Grizzly Steppe: As "evidence" and to document the unprecedented deportation of 35 Russian diplomats and the closure of two Russian associations without a major simultaneous political or diplomatic incident or act of war, the Department of Homeland Security (DHS) and the FBI 13-page "report" that justifies the above acts "for the violation and exploitation of networks and parameters related to the US elections", that is, the hack.
According to DHS, “this document provides technical details about the tools and infrastructure used by Russian civilian and military intelligence services. intelligence Services or RIS) to hack and exploit networks and parameters related to US elections, as well as US government politicians, and private sector sectors. The US government refers to this malicious cyber activity by RIS as GRIZZLY STEPPE.”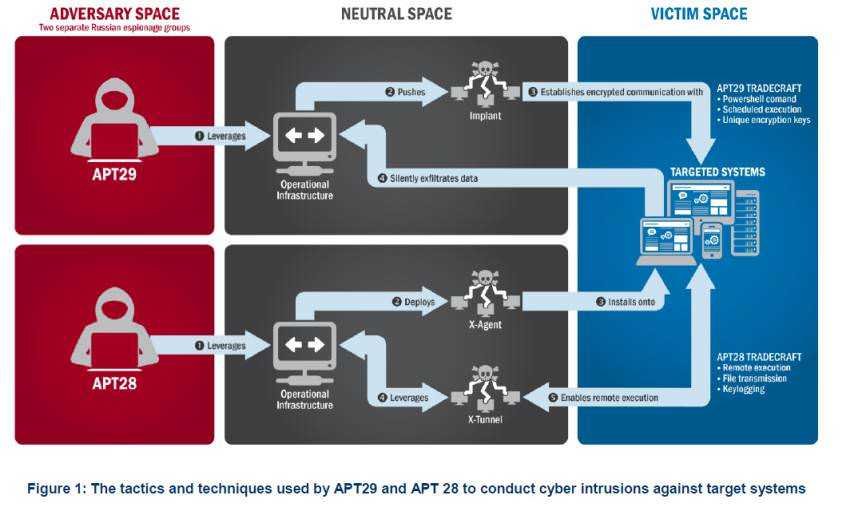
From the very beginning of the report, there is a broad disclaimer, according to which everything contained in it (the report) may be totally incorrect.
“This report is provided for informational purposes only. The Department of Homeland Security (DHS) makes no warranties of any kind information contained within. DHS does not endorse any commercial product or service referred to herein.”
The continuation raises questions as there is a claim that Russia has violated the elections, and the 13 page report allegedly provides technical details about the tools and infrastructures used by the Russian intelligence services.
Grizzly Steppe:
So, with this helpful background in mind, we present some of the most notable excerpts from the report that refers to two supposed Russian groups - APT and APT 28.
The US Government confirms that two different RIS actors participated in the US invasion. The first group, also known as Advanced Persistent Threat (APT) 29, attacked party systems in the summer of 2015, while the second, also known as APT28, was launched in the spring of 2016.
Both groups have previously carried out targeted attacks on government organizations, think tanks, universities and companies around the world. APT29 has been observed conducting targeted spearphishing campaigns using web links that point to malware Remote Access Tools (RATs).
APT28 is known for using domains that closely mimic those of target organisms and are aimed at cheating potential victims by undermining legitimate certifications.
Once the two groups APT28 and APT29 manage to gain access to the data of their victims, collect and analyze the information to gain value for the intelligence services. These groups use this information to create highly targeted spearphishing campaigns.
All the report published today is at the end of the publication, and comes as a retaliation against Russia for Grizzly Steppe by the Obama administration.
It should be noted that the intelligence community formally attributed the attacks to Russia in October, but did not provide any evidence to support its assessment. It is unclear whether this DHS report seeks to pass as "proof" that Russia violated the US election, because if they do, Putin will laugh all night.





