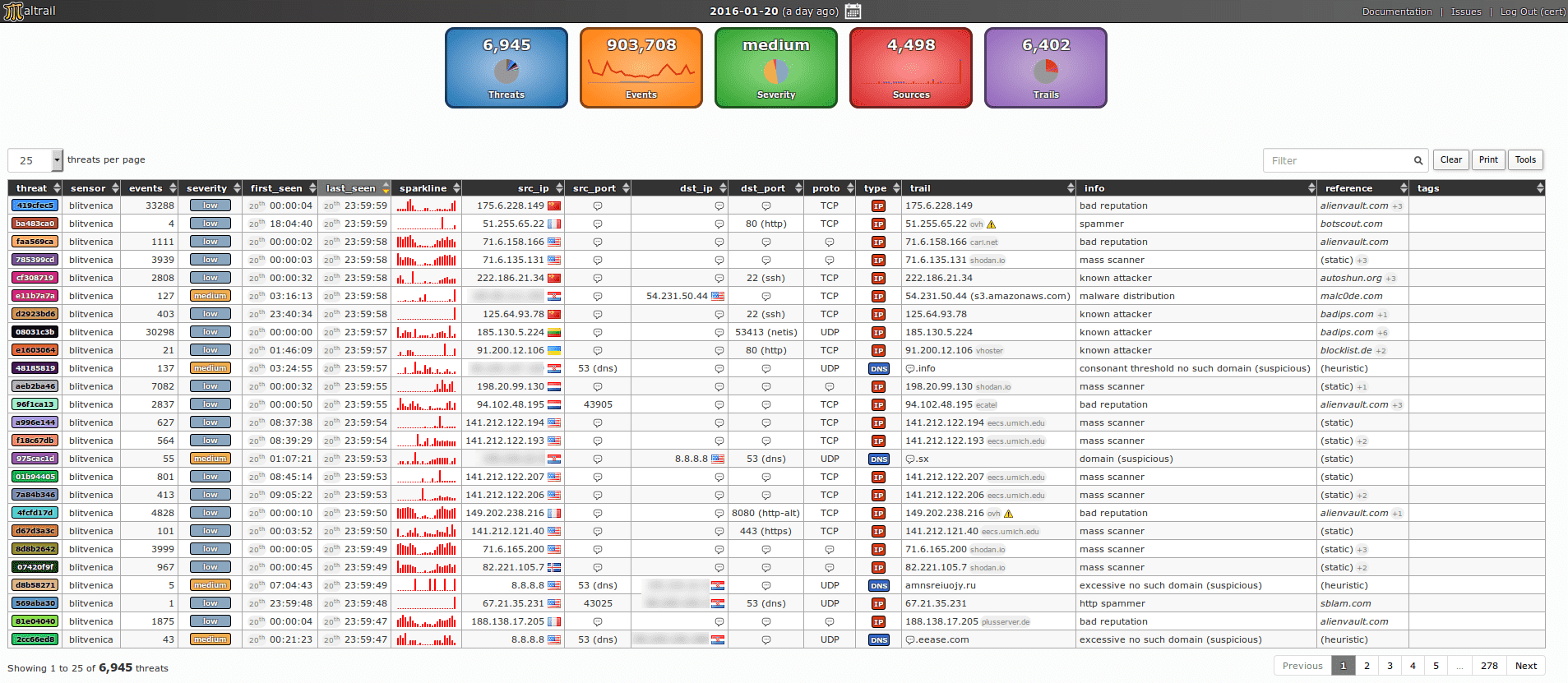
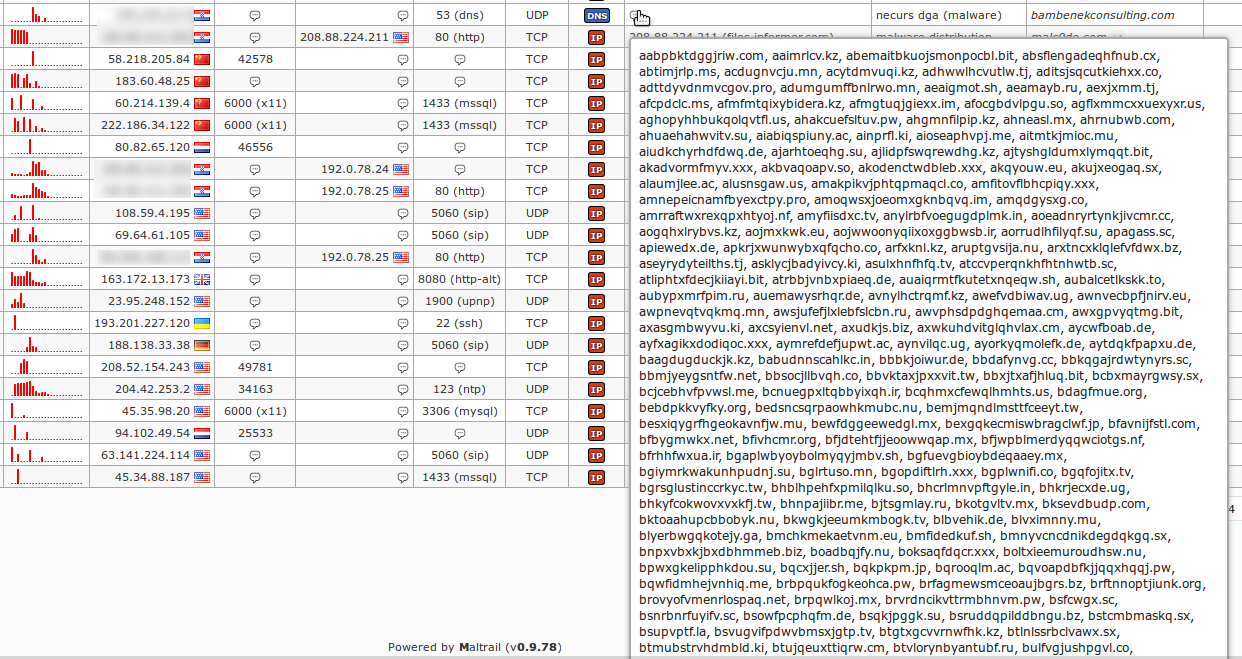
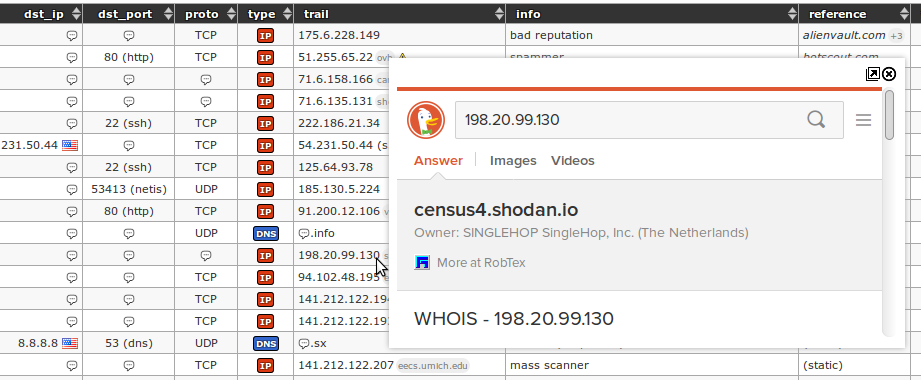
The Maltrail is a system detectionof malicious traffic, which uses publicly available lists containing malicious or generally suspicious "paths", along with static traces collected from various AV reports and custom user-defined lists, where the trace can be anything from name, URL , IP address or user and HTTP header value.
It also uses advanced heuristic mechanisms that can help detect unknown threats.
