Its security researchers Google expand the scope of their work since they will investigate errors in the software available at OEM Appliances Android όπως από τις εταιρείες Huawei, ZTE και Samsung.
The new program is called Android Partner Vulnerability Initiative (APVI by Android Partner Vulnerability Initiative). Through the new program, Google's Android security and privacy team will be able to investigate and reveal defects in OEM software.
"APVI covers issues discovered by Google that could potentially affect the security of an Android device or its user. The new service is in line with the standard ISO / IEC 29147: 2018 Information technology - Security techniques - Vulnerability disclosure recommendations", Says Google.
The team has already revealed and reported a number of vulnerabilities in OEMs, some of which have not been fixed. 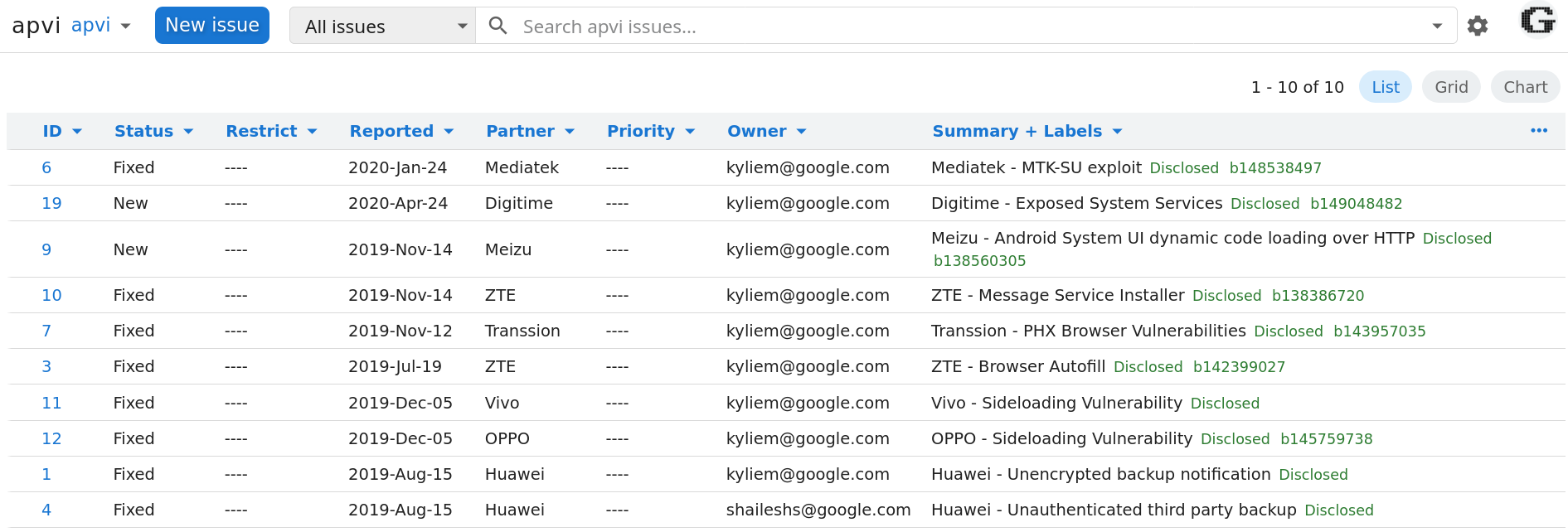
The program works like the Android Security Gap Rewards Program (ASR from the Android Security Rewards Program) and the Google Play Security Rewards Program, which contributes to the Android Security Bulletins (ASB), which ultimately leads to the monthly update level Security Code (SPL) for Android.
You can track the latest known vulnerabilities in the debugger through it Chromium bug tracker.





