After a year, Gootkit is back to life along with REvil Ransomware, in a new campaign targeting Germany.

Gootkit Trojan is Javascript-based malware that performs various activities such as remote access, key logging, video recording, email theft, password theft, and malicious script injection to steal online banking credentials.
Last year, the creators of Gootkit leaked data when they left a MongoDB database exposed on the Internet. Following this incident, security investigators believed that the creators of Gootkit had ceased operations until they suddenly appeared in November.
Gootkit comes to life with ransomware collaboration
In this new malicious campaign, hackers hack into WordPress sites and use infected SEO to display fake forum posts. These posts pretend to be a question, with a link to fake forms or downloads.
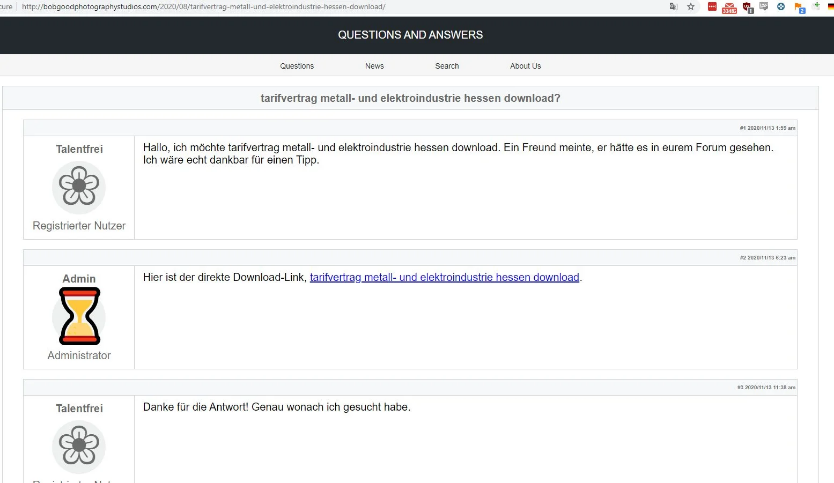
When the user clicks on the link, they will download a ZIP file containing an obscure JS file that will install either the Gootkit malware or the REvil ransomware.
This same distribution method was previously used by REvil in September 2019, around the same time that Gootkit disappeared.
Gootkit and REvil were installed in anonymous attacks
In a news report released yesterday, Malwarebytes researchers explain that malicious JavaScript payloads will launch attacks on either Gootkit or REvil.
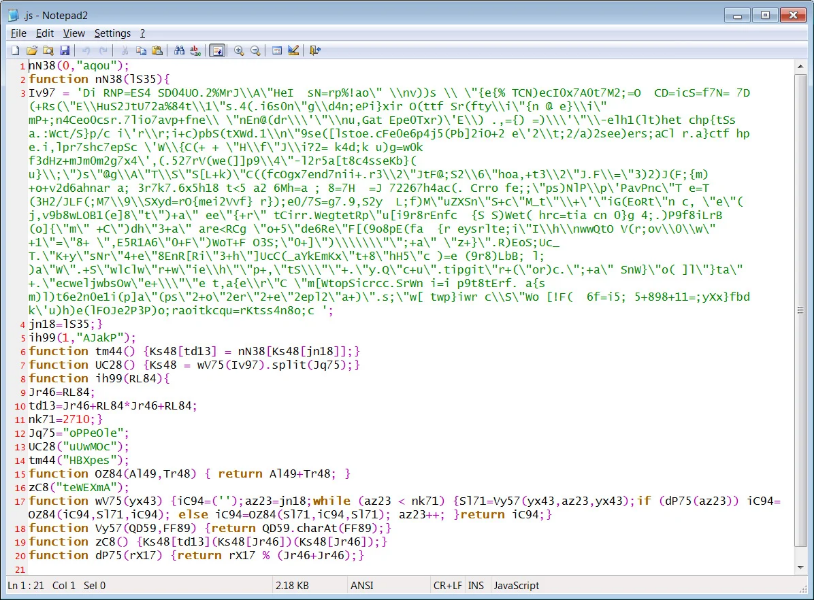
When started, JavaScript will connect to the command and control server and download another script that contains the malware.
In Malwarebytes' analysis, this payload is usually Gootkit, although in some cases it was REvil ransomware.
After converting to ASCII, the next JavaScript is revealed and the code is executed. This JavaScript comes with a built-in PE payload that can be either a loader for Gootkit or for ransomware REvil.
These payloads will be stored as Base64 encoded or hexadecimal strings in either a text file or split into multiple Windows registry values, as shown below.
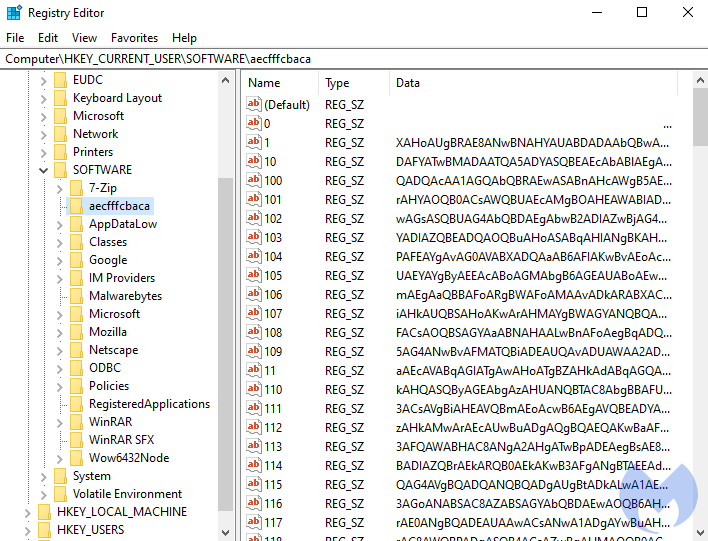
The loader will finally read the Registry or text file payloads, decode it, and start the process directly on μνήμη.
Using fuzzy payloads and split into comeyea that are stored in the Registry, making it harder for security software to detect malicious payloads.
"The hackers behind this campaign are using a very clever loader that performs certain steps to avoid detection. "Because the payload is stored in the registry with a random key name, many security products will not be able to detect it and remove it," explains Malwarebytes.
An interesting discovery that the analyst found during essay of this malicious campaign was that the Revil infection showed ransom notes used in previous attacks.
#GootKit > #REvil/#Sodinokibi. The anyrun got someone else's key? 😂
cc @malwrhunterteam @demonslay335
h / t @Scoobs_McGee again https://t.co/X9hPHs8BBW pic.twitter.com/SWODYmxbjY— Tommy M (TheAnalyst) (@ffforward) November 24, 2020
This error was most likely caused by the distribution campaign, which uses an older version of REvil ransomware and forgot to update it to a newer version.