Architecture
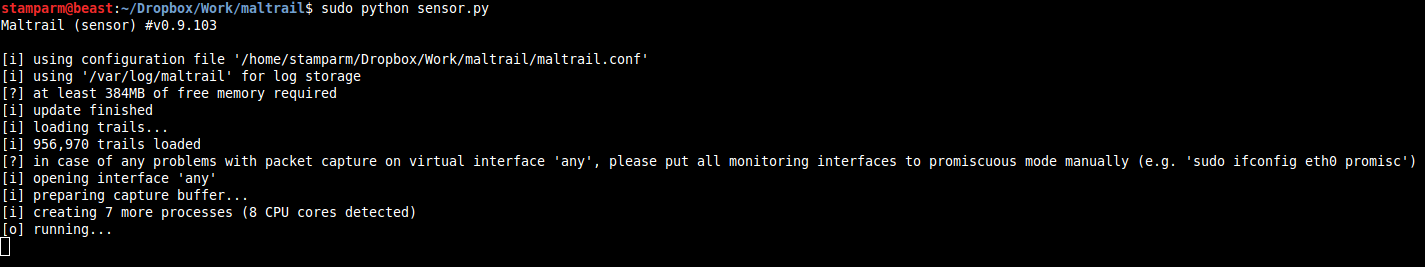
Maltrail is based on the sequence Sensor -> Server Client Architecture. Sensor(s) is a stand-alone component running on the monitoring node (e.g. Linux platform passively connected to the SPAN / mirroring port or transparently embedded in a Linux bridge) or stand-alone machine (e.g. Honeypot) where it 'monitors » the traffic passing for blacklist objects / "paths" (eg domain names, URLs and/or IP addresses).
