For decades, security researchers have warned about techniques piracyof virtualization software. Apparently a team has put it into practice.
The software virtualization offers a way to multiply computing efficiency by hosting entire collections of computers as "virtual machines" on a single computer. 
Security researchers have long warned about the potential dark side of this technology: theoretical "hyperjacking" and "blue pill" attacks, where hackers steal the Virtualisation to spy on and manipulate virtual machines, with no way to detect the intrusion. This insidious spying eventually went from the research papers that brought the warnings to a mysterious hacker group that has carried out a bunch of hyperjacking attacks.
Today, the company security Mandiant owned by Google and virtualization company VMware have published shared warnings that a sophisticated hacker group is installing backdoors in VMware's virtualization software. By planting their own code on the victims' so-called hypervisors—the VMware software that runs on a physical computer to manage all the virtual machines it hosts—the hackers were able to monitor and invisibly run commands on the computers overseen by those hypervisors.
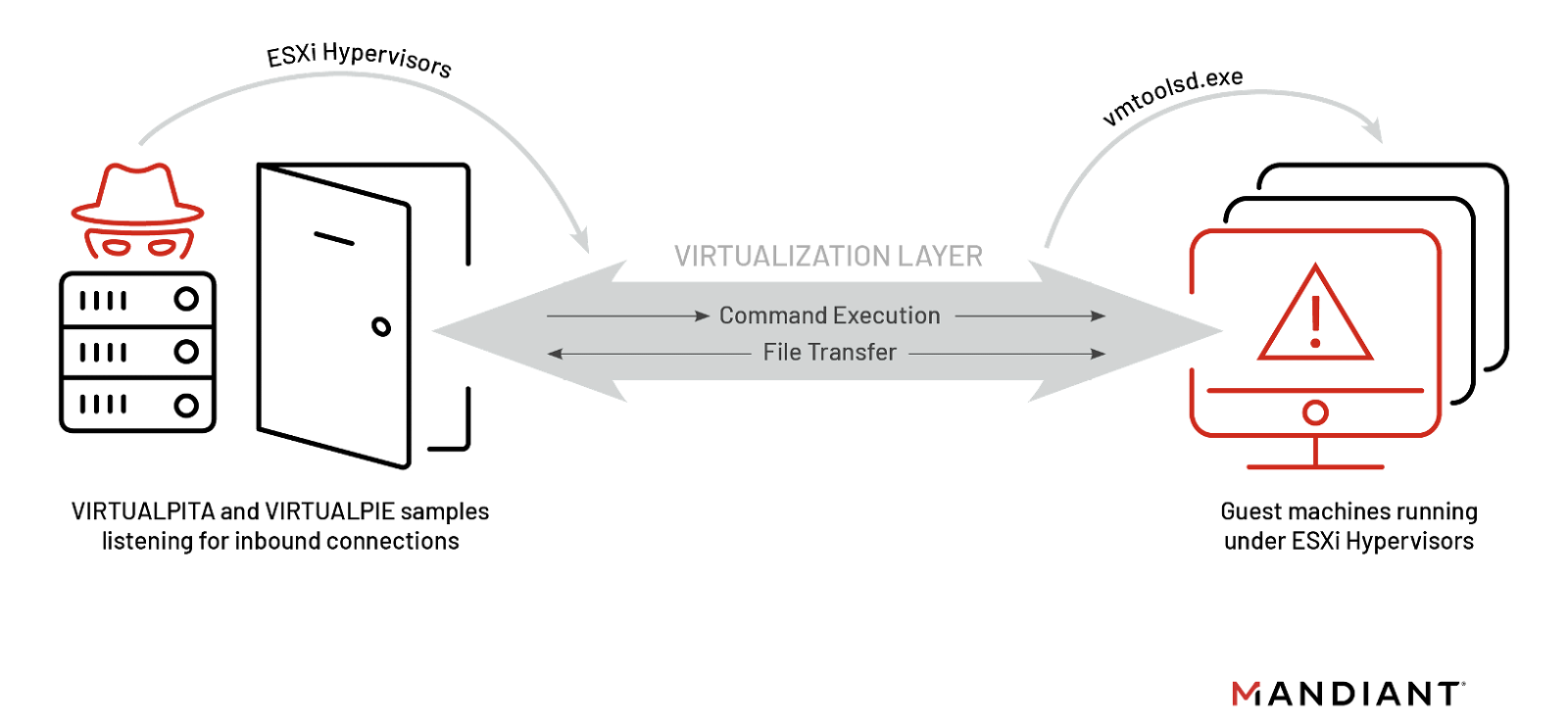
And because the malicious code targets the hypervisor of the physical machine and not the virtual machines, the hacker's ploy avoids almost all traditional security measures designed to monitor these target machines.
Mandiant consultant Alex Marvi says his company discovered the hackers earlier this year and disclosed their practices to VMware. The researchers report that they have seen the group perform virtualization hacking – a technique historically called hyperjacking – on around 10 victim networks across North America and Asia.
Mandiant says the hackers have not been identified as any known group, but appear to be linked to China.





