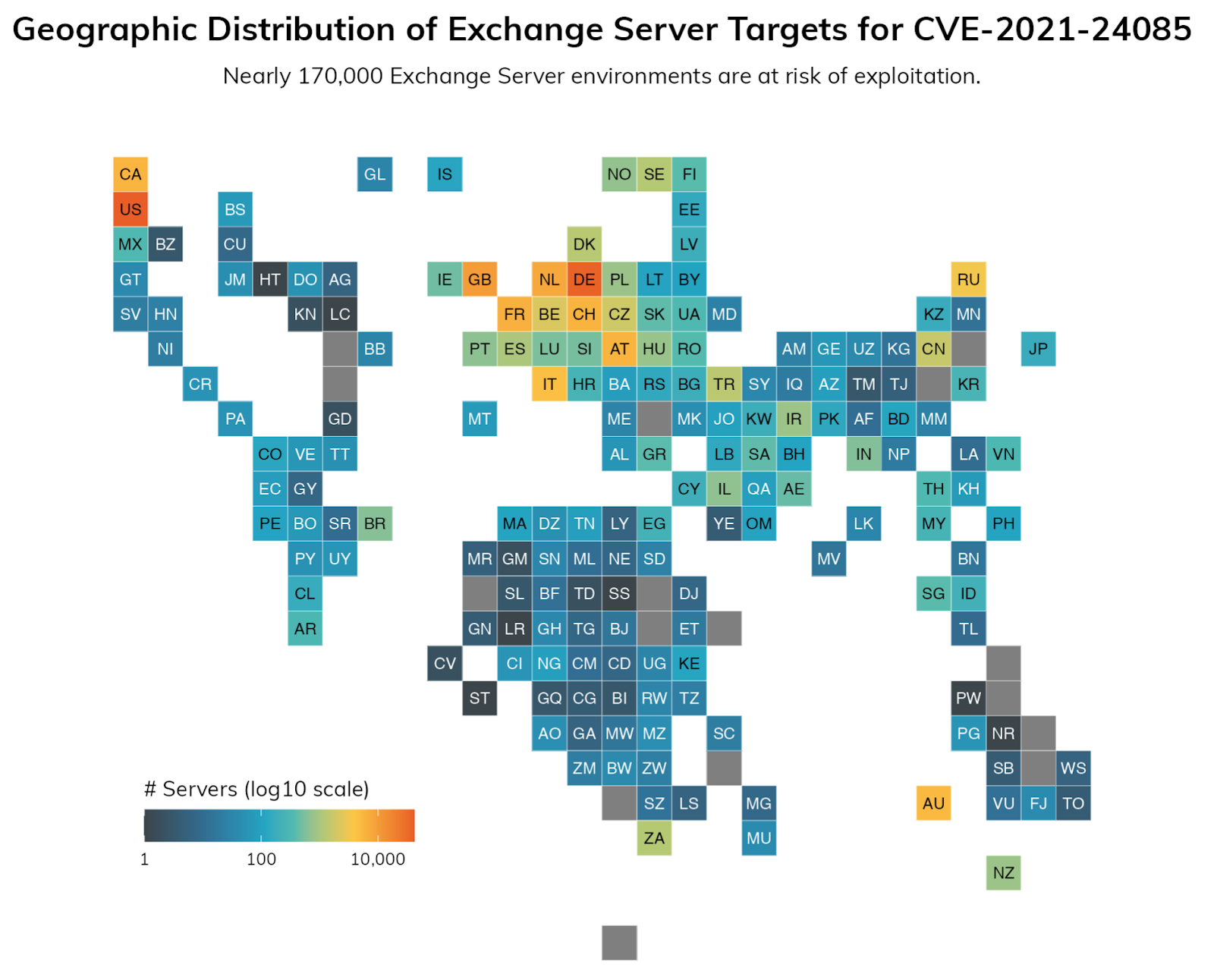
It seems that after SolarWinds was attacked by Russians, the next big disaster has been revealed. The hackers of the Chinese Hafnium team, exploited vulnerabilities in Exchange servers. The vulnerabilities were not closed with security updates until March 2, 2021.
The attackers 'goal was to gain control of the victims' emails and possibly access and infiltrate their network infrastructure through Active Directory licenses.
In one Publication security company Rapid7 reports that there are at least 170.000 compromised Exchange servers. The article provides IP addresses that scan the Internet as well as an analysis of how one can detect an infection. More information and analysis are provided at this Microsoft article, as well as in this US-CERT warning.
Microsoft has released a PowerShell script (Test-Hafnium), με το όνομα Test-ProxyLogon.ps1, για να σας βοηθήσει να εντοπίσετε τα vulnerable points. The script and additional notes are on GitHub.
CERT Latvia also published one script on GitHub which can be used to check if an Exchange server contains a webshell.