In case of a positive match, it sends the details of the event to the (central) server where they are stored in the appropriate log directory (ie LOG_DIR described in the Configuration section).
If the sensor is running on the same computer as the server (default configuration), the logs are stored directly in the local log directory. Otherwise, they are sent via UDP messages to the remote server (ie LOG_SERVER described in the Configuration section).
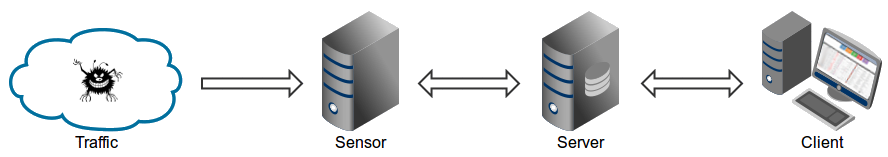
The primary role of the server is to store event details and provide support for application web report. In the default configuration, the server and sensor will operate on the same computer.
Thus, to avoid possible interruptions in the sensor activities, the front-end reference part is based on the “Fat client” architecture (i.e. all data post-processing is done inside the program instance browsing customer web).
The events (ie log entries) for the selected period (24 hours) are transferred to the client, where the web reporting application is solely responsible for the presentation part. The data is sent to the client in compressed parts, where it is processed sequentially. The final report is created in a condensed form, effectively allowing the presentation of the almost unlimited number of events.
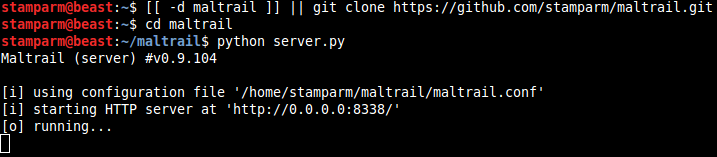
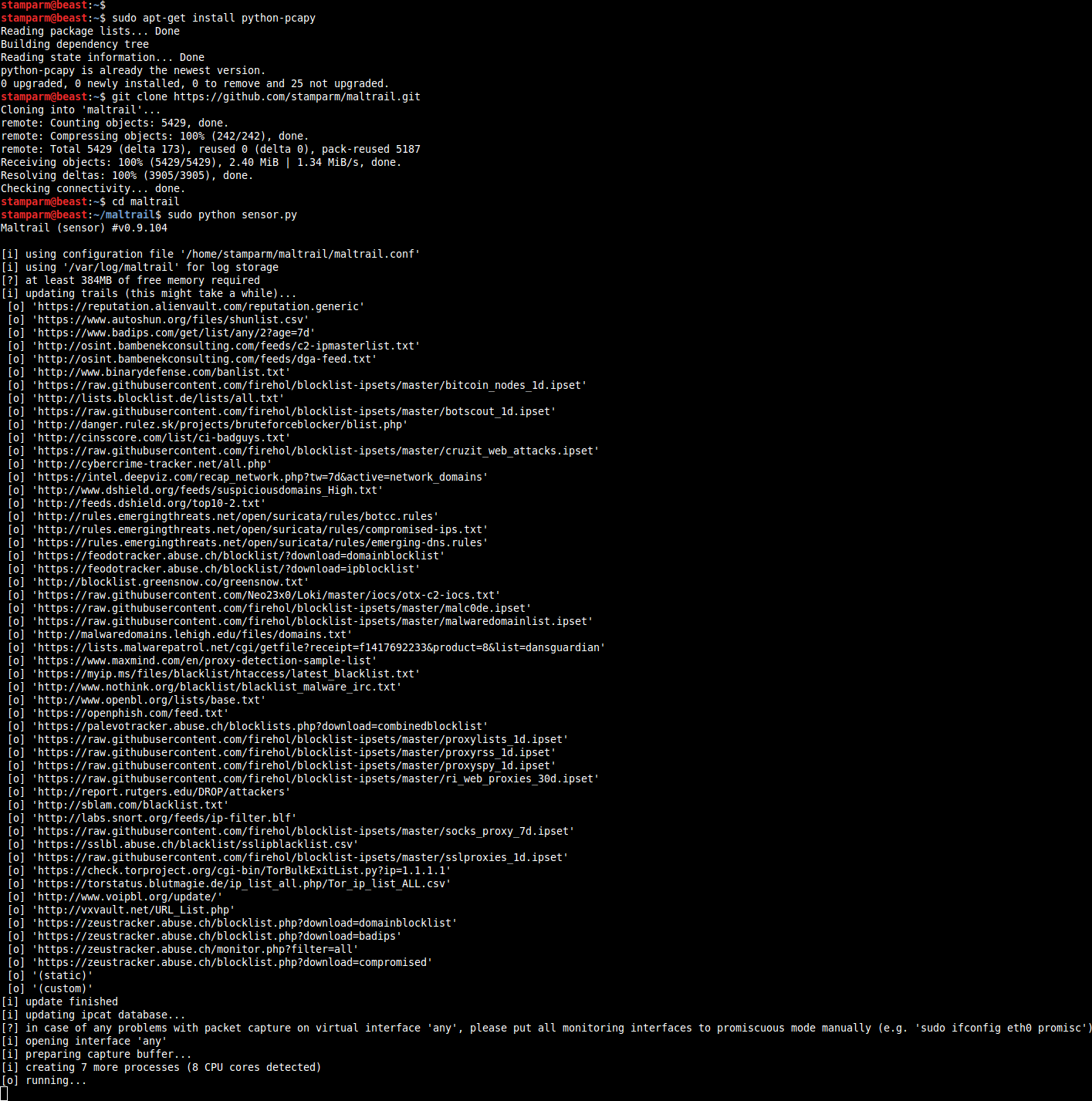
Installation
sudo apt-get install python python-pcapy git
git clone https://github.com/stamparm/maltrail.git
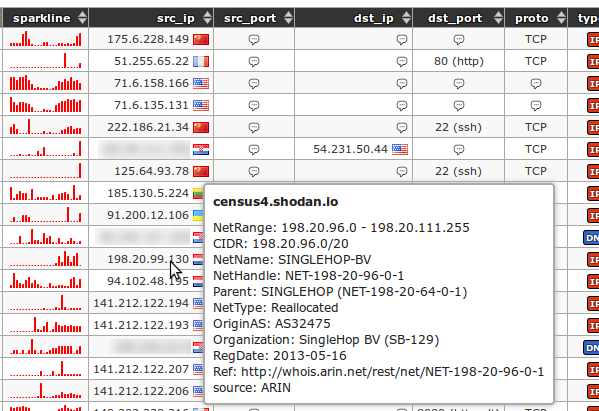
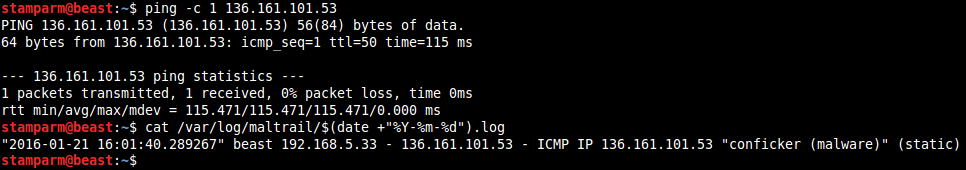
Application snapshots
