Modlishka: A new penetration testing tool can automate phishing attacks. The new tool may also violate accounts protected by two-factor authentication (2FA).
It is called Modlishka and was developed by Polish researcher Piotr Duszyński.
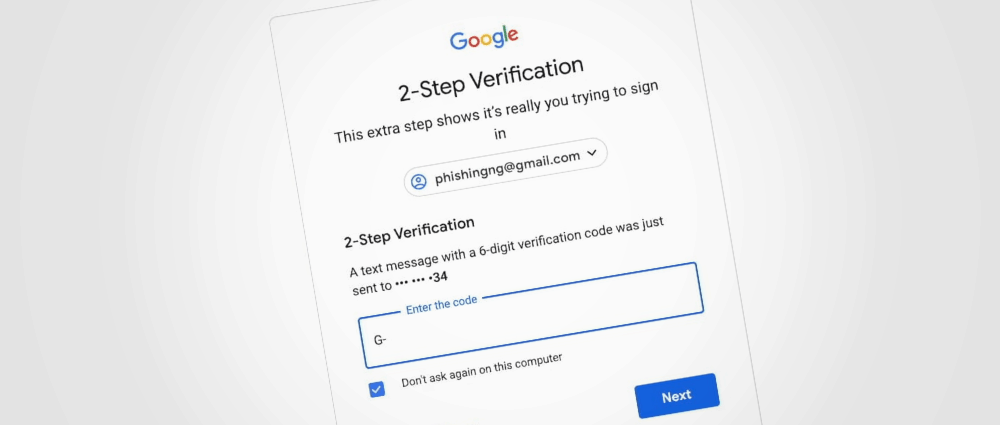
Modlishka is the tool that researchers call a reverse proxy server, but has been modified to handle page traffic (login) and phishing procedures.
It "parks" between the legitimate user and the page the hacker is interested in hacking (Gmail, Yahoo or Protonmail). Phishing victims connect to Modlishka's server and the reverse proxy running behind sends the requests to the original site.
So the victim gets authentic content from the normal website, but all the traffic and all the victim interactions pass and are registered on the Modlishka server.
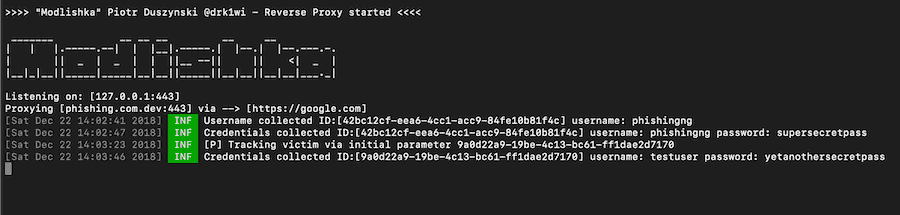
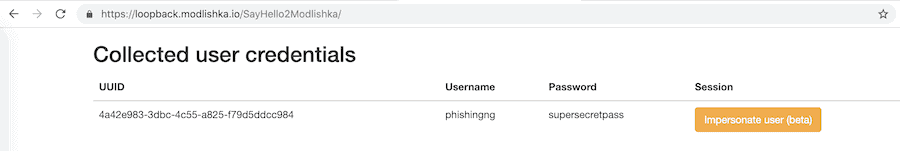
Of course all the passwords entered by the user are automatically recorded in the Modlishka panel, while the reverse proxy urges users to use 2FA tokens.
If attackers are on hand and collect these 2FA tokens in real time, they can use them to log in to victims' accounts and proceed with an immediate password change.
The video below shows how a phishing website using Modlishka perfectly loads the content from its real login page Google.
Due to its simple design, Modlishka does not use "standards", a term used by phishers to describe clones of legitimate sites. But all content is retrieved from the legal site in real time, so attackers do not have to spend a lot of time updating the templates.
Attackers still need a phishing domain (to host Modlishka's server) and a valid certificate TLS.
Modlishka is currently available at GitHub with open source license. More information is available at blog of Duszyński.
Images – Information Catalin Cimpanu ZDNet
_____________________






Even if you have a valid tls certificate you can not know the private key of the domain you are attacking so if the server has ssl (tls) you will not be able to see what data is exchanged client - server because it is encrypted…