The GoScan is an interactive, auto-complete network scanner that provides automation via nmap.

GoScan is also particularly suitable for unstable environments, as it enables scans and maintains their status in a SQLite database.
Scans are performed in the background, so even if the connection to the framework running GoScan is lost, the results can be uploaded asynchronously. That is, data can be entered into GoScan at different stages of the process, without the need to re-entermovementof the entire process from scratch if something goes wrong.
In addition, the Service Enumeration integrates a collection of other tools (eg EyeWitness, Hydra, nikto, etc.), each custom targeting a specific service.
Installation
# Linux (64bit)
$ wget https://github.com/marco-lancini/goscan/releases/download/v2.4/goscan_2.4_linux_amd64.zip
$ unzip goscan_2.4_linux_amd64.zip
# Linux (32bit)
$ wget https://github.com/marco-lancini/goscan/releases/download/v2.4/goscan_2.4_linux_386.zip
$ unzip goscan_2.4_linux_386.zip
# After that, place the executable in your PATH
$ chmod + x goscan
$ sudo mv ./goscan / usr / local / bin / goscan
Application snapshots
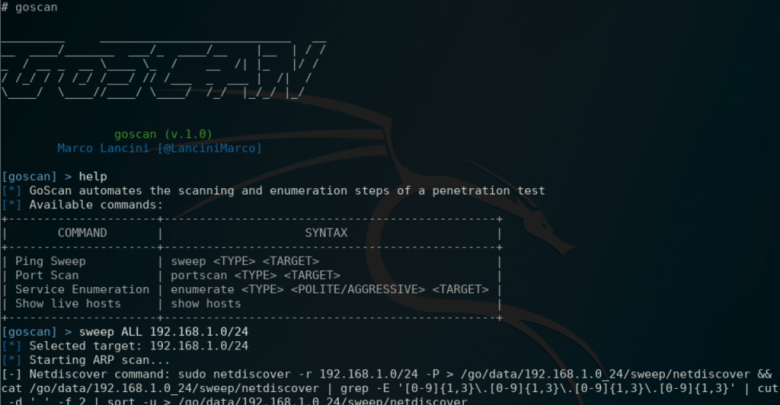
Use
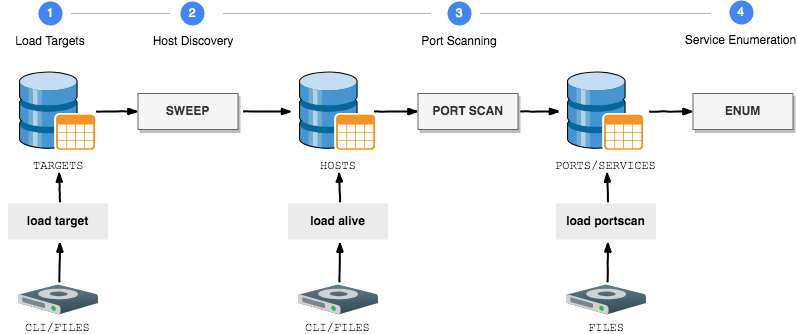
| 1. Loading targets |
|
| 2. Host discovery |
|
| 3. Door scan |
|
| 4. Counting services |
|
| 5. Special scans |
|
| Tools |
|