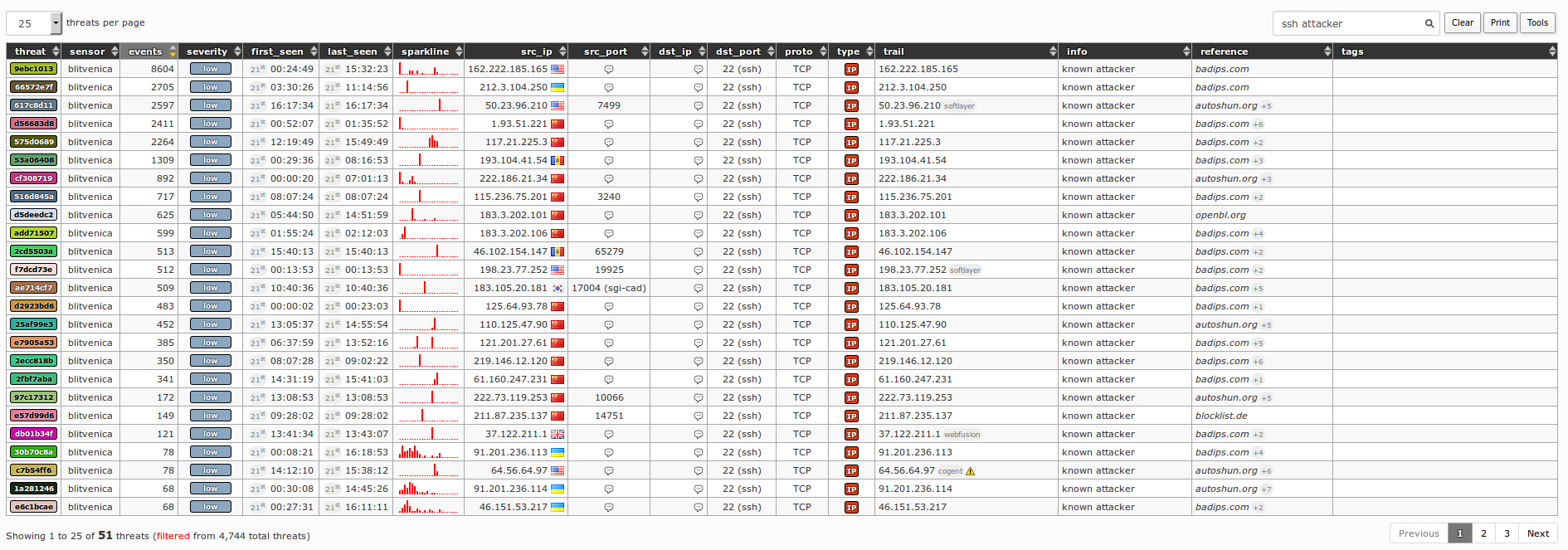

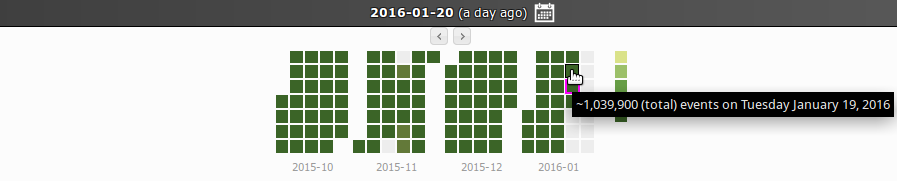
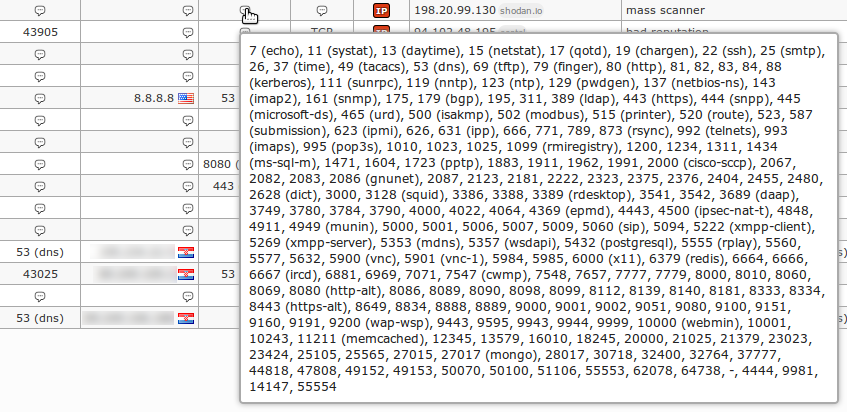
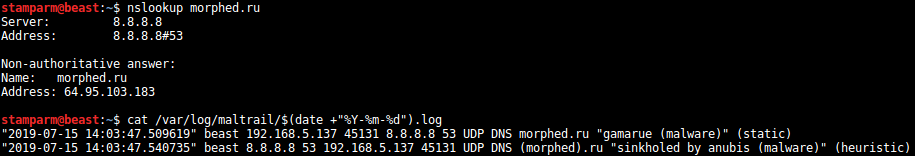
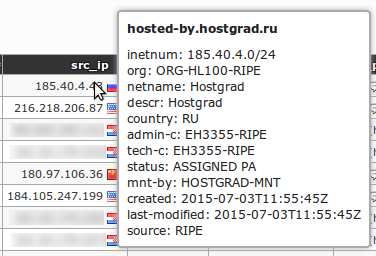

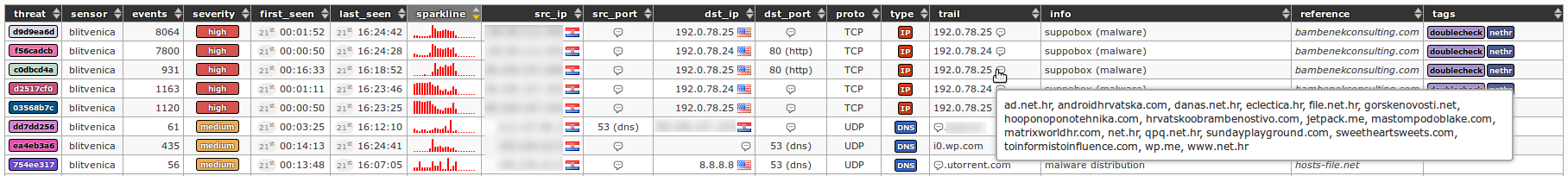
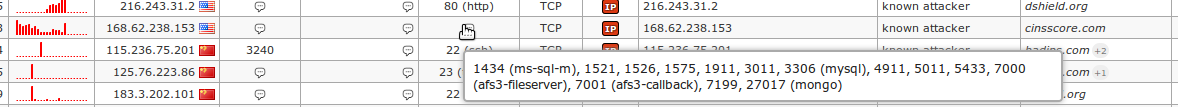
![]()
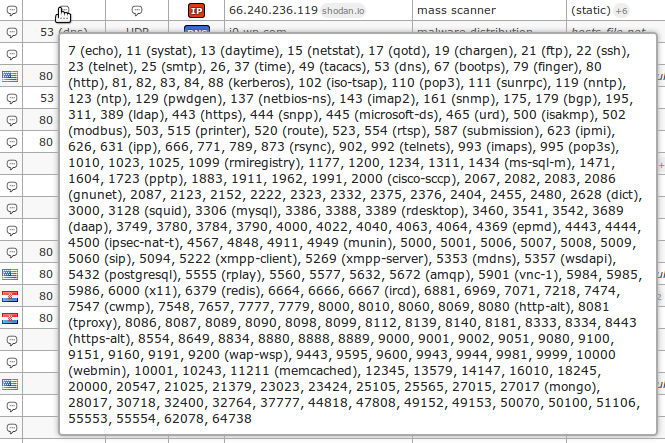
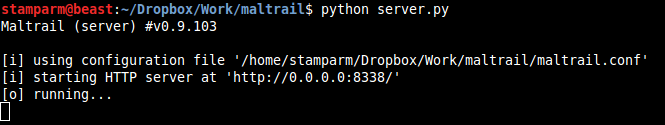
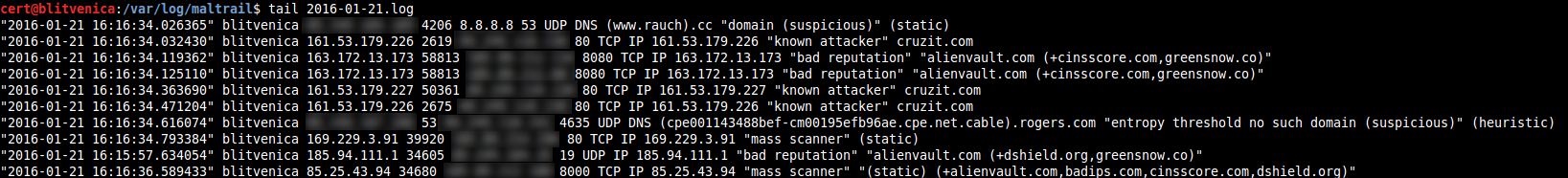
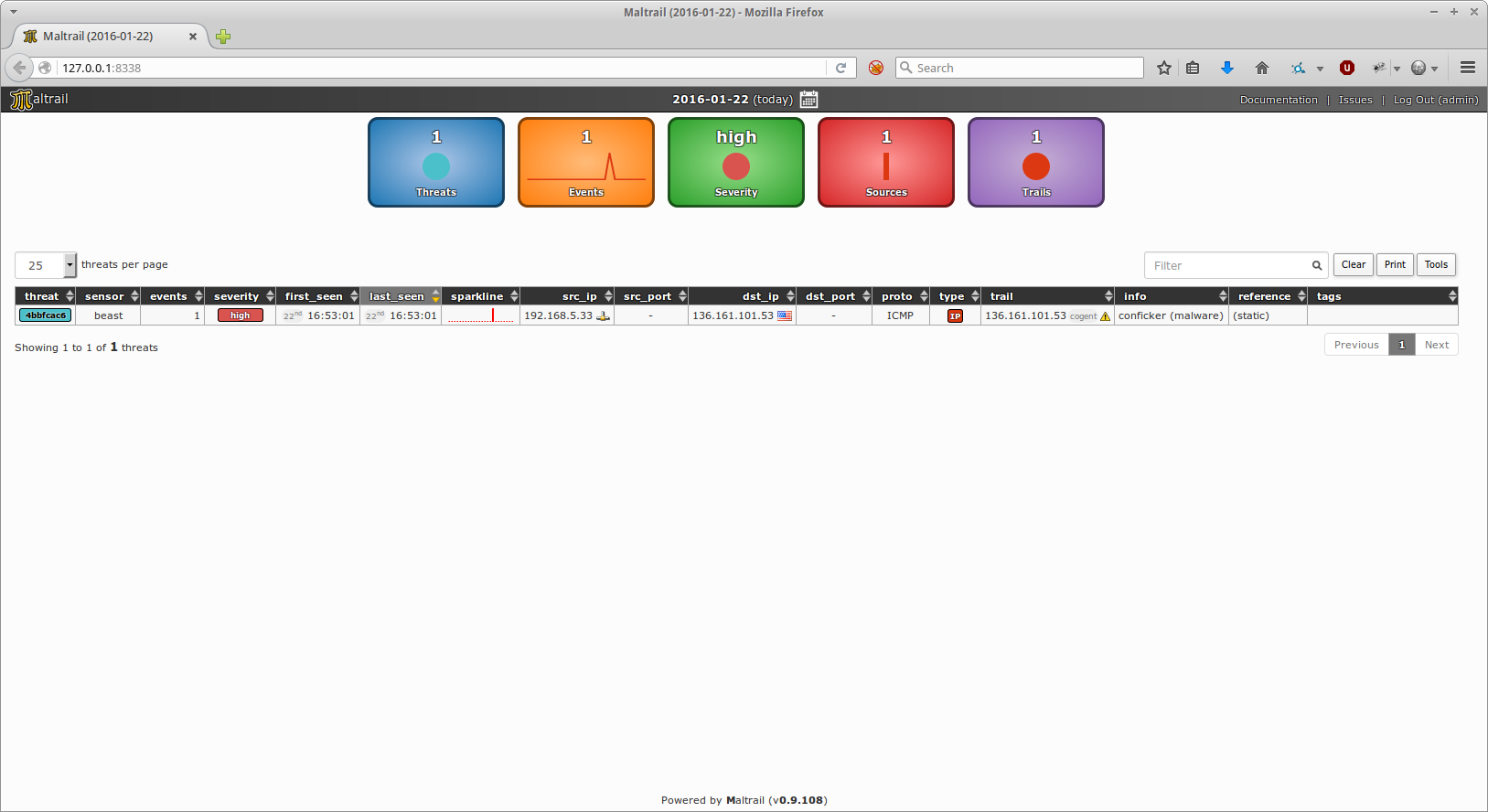
Information on using the program, you will find here.





