Kaspersky Lab recently discovered it Grabit, a new digital espionage campaign that has managed to capture about 10.000 records from small and medium-sized businesses, mainly in Thailand, India and the United States. Companies targeted by Google Grabit were active in various sectors, such as: chemical products, nanotechnology, education, agricultural production, SMEs, constructions, etc.
The campaign also took place in the United Arab Emirates, Germany, Israel, Canada, France, Austria, Sri Lanka, Chile and Belgium.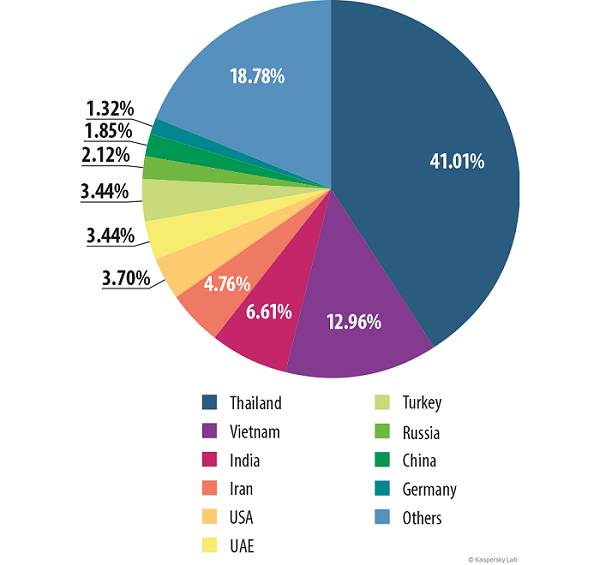
“We see many espionage campaigns targeting large corporations, government and other major organizations. Small and medium-sized enterprises are rarely among the targets of these attacks. However, Grabit proves that in the digital world, any organization, regardless of whether it has capital, important information or political influence, can potentially attract the attention of a malicious actor.
The Grabit campaign is still active, so it is extremely important that businesses monitor their networks to remain secure. On May 15th, a simple Grabit keylogger was found to be in possession of thousands of data connectionof victim accounts from hundreds of "infected" systems. This threat should not be underestimated." he said Gone Noar, Senior Security Researcher of the Worldwide Research and Analysis Group of Kaspersky Lab.
The "infection" starts when a user in a business receives an email with an attachment that resembles a Word (.doc) file. When the user downloaded the document, the spy program enters the computer from a remote server that has been tampered with by the Grabit group to be used as a malware node.
Attackers control their victims using the HawkEye keylogger (a commercial spy tool from HawkEyeProducts) and a configuration unit that contains a range of Remote Management Tools.
According to Kaspersky Lab specialists, the size of the campaign is that a keylogger on one of the command-and-control servers has managed to bypass 2.887 access codes, 1.053 messages and 3.023 user names from 4.928 different hosts, both internally and externally, between including Outlook, Facebook, Skype, GMail, Pinterest, Yahoo, LinkedIn and Twitter. He also managed to intercept bank account information and other information.
A heterogeneous group of digital criminals
The team behind Grabit doesn't go to any extra effort to hide their activity like they do in other cases. Some malicious samples used the same host server and even the same login details, compromising their own activity and better safety.
But on the other hand, attackers use powerful mitigation techniques to keep their code hidden from the analysts.
This leads Kaspersky Lab to believe that behind the Grabit's activities there is a heterogeneous group, with some of its members having more technical knowledge than others and more focused on making it difficult to locate them.
Expert analysis shows that whoever programmed the malware did not write the entire code from scratch.
To protect against Grabit, Kaspersky Lab suggests to businesses:
- Check the locations C:\Users\
\AppData\Roaming\Microsoft to see if they contain executable files, as they may have been infiltrated by malware. This is something basic that should not be ignored. - Check Windows System Parameters Settings via the "msconfig" procedure to ensure that there is no grabit1.exe in the startup table.
- Ensure that attachments and links from unknown senders are not opened. If a user can not open a file, they should not forward it to others, but ask for help from the IT department.
- Use an advanced and up-to-date anti-malware solution, and always follow the antivirus job list for suspicious procedures.
Kaspersky Lab products detect all known Grabit samples and protect users from this threat.
More information about Grabit is available on the site Securelist.com.





